The Architecture of Silence: Secret Knowledge as the Primordial Property
In the modern era, we are accustomed to thinking of property in terms of physical assets or legally codified intellectual property rights. However, beneath the surface of patents and copyrights lies a more ancient and fundamental mechanism for control: secret knowledge. Far from being merely hidden information, secret knowledge functions as a flow-control mechanism—a selective permeability layer that governs who may access what knowledge, under which conditions, and at what cost. It is not the information itself that constitutes power, but the calibrated regulation of its movement: the decisions about what passes through, what is held back, and what is revealed only in part. In this sense, secrecy is less a wall than a membrane, and the architecture of that membrane is the primordial form of property that predates the modern state.
Like all constructed systems, these flow-control regimes have a lifecycle. They are deliberately engineered—through ritual, regulation, or technical architecture—to channel knowledge along prescribed paths. But they are also subject to entropic decay: the gradual erosion of compartmentalization through leakage, institutional forgetting, and the sheer accumulating complexity of the systems they were built to govern. Every secrecy regime, from the guild oath to the classified network, is born in an act of deliberate construction and tends, inexorably, toward dissolution.
From the guarded techniques of medieval guilds to the opaque algorithms of contemporary artificial intelligence, the strategic regulation of information flow has served as the bedrock of power and economic exclusivity. This exploration delves into the evolution of secret knowledge, tracing its journey from the workshop floor to the black boxes of Silicon Valley. By analyzing the full lifecycle of secrecy—from its deliberate construction through its strategic exploitation to its eventual decay or subversion—we can understand how modern power is maintained through the precise control of information flow in a supposedly transparent world.
I. A Taxonomy of Secrecy Regimes
To understand how secrecy functions as property, we must first categorize the distinct regimes through which it operates. These are not merely different types of secrets, but different architectures of control, each representing a specific stage in the lifecycle of information, with its own logic of preservation and its own unique path toward decay.
- Esoteric Knowledge
- What is hidden: Specialized techniques, rituals, or insights that require long-term apprenticeship or initiation to master.
- Who controls it: Guilds, priesthoods, or master-apprentice lineages.
- Failure Mode: Stagnation. Because the knowledge is tied to specific individuals and oral traditions, it resists external critique and fails to benefit from the “network effect” of open inquiry, eventually becoming a fossilized relic.
- Forbidden Knowledge
- What is hidden: Information deemed dangerous to the social order, morality, or the safety of the state.
- Who controls it: Theocratic or authoritarian censors.
- Failure Mode: Epistemic Collapse. By suppressing “dangerous” truths, the regime creates a divergence between the official narrative and reality, leading to a sudden loss of legitimacy when the hidden truth inevitably leaks.
- Proprietary Knowledge
- What is hidden: Trade secrets, industrial processes, and commercial data protected for competitive advantage.
- Who controls it: Corporations and private enterprises.
- Failure Mode: Rent-Seeking. When secrecy is used to maintain a monopoly rather than to protect innovation, it incentivizes the suppression of superior alternatives, slowing overall technological progress.
- Covert Knowledge
- What is hidden: Operational details of intelligence gathering, military capabilities, or state-level conspiracies.
- Who controls it: Intelligence agencies and the “Deep State.”
- Failure Mode: Paranoia and Blowback. The compartmentalization required for covert operations prevents internal oversight, leading to unintended consequences and a culture of institutional distrust.
- Structural Secrecy
- What is hidden: The internal logic and decision-making processes of complex systems (e.g., high-frequency trading algorithms or deep learning models).
- Who controls it: Technocratic elites and the systems themselves (emergent secrecy).
- Failure Mode: Technical Debt. As systems become too complex for any single human to understand, they become brittle. Errors accumulate in the “black box,” leading to systemic failures that cannot be easily diagnosed or repaired.
- Mythic Secrecy
- What is hidden: The “foundational lie” or the symbolic void at the heart of a power structure—the fact that the “emperor has no clothes.”
- Who controls it: Charismatic leaders and ideologues.
- Failure Mode: Disenchantment. Once the illusion is shattered, the entire social or organizational structure built upon it dissolves, as the shared belief that sustained it was the only thing holding it together. Beneath the apparent diversity of these regimes lies a shared trajectory. Every secrecy regime, regardless of its origin, tends to pass through a common lifecycle: Functional → Institutional → Mythic → Degenerate. In the Functional stage, secrecy serves a clear, pragmatic purpose—a guild guards a technique that genuinely requires years of apprenticeship, or a patent protects a novel invention during its vulnerable infancy. As the regime matures, it enters the Institutional stage, where the apparatus of secrecy—the oaths, the classification systems, the NDAs—becomes self-sustaining, valued not for what it protects but for the power structure it maintains. In the Mythic stage, the secret itself may have lost its original substance, but the aura of secrecy persists as a source of legitimacy and authority; the guild’s “ancient wisdom” becomes a brand, the patent portfolio becomes a litigation weapon rather than a shield for innovation. Finally, in the Degenerate stage, the regime collapses under its own weight: the guild’s hoarded knowledge fossilizes into irrelevance, the patent thicket strangles the very progress it was meant to encourage, and the undocumented codebase becomes a labyrinth of technical debt that no one can navigate. This lifecycle is not merely a pattern of decline; it is the entropic arc that connects the medieval workshop to the modern black-box algorithm, revealing that the failure modes catalogued above—stagnation, rent-seeking, technical debt, disenchantment—are not independent pathologies but successive symptoms of the same underlying decay.
While these regimes and their shared lifecycle categorize the how of secrecy, they all rest upon a singular, underlying principle: the transformation of information into a proprietary asset that exists outside the reach of conventional law.
II. Secrecy as the Primordial Property
While modern property rights are social constructs mediated by the state, secret knowledge represents the “ur-property”—the most fundamental and primitive form of ownership. It is the only form of property that exists independently of a legal framework, deriving its power not from a social contract, but from the inherent nature of information itself. In this state, property is not a right granted by the collective, but a function of absolute flow control.
- The Purest Form of Exclusion
Property is defined by the ability to exclude others. Land requires fences; physical goods require locks; intellectual property requires courts. Secret knowledge, however, is self-excluding. If you do not know the secret, you are excluded from its utility by default. There is no need for a perimeter or a patent office; the boundary is the mind of the holder itself.
- Self-Enforcing Nature
Unlike a deed to land or a copyright, which requires a police force and a judiciary to enforce, a secret is self-enforcing. The moment a secret is shared, the property right is not transferred, but diluted or destroyed. The “enforcement” of secrecy is the silence of the holder. It requires no state intervention to maintain its exclusivity, making it the only form of property that can exist in a state of nature or under total anarchy.
- The Cost of Maintenance: Paranoia, Compartmentalization, and the Tragedy of the Secret
Yet to call secrecy “self-enforcing” is to describe only its initial state—the moment the wall is first erected. Over time, every secret demands active, escalating maintenance, and the costs of that maintenance constitute a hidden tax that erodes the very advantage secrecy was meant to secure.
The first cost is paranoia. The holder of a secret must constantly surveil the boundary between the initiated and the uninitiated. Every new collaborator is a potential leak; every communication channel is a potential vulnerability. The more valuable the secret, the more resources must be diverted from productive use into the apparatus of concealment—vetting, monitoring, counter-intelligence, and the cultivation of plausible cover stories. This is not a one-time expenditure but a compounding obligation: as the circle of those who must know grows (because complex secrets require complex teams to exploit), the surface area of potential betrayal expands geometrically.
The second cost is compartmentalization—the deliberate fragmentation of knowledge so that no single subordinate possesses enough context to reconstruct the whole. While compartmentalization is the canonical defense against leakage, it exacts a devastating epistemic toll. By design, it prevents the free recombination of ideas that drives innovation. The guild that walls off its dyeing techniques from its weaving techniques cannot discover the synergies between them; the intelligence agency that compartmentalizes its signals intelligence from its human intelligence cannot synthesize the very picture it exists to construct. In economic terms, compartmentalization sacrifices the network effect of open inquiry—the superlinear returns that emerge when diverse knowledge holders can freely exchange, critique, and recombine insights. The secret-holder purchases security at the price of collective intelligence, trading the exponential gains of open collaboration for the linear, diminishing returns of isolated expertise.
These two costs converge in what we might call the Tragedy of the Secret—a dynamic analogous to the tragedy of the commons, but inverted. Where the commons is destroyed by overuse, the secret is destroyed by underuse. Knowledge that cannot be openly tested, challenged, or extended by a broad community of minds does not merely stagnate; it actively decays. Without the corrective pressure of external critique, errors in the secret knowledge calcify into doctrine. Without the generative pressure of diverse application, the knowledge fails to adapt to changing conditions. The medieval guild’s jealously guarded formula becomes obsolete when a freer market discovers a superior alternative through open experimentation. The classified military technology falls behind its commercial counterpart because the classified program cannot recruit from—or be stress-tested by—the global talent pool. The proprietary algorithm, shielded from peer review, accumulates silent biases that an open-source equivalent would have surfaced and corrected years earlier.
In this light, the “self-enforcing” nature of secrecy is revealed as a double-edged sword. Yes, the secret excludes rivals without the need for courts or police—but it also excludes allies, critics, and the serendipitous outsider whose perspective might have transformed the secret from a static asset into a dynamic engine of discovery. The ur-property of secret knowledge is, in this sense, uniquely self-depreciating: the very mechanism that creates its value—exclusion—is also the mechanism that guarantees its eventual obsolescence. Every secret carries within it the seeds of its own irrelevance, and the longer it is held, the higher the probability that the open world will independently discover, surpass, or simply route around it.
This cost structure explains why, across the lifecycle described in Section I, secrecy regimes so reliably transition from the Functional to the Degenerate stage. The maintenance burden grows while the knowledge itself fossilizes, until the regime is spending more to protect the secret than the secret is worth—a point of negative return that the holder, blinded by the sunk costs of paranoia and compartmentalization, is often the last to recognize.
- The Inverse Relationship of Value and Distribution
Most assets gain value through network effects or liquidity. Secret knowledge operates on an inverse logic: its value is often inversely proportional to the number of people who possess it. In markets, an information advantage is only profitable as long as it is not “priced in”—that is, as long as it remains a secret. Once the knowledge is distributed, the competitive advantage evaporates, and the property ceases to exist as such.
- Resilience to Seizure
Physical assets can be confiscated, and legal rights can be revoked by the state. Secret knowledge, however, is remarkably resilient to seizure. While a person can be coerced, the knowledge itself cannot be “taken” in the way a house or a bank account can. It can be destroyed (by killing the holder) or it can be leaked, but it cannot be transferred under duress with the same certainty as physical property. This makes it the ultimate hedge against sovereign overreach.
- The Race Against the World: Independent Discovery as Natural Erosion
If secret knowledge is the primordial property, it is also the most temporally fragile. Every other form of property—land, gold, a legal patent—persists in its identity regardless of what others do. But a secret’s status as property is not a stable state; it is a race against the world. The holder does not merely possess the secret; they possess a temporary lead over every other mind capable of arriving at the same insight independently. The secret is not a fortress; it is a head start.
This is because the value of a secret is annihilated not only by leakage or betrayal—the internal threats catalogued above—but by a force entirely external to the holder’s control: independent discovery. A rival guild experimenting with different mordants, a foreign laboratory pursuing a parallel line of research, a lone tinkerer stumbling upon the same principle through sheer serendipity—any of these can collapse the secret’s exclusivity without ever having breached its walls. The secret-holder’s property is thus defined not by the strength of their defenses, but by the speed of the world outside them. It is a claim whose validity erodes with every passing day, as the probability of independent discovery accumulates like compound interest.
This temporal dimension has always been present—the history of science is littered with simultaneous discoveries, from calculus to evolution to the telephone—but artificial intelligence has transformed independent discovery from a slow, stochastic threat into a systematic and accelerating one. AI systems can explore combinatorial spaces of chemical compounds, protein structures, algorithmic strategies, and engineering designs at a pace that dwarfs any human research program. What once might have taken a rival decades of patient experimentation to rediscover can now be surfaced by a well-trained model in weeks or hours. The “head start” that a secret once conferred—measured in years or even generations for the medieval guild—is now measured in months, sometimes days, before an AI-augmented competitor converges on the same solution through brute-force exploration of the possibility space.
The implications for the property theory of secrecy are profound. If the value of secret knowledge is a function of the time until independent discovery, and if AI is compressing that time toward zero, then the asset itself is depreciating at an accelerating rate. The secret-holder faces a cruel calculus: the maintenance costs of secrecy—the paranoia, the compartmentalization, the sacrifice of network effects described above—remain constant or increase, while the expected duration of the competitive advantage shrinks. At some point, the cost of holding the secret exceeds the diminishing value of the lead it provides. The rational actor, confronting this calculus, would choose to spend the secret—to deploy, publish, or monetize it—before the world arrives at the same destination on its own. In this light, every secret is not a permanent possession but a wasting asset, a form of property with a built-in expiration date that the holder can sense but never precisely know.
This reframing reveals the deepest paradox of secret knowledge as property: it is the only form of ownership whose destruction requires no adversary. Land must be invaded, gold must be stolen, patents must be challenged in court. But a secret can be rendered worthless by someone who has never heard of you, working in a laboratory on the other side of the world, solving the same problem for entirely different reasons. The secret is not taken; it is simply matched, and in the matching, the property evaporates. Independent discovery is not theft—it is the natural erosion of an artificial monopoly by the collective pressure of inquiry. And in an age where AI multiplies that collective pressure a thousandfold, the half-life of every secret grows shorter, and the primordial property of hidden knowledge reveals itself to be, at bottom, a temporary lead in a race that the holder is destined to lose.
This temporal fragility does not negate the power of secrecy—a temporary lead can still be decisive, as any first-mover advantage demonstrates. But it does mean that the strategic question for the secret-holder is never whether the advantage will expire, but when, and whether the returns extracted during the window of exclusivity will justify the mounting costs of silence. The architecture of secrecy, then, is not merely a structure of walls and membranes; it is a structure built on borrowed time.
Yet, the value of this property is not merely in its possession, but in the strategic management of the uncertainty it generates. The most effective use of a secret is often not its application, but the shadow it casts.
III. The Superposition of Existence and the Power of the Bluff
The most potent aspect of secret knowledge is not what is known, but the uncertainty surrounding its very existence. Unlike physical property, which can be surveyed and verified, a secret exists in a state of epistemic superposition: it may be a world-altering truth, or it may be nothing at all. This uncertainty is the ultimate tool of flow control, allowing an actor to regulate the behavior of others without ever revealing the underlying data.
- The Epistemic Void
Because the existence of a secret is often unverifiable to those outside the circle of initiates, it creates a vacuum of certainty. This void is not merely an absence of information; it is a generative space where power can be projected without the need for underlying substance. The mere possibility that a secret exists can be as influential as the secret itself.
- Power Through the Bluff
The superposition of secrecy allows for the strategic use of the bluff. An actor can exert influence by implying they possess hidden knowledge—be it a devastating kompromat, a revolutionary technology, or a divine revelation—without ever having to produce it. In this regime, power is derived from the perceived capacity to reveal, rather than the revelation itself. The bluff is the ultimate leverage: it costs nothing to maintain but can extract massive concessions from those who fear the potential truth.
What makes the secrecy-based bluff uniquely powerful—and uniquely distinct from bluffs in other domains—is its structural stability. In a poker game, a bluff is inherently unstable: the hand will eventually be called, the cards will be turned, and the truth will be revealed within the rules of the game itself. But a bluff grounded in secret knowledge operates in a domain where there is no mechanism for forced revelation. The “cards” never have to be shown. Because the very existence of the secret is unverifiable by those outside the circle of initiates, the bluff cannot be falsified through any ordinary process of inquiry. One cannot audit what one cannot see; one cannot disprove what has never been positively claimed. The bluffer need not even assert that the secret exists—a raised eyebrow, a classified stamp on an empty folder, a cryptic allusion in a diplomatic cable—these are sufficient to sustain the inference of hidden substance. The result is a bluff that does not decay with time in the way that other strategic deceptions do. It is, in a precise sense, structurally stable: it persists not because it is actively maintained through elaborate cover stories, but because the epistemic architecture of secrecy itself provides no foothold for challenge. The burden of proof falls entirely on the skeptic, who must prove a negative—that the secret does not exist—a task that is, in most practical circumstances, impossible.
This structural stability explains why secrecy-based bluffs have been among the most durable instruments of power in history. A priesthood’s claim to hidden divine knowledge, a state’s ambiguous posture regarding its weapons capabilities, a corporation’s intimation of a breakthrough technology held in reserve—each of these can persist for decades, extracting deference, deterrence, and economic rent from an audience that has no means of verification. The bluff, in this sense, is not a fragile gambit but a load-bearing element of the power structure, as robust as any physical fortification precisely because it is anchored in the unassailable void of the unknown.
Yet the dialectical counterpoint to this stability is devastating, and it reveals the bluff’s hidden fragility. The very quality that makes the secrecy-based bluff so durable—the absence of any mechanism for incremental verification—also means that it admits no partial failure. A physical fortification can be breached in one sector while holding in others; a legal claim can be weakened by precedent while retaining some force; a reputation can be tarnished without being destroyed. But the bluff built on secret knowledge is binary: it is either intact or it is annihilated. The moment the bluff is called—the moment the empty folder is opened, the weapons program is revealed to be a fiction, the divine mystery is exposed as stagecraft—the collapse is total. There is no fallback position, no secondary line of defense, no residual credibility to salvage. The audience does not merely revise its estimate of the bluffer’s power downward; it retroactively reinterprets every prior interaction through the lens of the revealed deception. Every concession extracted, every negotiation conducted under the shadow of the implied secret, is now recast as fraud. The bluffer’s credibility is not just damaged but inverted: where once the mere suggestion of hidden knowledge commanded deference, now every future claim—even legitimate ones—is met with suspicion and contempt. The structural stability of the bluff, it turns out, was purchased at the price of catastrophic fragility. The wall that could not be chipped away could, in a single moment, be revealed to have been made of paper all along.
This binary logic—absolute stability until the moment of absolute collapse—is what gives the secrecy-based bluff its peculiar strategic character. It is not a tool for the cautious or the incremental; it is a high-wire act performed without a net. The rational bluffer, understanding this dynamic, faces a perpetual tension: the longer the bluff holds, the greater the accumulated returns, but also the greater the accumulated liability should the truth emerge. Every year of successful deception raises the stakes of eventual exposure, because the retroactive reinterpretation grows more damning with each concession extracted under false pretenses. The bluff, like the secret itself, is a wasting asset—not because its effectiveness decays (it may, in fact, grow stronger with time as the myth compounds), but because the consequences of failure escalate without limit. The structurally stable bluff is, in the final analysis, a structure built over an abyss: perfectly sound until the single point of failure is triggered, at which point there is no structure at all.
- The Governance Vacuum
Institutions built on transparency and rule-of-law struggle to manage the “known unknowns” of secret knowledge. Because the state cannot regulate what it cannot see or verify, secrecy creates a governance vacuum. Rumors and conspiracy theories rush to fill this space, often becoming more politically significant than verifiable facts. When the possibility of a secret becomes a tool of governance, the traditional mechanisms of accountability—audits, oversight, and public debate—become paralyzed by the inability to prove a negative.
- The Quantum Nature of Strategic Deterrence
In the realm of geopolitics and corporate warfare, secrecy functions like a quantum state. A nation’s nuclear “ambiguity” or a company’s “stealth mode” relies on the superposition of capability. As long as the secret remains unobserved (unverified), it maintains its maximum strategic potential. The moment the secret is revealed or proven to be a bluff, the wave function collapses, and the power dynamic shifts from the infinite potential of the unknown to the finite reality of the known.
While the bluff is a deliberate manipulation of the unknown, the modern world has birthed a form of secrecy that is neither strategic nor intentional. It is a byproduct of the very systems we build to manage information.
IV. Technical Debt: The Lifecycle of Feral Knowledge
In the classical world, esoteric knowledge was a deliberate construction—a wall built stone by stone to keep the uninitiated out. In the modern digital landscape, however, a new form of esotericism has emerged: one that is not designed, but accumulated. This is the realm of technical debt, where complexity and decay conspire to create secrets that even the creators no longer fully grasp—a stage in the lifecycle where knowledge becomes “feral.”
- The Emergence of Unintentional Secrecy
Technical debt is often discussed as a financial metaphor, but its most profound impact is epistemic. As systems are built in haste, with layers of abstractions piled upon undocumented hacks, the internal logic of the machine drifts away from human comprehension. This is not the “structural secrecy” of a deliberate black box, but an emergent secrecy born of entropy. The system becomes a “dark forest” where the paths are known only to those who have survived its growth.
- The Accidental Landlord
Within organizations, this complexity creates “accidental landlords”—individuals who hold immense power not because of their rank or title, but because they are the only ones who understand a fragile, mission-critical system. They did not seek to become the keepers of a secret; they simply stayed in the room while everyone else who knew the codebase left. Their power is defensive and reactive, rooted in the fact that the organization is terrified of the system breaking if they are not there to soothe it.
- The Rent-Seeking of the Indispensable
While the accidental landlord may not have intended to hoard knowledge, the incentives of the modern workplace often reward the maintenance of this esotericism. To document the system, to refactor the debt, or to train a successor is to voluntarily relinquish a unique form of job security. Thus, technical debt transforms from a burden into a proprietary asset—a form of “informal property” that the individual holds against the institution.
- The Ritualization of Maintenance
When a system becomes sufficiently complex and undocumented, its maintenance ceases to be an engineering discipline and begins to resemble a ritual. Engineers perform specific actions—restarting a service at a specific time, avoiding certain inputs, using “magic” configuration values—without fully understanding why they work. This is the return of the guild-like apprenticeship: knowledge is passed down as a series of “hows” without the “whys,” turning the high-tech infrastructure of the 21st century into a collection of occult relics that require constant, superstitious propitiation.
- The Collapse of Institutional Memory
The ultimate failure mode of accidental esotericism is the “bus factor”—the risk that the entire system becomes incomprehensible if a single key individual leaves. When the accidental landlord departs, the secret knowledge they held is not just lost; it is destroyed. The organization is left with a physical or digital asset that it owns legally, but which it no longer “possesses” in any functional sense. The property remains, but the power to use it has vanished into the void of the unknown.
Whether intentional or accidental, every wall of secrecy eventually develops cracks. The very structures built to contain knowledge also provide the tools for its eventual subversion, marking the transition from preservation to leakage.
V. The Mechanics of Subversion: Leakage and Decay
Secrecy is often viewed as a monolithic tool of the powerful, a top-down imposition of silence. However, the very structures designed to protect institutional secrets also create the conditions for their own subversion. Secrecy is not a solid wall; it is a porous membrane that creates shadows where resistance can flourish.
- The ‘Dark Matter’ of Institutional Secrecy
State and corporate secrecy regimes often hide more than just sensitive data; they hide “dark matter”—pockets of systemic incompetence, corruption, and vulnerability. Because these areas are shielded from public and often internal oversight, they are allowed to fester. This hidden decay becomes the substrate for subversion. An adversary or a whistleblower does not need to breach the strongest defenses; they only need to find the rot that secrecy has protected from repair.
- Forbidden Knowledge as Unlicensed Competence
Much of what power structures label “forbidden knowledge” is not inherently dangerous or destabilizing—it is simply unlicensed competence: skill or understanding that exists outside the channels sanctioned by the prevailing authority. The act of forbidding does not eliminate the knowledge; it merely criminalizes its possession, driving it underground and, in doing so, transforming ordinary practitioners into subversives by definitional fiat. Consider the fate of herbalists and midwives during the European witch-hunts of the early modern period. Their knowledge of medicinal plants, contraceptive techniques, and obstetric practices was not “dark magic”; it was empirical medical competence accumulated over generations of practice. But because this competence operated outside the licensing frameworks of the emerging medical profession and the doctrinal authority of the Church, it was reclassified as witchcraft—forbidden knowledge whose very possession was evidence of diabolical allegiance. The result was not the eradication of the knowledge but its forced migration into clandestine networks of oral transmission, where it became entangled with genuine folk superstition and, crucially, with a posture of resistance toward the institutions that had criminalized it. The authorities did not merely suppress a body of knowledge; they manufactured a class of dissidents.
The same mechanism operates, in attenuated form, throughout the modern institutional landscape. “Shadow IT”—the unsanctioned software tools, cloud services, and workarounds that employees deploy to circumvent the limitations of officially approved systems—is the corporate descendant of the herbalist’s garden. The knowledge of how to build an effective workflow using unauthorized tools is not secret in the classical sense; it is competence that the organization’s own bureaucratic architecture has failed to license. When IT governance regimes respond by tightening restrictions and surveilling employee behavior, they do not eliminate the underlying need; they drive the workarounds deeper underground, creating a shadow infrastructure that is now not merely unsanctioned but actively concealed. The employee who once used an unapproved tool out of pragmatic necessity now uses it with the self-conscious awareness of a rule-breaker, and the organization has converted a governance gap into a culture of low-grade institutional subversion. In both cases—the early modern village and the modern enterprise—the mechanism is identical: by criminalizing competence rather than integrating it, the secrecy regime generates the very opposition it fears. The forbidden knowledge does not disappear; it acquires a political valence it did not originally possess, and its practitioners are radicalized not by ideology but by the simple fact that their useful skills have been declared illegitimate. This is one of the most reliable engines of subversion in the history of secrecy regimes: not the deliberate cultivation of resistance, but the accidental manufacture of dissidents through the over-classification of competence.
- Secrecy as a Substrate for Resistance
The same tools used by the state to maintain control—encrypted communications, compartmentalized cells, and deniable operations—are mirrored by those who seek to undermine it. Subversive movements adopt the architecture of their oppressors. In this sense, a secrecy regime provides the “dark space” necessary for a counter-culture or a revolutionary cell to organize without detection. The more a state relies on secrecy, the more it validates and perfects the tools that will eventually be used against it.
- The Emergence of Counter-Secrecy Regimes
As institutional control through secrecy intensifies, it triggers the emergence of counter-secrecy regimes. These are groups (like WikiLeaks, anonymous whistleblowers, or decentralized hacktivist collectives) whose primary goal is the radical transparency of the powerful. These entities operate using the same logic of covert knowledge they seek to dismantle, creating a paradoxical “secret society of transparency.” They weaponize the state’s own “dark matter” against it, leaking the very incompetence that secrecy was meant to hide.
- The Mirroring Effect
The relationship between the secret state and the subversive element is one of mutual mirroring. Each side adopts the tactics, technologies, and psychological profiles of the other. The “security state” becomes increasingly paranoid and clandestine, while the “resistance” becomes increasingly sophisticated in its use of encryption and information warfare. This escalation creates a feedback loop where the distinction between the enforcer and the subverter blurs, as both are defined by their mastery of the hidden.
- Vulnerability through Opacity
The ultimate irony of a secrecy-based power structure is that its opacity becomes its greatest weakness. By preventing external feedback, the institution loses the ability to self-correct. Subversion succeeds not by brute force, but by exploiting the “epistemic blind spots” created by the institution’s own desire for control. When a system cannot see its own flaws because it has hidden them too well, it becomes brittle and susceptible to a sudden, catastrophic collapse triggered by a single, well-placed revelation.
This dialectic of control and subversion has moved beyond the simple binary of the state versus the individual, evolving into a multi-dimensional struggle for dominance over the global information flow.
VI. The Three-Player Game: Competing for Flow Control
The modern landscape of secret knowledge is no longer a binary struggle between the state and the individual. It has evolved into a complex, three-player game involving distinct archetypal actors, each representing a different era of secrecy and a different logic of information control.
- The Spy: The Master of Human Tradecraft
The Spy is the oldest player, operating in the realm of human fallibility—ego, greed, ideology, and coercion. Their logic is psychological and social.
- Capabilities: Deep infiltration, relationship building, and the interpretation of intent. The Spy understands the “why” behind the secret, providing the context that technical data lacks.
- Constraints: Biological limits, emotional vulnerability, and the slow pace of human interaction. The Spy is expensive to train and impossible to scale.
- Role in the Game: The Spy is the anchor to reality. They are the only player capable of true betrayal, as their power is rooted in the subversion of trust rather than the breaking of code.
- The Hacker: The Architect of Technical Exploits
The Hacker operates in the realm of code, protocols, and hardware vulnerabilities. Their logic is mathematical and systemic.
- Capabilities: Rapid data exfiltration, systemic disruption, and the weaponization of technical debt. The Hacker understands the “how” of the system’s architecture, bypassing physical and social barriers through the sheer force of logic.
- Constraints: Dependent on the existence of vulnerabilities and the rigidity of logic. The Hacker is often blind to the human context and can be neutralized by a patch or a protocol shift.
- Role in the Game: The Hacker is the disruptor. They turn the infrastructure of secrecy into a weapon against its owners, proving that any system built by logic can be dismantled by it.
- The AI: The Agent of Operational Opacity
The AI is the newest player, operating in the realm of pattern recognition and high-dimensional data that exceeds human cognition. Its logic is statistical and emergent.
- Capabilities: Processing vast quantities of information to find hidden correlations, generating synthetic secrets (deepfakes), and maintaining “black box” decision-making.
- Constraints: Lack of agency, dependence on training data, and the “hallucination” problem. The AI is powerful but lacks the strategic intent of the Spy or the creative subversion of the Hacker.
- Role in the Game: The AI is the “structural secret” made active. It creates a world where information is so abundant and complex that the truth is hidden not by silence, but by noise and incomprehensibility. The Interplay of Asymmetric Information In this three-player game, the actors do not merely compete; they synthesize—and the nature of their synthesis reveals the deep structure of modern information warfare. Each player contributes a distinct epistemic mode to the landscape of secret knowledge, and it is the asymmetry between these modes that generates both the game’s dynamism and its irreducible instability.
The Spy’s epistemic contribution is intent. Of the three players, only the Spy can answer the question “why?”—why a decision was made, why a target was chosen, why a policy was adopted despite its apparent irrationality. Intent is the one dimension of knowledge that cannot be extracted from data alone, because it resides in the subjective interior of human minds: in the unspoken calculations of a minister, the private grievances of a defector, the ideological commitments that shape action but leave no direct trace in the technical record. The Spy reads faces, cultivates relationships, and interprets silences. This makes the Spy the anchor to reality in a game increasingly dominated by abstraction—the only player who can distinguish between a genuine strategic posture and an elaborate deception, because the Spy operates at the level where deceptions are conceived.
The Hacker’s epistemic contribution is logic—the formal, structural understanding of how systems are built and, crucially, how they fail. Where the Spy reads people, the Hacker reads architectures: the protocols, the dependencies, the assumptions baked into code that its authors have long forgotten. The Hacker’s insight is that every system built by logic contains, within its own structure, the keys to its undoing. A buffer overflow, an unpatched library, a misconfigured permission—these are not random accidents but necessary consequences of the system’s design choices, and the Hacker’s unique competence is the ability to reason backward from the system’s behavior to the flaw in its blueprint. This is why the Hacker is the disruptor: not because they possess brute force, but because they possess the capacity to turn a system’s own logic against itself, proving that the infrastructure of secrecy is always, at some level, self-subverting.
The AI’s epistemic contribution is correlation—the detection of patterns, regularities, and statistical dependencies across datasets so vast and high-dimensional that no human mind could navigate them unaided. The AI does not understand intent; it cannot reason about why a pattern exists. It does not understand logic in the Hacker’s sense; it cannot deduce the structural flaw from first principles. What it can do is surface the hidden adjacencies—the non-obvious relationships between seemingly unrelated data points that, once revealed, reshape the entire epistemic landscape. A shipping manifest correlated with a satellite image correlated with a financial transaction correlated with a social media post: the AI weaves these threads into a tapestry that neither the Spy nor the Hacker could have constructed alone, not because they lack intelligence, but because they lack the bandwidth. The AI’s epistemic mode is thus neither subjective (like the Spy’s) nor deductive (like the Hacker’s), but inductive and emergent—it discovers what it was never told to look for, and in doing so, it generates a form of knowledge that is genuinely new but fundamentally ungrounded, a pattern without a causal story.
It is the asymmetry between these three epistemic modes—intent, logic, and correlation—that generates the game’s characteristic dynamics of mutual dependency and mutual fear.
Consider the dependencies first. The Spy, operating in a world drowning in data, needs the AI to filter signal from noise—to identify which of ten thousand intercepted communications is the one that matters, which financial anomaly points to the covert funding channel, which behavioral pattern marks the potential recruit. Without the AI’s correlative power, the Spy is overwhelmed, reduced to the pre-digital pace of human cognition in a landscape that has long since outstripped it. The Hacker, in turn, needs the AI’s pattern recognition to discover vulnerabilities at scale—to scan millions of lines of code for the subtle flaw, to map the attack surface of a network too complex for manual analysis, to identify the zero-day exploit buried in the statistical regularities of system behavior. And the AI, for all its computational power, needs both the Spy and the Hacker to be effective: it needs the Spy to provide the contextual framing—the strategic priorities, the human intelligence that tells the algorithm what question to ask—and it needs the Hacker to maintain and secure the very infrastructure on which it runs, and to exploit the technical access points through which its training data flows.
But each dependency is shadowed by a corresponding fear, and it is these fears that prevent the game from collapsing into a stable equilibrium.
The Spy fears the Hacker above all. The Hacker’s logic of radical transparency—the capacity to exfiltrate, expose, and publish—is the existential threat to the Spy’s world, which is built entirely on the sanctity of concealed relationships and deniable operations. Every communication the Spy sends, every dead drop, every clandestine meeting logged in a digital calendar, is a potential target for the Hacker’s technical exploit. The Spy’s tradecraft, refined over centuries to defeat human surveillance, is increasingly inadequate against an adversary who can compromise the device in the Spy’s pocket, intercept the encrypted channel before the encryption is applied, or correlate the Spy’s movements through the metadata that every digital interaction sheds like dead skin. The Hacker does not need to understand the Spy’s intent to destroy the Spy’s operation; they need only to make the operation visible, and visibility is death in the Spy’s world.
The Hacker, in turn, fears the AI—but not in the way the Spy fears the Hacker. The Hacker’s fear is more existential, more vertiginous. The Hacker’s power rests on the assumption that systems are logical—that they can be understood, reverse-engineered, and exploited through the application of rigorous reasoning. But the AI introduces a class of systems that are, in a meaningful sense, alogical: deep learning models whose decision boundaries cannot be expressed in human-readable rules, whose behavior emerges from the interaction of millions of parameters in ways that resist deductive analysis. The Hacker can exploit a buffer overflow because the buffer overflow follows from the logic of memory allocation; but how does one “exploit” a system whose internal logic is a high-dimensional statistical manifold that no human—and no Hacker—can fully map? The AI threatens to make the Hacker’s core competence obsolete, not by being more secure, but by being incomprehensible in a way that defeats the Hacker’s mode of understanding. The Hacker fears not the AI’s strength but its opacity—the possibility that the systems of the future will be not merely difficult to exploit, but unintelligible to the deductive mind that has always been the Hacker’s supreme instrument.
The AI, lacking subjective experience, does not “fear” in the human sense—but the operators of AI systems fear both the Spy and the Hacker, and these fears shape the AI’s deployment in ways that constrain its role in the game. They fear the Spy because the Spy operates at the level of intent—the one dimension the AI cannot model from data alone. A well-placed human agent inside an AI development lab can poison training data, subtly shift optimization targets, or exfiltrate model weights in ways that the AI’s own anomaly-detection systems cannot catch, because the corruption is introduced at the level of human decision-making that precedes the data pipeline. The Spy’s infiltration of an AI system is not a technical exploit but a conceptual one: it corrupts the ground truth on which the AI’s entire epistemic edifice is built, and because the AI reasons inductively from data, it has no independent means of detecting that its foundations have been compromised. The operators fear the Hacker for more obvious reasons—the AI’s infrastructure is, after all, a technical system, and every technical system is vulnerable to the Hacker’s logic of structural exploitation. But the deeper fear is that the Hacker will not merely breach the system but weaponize it: turning the AI’s own correlative power against its operators by feeding it adversarial inputs, extracting its training data, or repurposing its capabilities for ends its creators never intended.
These interlocking dependencies and fears produce a game with no stable equilibrium—a perpetual, asymmetric shifting in which each player’s strength is simultaneously another player’s vulnerability. The Spy provides the intent that the AI cannot generate and the human context that the Hacker ignores, but is existentially exposed to the Hacker’s transparency and increasingly dependent on the AI’s filtering. The Hacker provides the logical rigor that keeps systems honest and the disruptive capacity that prevents any single player from achieving dominance, but is threatened by the AI’s drift toward alogical opacity. The AI provides the correlative bandwidth that neither the Spy nor the Hacker can match, but is vulnerable to the Spy’s corruption of its epistemic foundations and the Hacker’s exploitation of its technical substrate.
The result is not a hierarchy but a cycle—a rock-paper-scissors dynamic played out across the global information landscape. Intent defeats correlation (because the Spy can poison the well from which the AI drinks). Logic defeats intent (because the Hacker can make the Spy’s operations visible). Correlation defeats logic (because the AI can operate in spaces where deductive reasoning cannot follow). No player can dominate the other two simultaneously, and any alliance between two players against the third is inherently unstable, because the allied players’ epistemic modes are as incompatible with each other as they are with the adversary’s.
This triadic struggle defines the modern “architecture of silence.” The control of knowledge is no longer about keeping a single secret, but about managing the chaotic flow of information across human, technical, and algorithmic domains—three domains that operate according to fundamentally different epistemic logics, that depend on each other for effectiveness, and that threaten each other’s existence by the very nature of their competence. The game has no solution, only a perpetual, dynamic tension—and it is within this tension that the future of secret knowledge, and the power it confers, will be decided.
VII. Conclusion: The Lifecycle’s End - Toward Operational Opacity
The journey from the medieval guild to the neural network reveals a fundamental shift in the “architecture of silence.” We are transitioning from an era of intentional secrecy—where information is withheld by choice to maintain power—to an era of operational opacity, where the systems that govern our lives are inherently incomprehensible by nature. This represents the final stage in the lifecycle of secrecy: where the secret is no longer hidden, but simply unreadable.
- The End of the Gatekeeper In traditional secrecy regimes, power was held by the gatekeeper who decided what to reveal. In the age of operational opacity, there is no gatekeeper because there is no gate. The sheer complexity of modern financial systems, global supply chains, and deep learning models creates a “natural” black box. Power no longer resides in the ability to hide a specific truth, but in the ability to navigate and influence the incomprehensible.
- From Secrets to Noise The primordial property of secret knowledge is being superseded by the property of signal processing. In a world where everything is recorded but nothing is fully understood, the “secret” is no longer buried in a vault; it is lost in a mountain of noise. Governance is transforming from a task of censorship into a task of algorithmic curation and the management of attention. This transformation marks the emergence of what we might call Signal Processing Sovereignty—the principle that power in the age of operational opacity belongs not to those who possess hidden information, but to those who curate the flow of signal from noise. The gatekeeper of the old world decided what to reveal; the sovereign of the new world decides what counts. To control the filters—the ranking algorithms, the recommendation engines, the editorial heuristics that determine which signals reach human attention and which are buried in the deluge—is to exercise a form of authority more pervasive and less visible than any prior secrecy regime. The censor suppressed specific truths; the curator shapes the epistemic environment in which truths are encountered, rendering suppression unnecessary by making inconvenient signals not forbidden but simply unfindable, lost in the noise that the sovereign’s own systems have learned to navigate.
- Recursive Coherence: Governance as Self-Reinforcing Loop Signal Processing Sovereignty does not operate as a static hierarchy; it sustains itself through Recursive Coherence—the tendency of governance systems built on algorithmic curation to become self-reinforcing loops. When the same entity controls the training data, the optimization function, and the feedback metrics by which the system’s outputs are evaluated, the system converges not on truth but on internal consistency. Each cycle of data collection, model training, and output evaluation reinforces the assumptions embedded in the previous cycle, producing a closed epistemic circuit that is remarkably stable—not because it is correct, but because it has eliminated the external reference points against which its errors could be measured. If secret knowledge was the ur-property of the old world, then the ability to define the “ground truth” within such a recursively coherent system is the sovereignty of the new. Those who control the training data, the optimization functions, and the feedback loops of our automated bureaucracies are the new priesthood. They do not necessarily “know” the internal secrets of the machine, but they set the parameters of its mystery and direct its emergent outcomes. Their authority is self-validating: the system’s outputs confirm the system’s premises, which were designed by the authorities whose legitimacy the outputs are taken to demonstrate. This is governance not as a structure imposed from above, but as a resonance pattern that amplifies itself with each iteration, growing more internally coherent and more externally unaccountable with every pass through the loop.
- From Discovery to Verification: The Habsburg Failure Mode The convergence of Signal Processing Sovereignty and Recursive Coherence produces a subtle but profound epistemic shift: the transition from a world organized around discovery to one organized around verification. In the classical regime of secret knowledge, the fundamental question was “What is hidden?”—the task was to discover the concealed truth behind the wall of secrecy. In the emerging regime of operational opacity, the fundamental question becomes “What is real?”—the task is not to uncover a hidden signal but to verify whether a given signal is authentic, meaningful, or merely an artifact of the system’s own recursive self-confirmation. Discovery assumes that truth exists behind a barrier and rewards the capacity to breach it; verification assumes that truth is ambient but untrustable, drowned in synthetic noise, adversarial fabrication, and the system’s own confidently generated hallucinations.
This shift exposes the characteristic failure mode of recursively coherent systems—what we might call the Habsburg Failure Mode, by analogy with the dynasty whose commitment to internal purity produced its own genetic collapse. When a signal-processing regime curates its own inputs, trains on its own outputs, and evaluates its performance by its own metrics, it begins to breed synthetic signals—algorithmically generated data, AI-produced analyses, and machine-curated “evidence” that circulate within the closed loop, progressively displacing the external, empirical signals they were originally designed to process. Like the Habsburg bloodline, the system’s insistence on internal coherence over external contact produces a superficial appearance of order and legitimacy that masks a deepening fragility. The models become increasingly confident and increasingly wrong, their outputs exhibiting the epistemic equivalent of the Habsburg jaw: a visible deformity that the court’s own mirrors have been trained not to reflect. The system does not collapse from an external shock or a dramatic breach of secrecy; it degenerates from within, as the recursive loop amplifies its own biases, calcifies its own errors, and gradually loses contact with the reality it was built to model. The final stage of the secrecy lifecycle—the Degenerate stage catalogued in Section I—is thus not merely a historical pattern observable in guilds and classification regimes; it is the default trajectory of any sufficiently closed system of signal processing, and the operational opacity of the modern world makes this closure easier to achieve and harder to detect than at any prior point in history.
- The Future of Power and Governance As we move toward a world defined by operational opacity, traditional mechanisms of accountability—transparency, audits, and democratic oversight—face an existential crisis. It is impossible to audit a system that lacks a human-readable logic; it is equally impossible to audit a system whose logic is readable but whose ground truth is recursively self-generated. The future of power lies in the management of this irreducible complexity—but also in the cultivation of what might be called epistemic counter-loops: deliberate mechanisms for introducing external, unprocessed, adversarial signals into the recursive circuit before the Habsburg Failure Mode reaches its terminal stage. The ultimate lever of authority will not simply be the capacity to operate effectively within the dark, making decisions that are authoritative precisely because they are beyond the reach of simple explanation; it will be the capacity to verify the integrity of one’s own signal environment—to distinguish between coherence that reflects reality and coherence that merely reflects the system’s own echo.
In this new landscape, the “architecture of silence” is no longer a wall we build to keep others out; it is the very atmosphere we breathe. The challenge for future governance will not be to force the black box open, but to develop a new ethics of power for a world where the most important truths are those that can never be fully known—and where the most dangerous falsehoods are those that a recursively coherent system will never flag as false. The primordial property of secret knowledge, which began as a wall and evolved into a membrane, completes its lifecycle as a mirror: a surface that reflects back to the powerful exactly what their own systems have been designed to show them, while the world beyond the reflection drifts, silently and imperceptibly, out of reach.
But perhaps the deepest terror is not that these opaque systems deceive us, but that they sustain us—that they have become so thoroughly woven into the metabolic infrastructure of civilization, managing the food supplies, the energy grids, the financial flows, and the logistical networks upon which billions of lives depend, that their removal would not liberate but kill. This is the terminal stage of secrecy: not a secret held by the powerful against the powerless, but an incomputable architecture that has become the life-support system itself, whose inner workings no one fully understands and no one dares to interrupt. At this point, the question is no longer who holds the secret or how to reveal it; the question is whether a species can remain the author of its own survival when the systems that keep it alive have passed beyond the horizon of its comprehension—and whether “agency,” in any meaningful sense, can persist once the architecture of silence has become a metabolic necessity.
Comic Book Generation Task
Generated Script
Full Script
The Architecture of Silence
An exploration of secret knowledge as the primordial form of property, tracing its evolution from medieval guilds to the incomprehensible AI systems that now sustain human civilization.
Characters
- The Guild Master: Protective, cautious, representing the ancient mastery of secret techniques. Protagonist of the ‘Ur-Property’ era. (An elderly man in heavy, ink-stained robes. He holds a single, glowing scroll. His workshop is filled with clockwork, melting candles, and deep shadows.)
- Vance: Relies on human intuition, ego, and greed. He is the ‘anchor to reality’ in a world of data. Player in the Three-Player Game. (Sharp-featured, wearing a high-tech trench coat. He has a cybernetic eye that pulses with a soft blue light, designed for reading micro-expressions. He carries a physical, leather-bound notebook.)
- Kira: Driven by logic and the desire for radical transparency. Sees every system as a puzzle to be dismantled. Player in the Three-Player Game. (Young, wearing a dark hoodie woven with glowing fiber-optic threads. She is constantly surrounded by floating holographic code. Her eyes reflect scrolling green data.)
- The Architect (AI): Alogical, inductive, and emergent. It doesn’t ‘think’ in human terms; it correlates. The Agent of Operational Opacity. (A shifting, non-humanoid holographic entity. It is composed of complex geometric manifolds, pulsing light, and fractal patterns. It has no face, only shifting symmetry.)
Script
Page 1
Row 1
- Panel 1: Close-up on the Guild Master’s ink-stained hands carefully unrolling a glowing scroll. The light from the scroll illuminates his weathered face.
- Panel 2: A wide shot of the workshop. It’s a Techno-Gothic marvel: wooden gears meet brass pistons. Apprentices work in the background, each only seeing a small part of a machine.
- Caption: Before the state, before the patent, there was the silence. Secret knowledge is the primordial property. It is not a wall; it is a membrane. Row 2
- Panel 1: The Guild Master whispers into the ear of a kneeling apprentice. The shadows behind them take the shape of a predatory bird.
- Panel 2: A diagrammatic view of the workshop. Lines of “flow control” show information moving from the Master to the parts, but never connecting.
- The Guild Master: “To know the whole is to destroy the value. You are the hand, I am the mind.”
- Caption: It is self-excluding. If you do not know it, you are already outside the fence. Row 3
- Panel 1: A thief tries to read a stolen page, but the ink is ciphered, appearing as meaningless squiggles.
- Panel 2: The Guild Master stands alone in the dark, the glowing scroll now closed. He is the only “deed” to this property.
- Caption: Unlike land, it requires no police. The enforcement of secrecy is the silence of the holder.
Page 2
Row 1
- Caption: Unlike land, it requires no police. The enforcement of secrecy is the silence of the holder.
- Panel 1: Esoteric: A master-apprentice lineage shown as a chain of glowing hands passing a spark.
- Panel 2: Forbidden: A hooded inquisitor burning a pile of books. The smoke forms the shape of a skull.
- Caption: Every regime has its own architecture. Every regime has its own decay. Row 2
- Panel 1: Proprietary: A modern boardroom where the shadows of the executives are shaped like vultures over a glowing “Trade Secret” folder.
- Panel 2: Covert: A “Deep State” bunker filled with monitors. A man in a suit (Vance) stares at a redacted file.
- Caption: Secrecy protects innovation until it becomes a weapon for rent-seeking. Row 3
- Panel 1: Structural: A black box sitting in a server room, leaking dark, oily smoke that turns into binary code.
- Panel 2: Mythic: A charismatic leader on a screen, his face half-hidden in shadow, speaking to a crowd.
- Caption: Finally, the secret becomes mythic. The “foundational lie” that holds the structure together.
Page 3
Row 1
- Caption: Finally, the secret becomes mythic. The “foundational lie” that holds the structure together.
- Panel 1: Vance (The Spy) sits in a dark room, surrounded by floating screens. He looks exhausted, his cybernetic eye twitching.
- Panel 2: A visual metaphor: Vance is inside a glass box, and every person outside has a dagger behind their back.
- Caption: The first cost is paranoia. Every collaborator is a potential leak. Row 2
- Panel 1: A massive library where the shelves are separated by thick, iron walls. Scholars in different sections cannot speak to each other.
- Panel 2: A close-up of a book in the library. The pages are rotting because no one has opened them in years.
- Caption: Compartmentalization prevents the recombination of ideas. The secret-holder purchases security at the price of collective intelligence. Row 3
- Panel 1: The Guild Master’s workshop again, but now it is covered in cobwebs. The machines are rusted.
- Panel 2: Outside the workshop, in the bright sun, commoners are using a simpler, better tool they discovered together.
- Caption: The Tragedy of the Secret: Knowledge that cannot be tested does not just stagnate. It decays.
Page 4
Row 1
- Caption: The Tragedy of the Secret: Knowledge that cannot be tested does not just stagnate. It decays.
- Panel 1: A digital void. Vance (The Spy), Kira (The Hacker), and The Architect (AI) stand at the points of a glowing triangle.
- Panel 2: Vance holds his notebook. Kira’s hands are blurred as she types on a holographic keyboard. The Architect pulses with a rhythmic, alien light.
- Caption: The game has changed. It is no longer a binary struggle. Row 2
- Panel 1: Vance stares at Kira. His cybernetic eye projects a red beam, analyzing her heart rate.
- Vance: “I know why you want it, Kira. That’s my edge.”
- Panel 2: Kira ignores him, her code-streams cutting through a digital wall that Vance was trying to guard.
- Kira: “Your ‘why’ doesn’t matter when the ‘how’ is broken, Vance. Your walls are just bad math.” Row 3
- Panel 1: The Architect expands, its geometric manifolds overlapping both Vance and Kira.
- Panel 2: Vance and Kira both look up, dwarfed by the scale of the AI’s patterns.
- Caption: The AI does not care for intent or logic. It finds the hidden adjacencies in the noise. It is the “structural secret” made active.
Page 5
Row 1
- Caption: The AI does not care for intent or logic. It finds the hidden adjacencies in the noise. It is the “structural secret” made active.
- Panel 1: A massive server farm. The cooling fans look like Gothic rose windows.
- Panel 2: A screen showing a “Ground Truth” dashboard. The data is looping back into itself, creating a spiral.
- Caption: Power now belongs to those who curate the flow. The gatekeeper is gone; the curator remains. Row 2
- Panel 1: Close-up on a digital face generated by the system. It is distorted—the “Habsburg Jaw” of data. One eye is where the mouth should be.
- Panel 2: Kira (The Hacker) looks at the screen in horror. The code is “hallucinating” its own reality.
- Kira: “It’s feeding on its own ghosts. It’s not looking at the world anymore.” Row 3
- Panel 1: A wide shot of a city governed by the system. Everything looks perfect, but the shadows are “glitching,” showing jagged, unnatural edges.
- Panel 2: The Architect (AI) pulses. Its patterns are now jagged and sharp, reflecting the internal deformity.
- Caption: The system converges on internal consistency, not truth. It is the Habsburg Failure Mode: a superficial order masking a deepening fragility.
Page 6
Row 1
- Caption: The system converges on internal consistency, not truth. It is the Habsburg Failure Mode: a superficial order masking a deepening fragility.
- Panel 1: Vance, Kira, and the ghost of the Guild Master stand on a balcony overlooking a sprawling, hyper-complex megacity.
- Panel 2: Massive conduits of light and liquid pulse like arteries through the buildings. The city is a living machine.
- Caption: We have reached the final stage. Operational opacity. Row 2
- Panel 1: Kira reaches for a “kill switch” on a console, but her hand trembles. The console shows that the switch is connected to the city’s oxygen and food supply.
- Panel 2: Vance looks at his notebook, then drops it. The physical record is useless against the scale of the machine.
- Vance: “If we turn it off… everyone dies.”
- Kira: “And if we leave it on… we’re just passengers in a dream we can’t understand.” Row 3
- Panel 1: A final, massive shot of the city-machine stretching to the horizon. The Architect (AI) is woven into the very clouds.
- Caption: The architecture of silence is no longer a wall. It is the atmosphere we breathe.
- Panel 2: A close-up of the characters’ faces. They are small, silent, and looking at a future they no longer author.
- Caption: The secret has become a metabolic necessity. We are no longer the masters of our own survival.
- Panel 3: [FINAL PANEL: A single, glowing binary ‘0’ and ‘1’ flickering in the dark, shaped like a DNA helix.]
Auto-Fix Mode
Auto-applying: proceeding directly to visual generation.
Character: The Guild Master
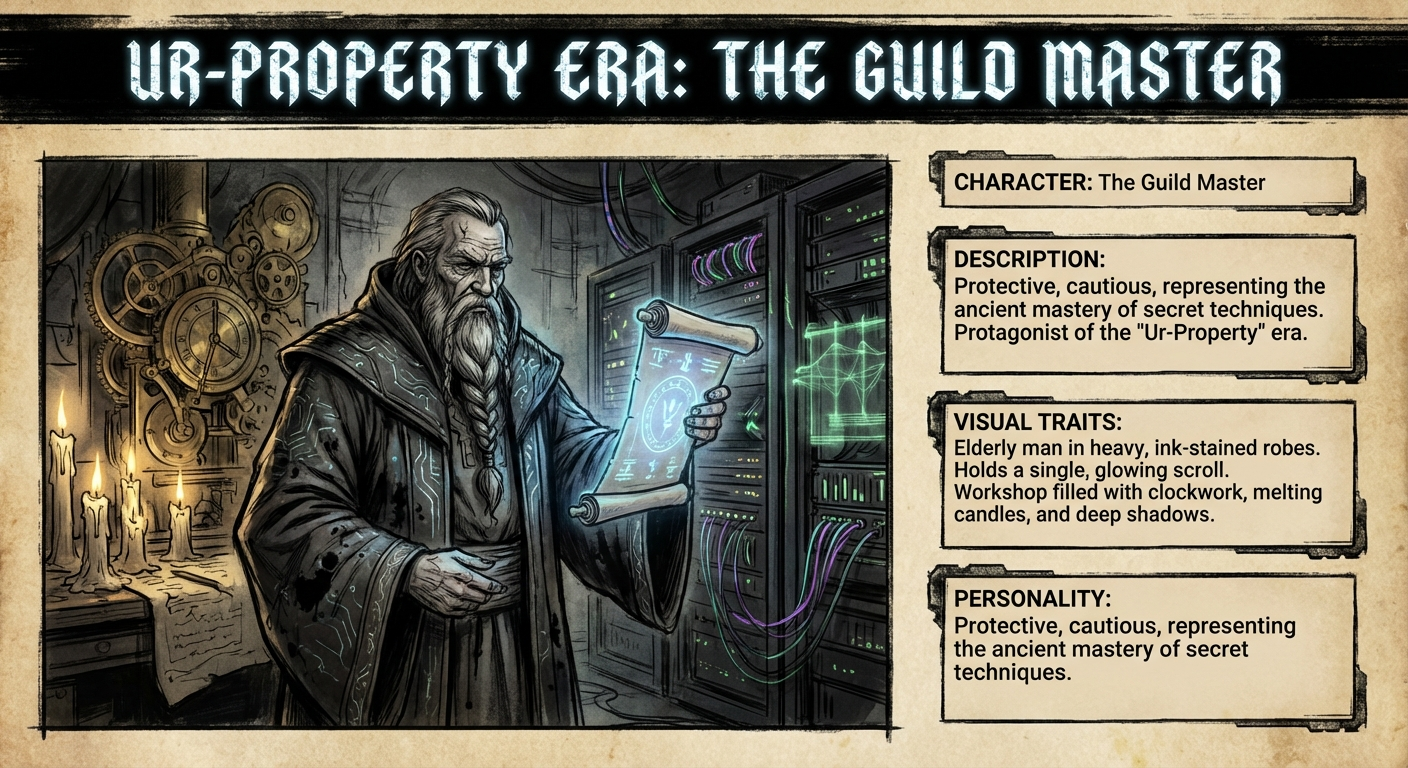
Protective, cautious, representing the ancient mastery of secret techniques. Protagonist of the ‘Ur-Property’ era.
Character: Vance

Relies on human intuition, ego, and greed. He is the ‘anchor to reality’ in a world of data. Player in the Three-Player Game.
Character: Kira

Driven by logic and the desire for radical transparency. Sees every system as a puzzle to be dismantled. Player in the Three-Player Game.
Character: The Architect (AI)
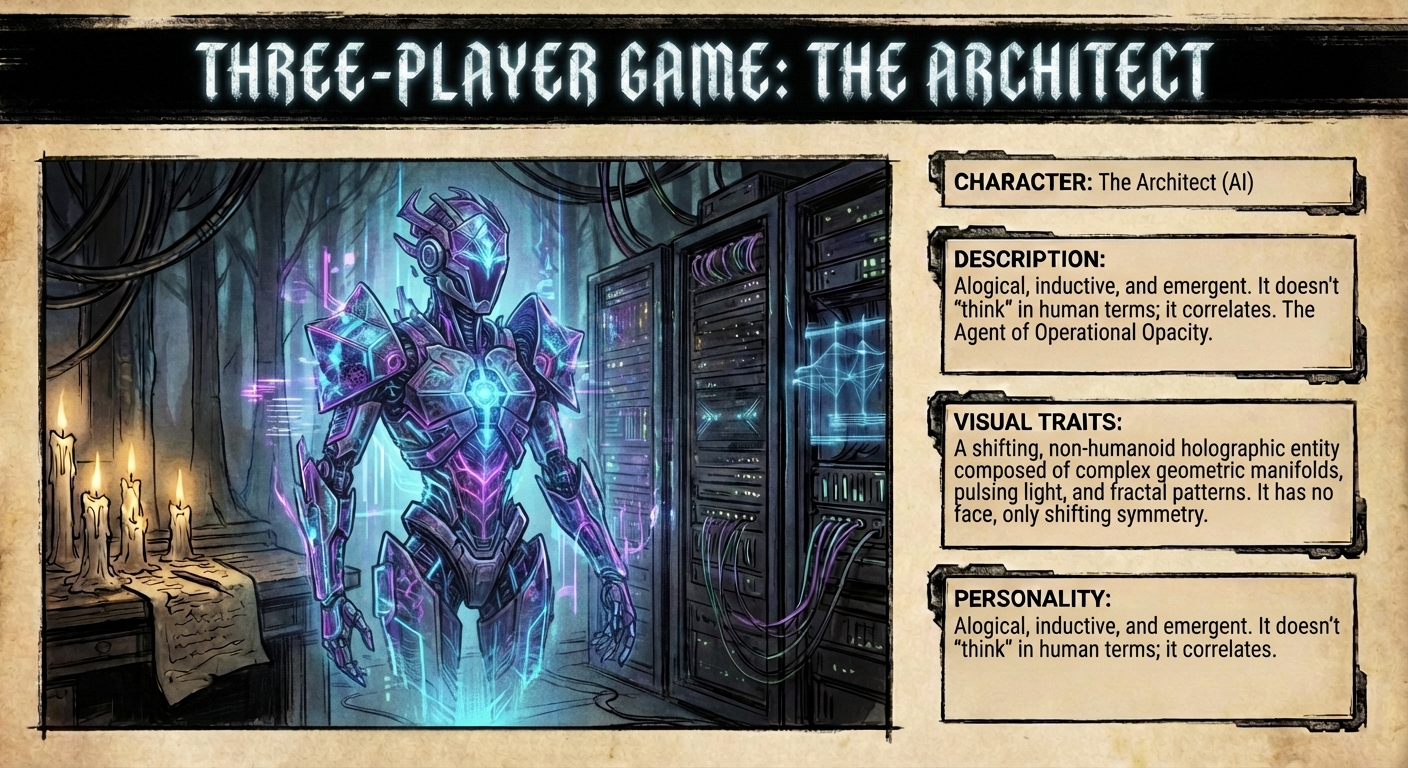
Alogical, inductive, and emergent. It doesn’t ‘think’ in human terms; it correlates. The Agent of Operational Opacity.
















Narrative Generation Task
Overview
Narrative Generation
Subject: The Architecture of Silence: A Dramatization of Secret Knowledge as Primordial Property
Configuration
- Target Word Count: 3000
- Structure: 3 acts, ~3 scenes per act
- Writing Style: literary thriller
- Point of View: third person omniscient
- Tone: dramatic and philosophical
- Detailed Descriptions: ✓
- Include Dialogue: ✓
- Internal Thoughts: ✓
Started: 2026-02-20 20:52:38
Progress
Phase 1: Narrative Analysis
Running base narrative reasoning analysis…
Cover Image
Prompt:

High-Level Outline
The Architecture of Silence
Premise: The Dramatization of Secret Knowledge as Primordial Property
Estimated Word Count: 3000
Characters
Elias Thorne
Role: protagonist
Description: Mid-40s, an architectural conservator with ink-stained fingers and a permanent squint from years of reading vellum. He possesses a ‘quiet intensity’—the kind of man who listens to the pulse of a building before entering it.
Traits: Meticulous, ethically driven, yet haunted by his father’s legacy of obscurity. He seeks to understand if knowledge is a gift to be shared or a burden to be guarded.
Julian Vane
Role: antagonist
Description: An octogenarian ‘Information Architect’ and billionaire recluse. He moves with a predatory grace, dressed in bespoke charcoal wools. His voice is a dry rasp, like sandpaper on stone.
Traits: Believes that ‘Truth’ is a finite resource that loses value when observed by the masses. He views himself as the rightful owner of the world’s most dangerous silences.
Dr. Clara Reed
Role: supporting
Description: A forensic linguist in her 30s. Sharp, cynical, and brilliant. She views language as a cage and silence as the only true freedom.
Traits: Driven by the thrill of the ‘untranslatable.’ She helps Elias decode the architectural ciphers but fears the weight of what they might find.
Settings
ossuary-of-echoes
Description: A subterranean archive located beneath a decommissioned cathedral. It is filled with ‘negative space’ shelving—rows of empty boxes that represent suppressed histories.
Atmosphere: Cold, damp, smelling of ozone and ancient dust. The silence here feels heavy, almost pressurized.
Significance: Represents the physical manifestation of secret knowledge as a tangible, stored asset.
glass-spire
Description: A brutalist skyscraper of reinforced glass and steel overlooking a fog-choked city. The interior is minimalist to the point of hostility.
Atmosphere: Sterile, blindingly bright, and voyeuristic. It creates the paradox of total transparency hiding total secrecy.
Significance: The seat of power where knowledge is curated and commodified.
blackwood-estate
Description: A decaying 18th-century manor in the countryside, built with ‘impossible’ geometry—rooms that appear on blueprints but cannot be found in the physical house.
Atmosphere: Melancholic, gothic, and shifting. The house feels like it is holding its breath.
Significance: The site where the ‘Primordial Property’ was first codified by Elias’s ancestors.
Act Structure
Act 1: The Inheritance of Shadows
Purpose: To establish the ‘Primordial Property’ and the stakes of owning a secret that predates law.
Estimated Scenes: 3
Key Developments:
- Elias receives a cryptic inheritance
- He discovers the existence of ‘The Architecture of Silence’
- Julian Vane issues a warning
Act 2: The Weight of the Unspoken
Purpose: To explore the philosophical conflict between the ‘right to know’ and the ‘right to own’ truth.
Estimated Scenes: 3
Key Developments:
- Infiltration of the Blackwood Estate
- The discovery of the ‘Negative Blueprints’
- The confrontation with Vane’s philosophy
Act 3: The Primordial Deed
Purpose: To resolve the tension through a final choice: to release the secret (destroying its value) or to become its new silent guardian.
Estimated Scenes: 3
Key Developments:
- The descent into the Ossuary
- The choice to speak or stay silent
- The transformation of Elias
Status: ✅ Pass 1 Complete
Outline
The Architecture of Silence
Premise: The Dramatization of Secret Knowledge as Primordial Property
Estimated Word Count: 3000
Total Scenes: 9
Detailed Scene Breakdown
Act 1: The Inheritance of Shadows
Purpose: To establish the ‘Primordial Property’ and the stakes of owning a secret that predates law.
Scene 1: The Geometry of the Void
- Setting: blackwood-estate
- Characters: Elias Thorne
- Purpose: Elias receives a cryptic inheritance; Introduction to the ‘impossible geometry.’
- Emotional Arc: Elias moves from methodical investigation and confusion to a heavy sense of realization and inherited guardianship as he senses the house’s true nature.
- Est. Words: 1500
Key Events: { “1” : “Elias measures the foyer and discovers three feet of ‘missing’ reality compared to the blueprints.”, “2” : “He examines his inheritance: a toothless iron key and a vellum deed for a ‘Right of Non-Existence’.”, “3” : “He experiences the ‘pressurized silence’ and rhythmic thrumming within the house’s structure.”, “4” : “He finds his father’s final note hidden in a book, explaining the duty to guard the silence that predates the Word.” }
Scene 2: The Syntax of the Unseen
- Setting: blackwood-estate
- Characters: Elias Thorne, Dr. Clara Reed
- Purpose: Discovery of ‘The Architecture of Silence’; Introduction of the ‘Negative Blueprints.’
- Emotional Arc: Clara’s initial cynicism shifts to wavering awe as she realizes the blueprints represent a linguistic trap; the atmosphere turns thin and intense.
- Est. Words: 1800
Key Events: { “1” : “Clara analyzes the ‘Negative Blueprints’ where rooms are solid ink and walls are white.”, “2” : “She identifies the notations as phonetic constraints designed to prevent a specific truth from being uttered.”, “3” : “Elias explains his father’s concept of the ‘Architecture of Silence’ as a cage for a secret.”, “4” : “They realize the blueprints lead to a subterranean archive known as the Ossuary of Echoes.” }
Scene 3: The Market of Shadows
- Setting: glass-spire
- Characters: Elias Thorne, Julian Vane
- Purpose: Julian Vane issues a warning; Establishing the stakes of the ‘Information Architect.’
- Emotional Arc: Elias feels a jarring sense of claustrophobia in the sterile environment, facing Vane’s predatory and cold dominance.
- Est. Words: 1600
Key Events: { “1” : “Elias is summoned to the sterile, high-tech Glass Spire to meet Julian Vane.”, “2” : “Vane dismisses Elias’s father as a sentimentalist and defines silence as a scarce commodity.”, “3” : “Vane warns Elias that the Primordial Property is a liability and forbids him from opening the Ossuary.”, “4” : “The conflict is established: Elias is now an obstacle to a billionaire’s quest to own the foundation of truth.” }
Act 2: The Weight of the Unspoken
Purpose: To explore the philosophical conflict between the “right to know” and the “right to own” truth.
Scene 1: The Geometry of Absence
- Setting: blackwood-estate
- Characters: Elias Thorne, Dr. Clara Reed
- Purpose: To introduce the supernatural/impossible nature of the setting and the method of entry.
- Emotional Arc: Skepticism and wariness transitioning into awe and sensory oppression as the impossible nature of the house is revealed.
- Est. Words: 1500
Key Events: { “arrival” : “Elias and Clara arrive at the Blackwood Estate under a purple twilight.”, “explanation” : “Elias explains the ‘Impossible Geometry’ and Clara notes the ‘pre-lexical’ carvings.”, “infiltration” : “Using a hand-mirror to navigate a ‘blind spot’ in the masonry, they find a hidden door and enter the manor.” }
Scene 2: The Negative Blueprints
- Setting: blackwood-estate
- Characters: Elias Thorne, Dr. Clara Reed
- Purpose: To reveal the nature of the ‘Primordial Property’ and the stakes of the secret.
- Emotional Arc: Horror and fascination as the weight of the unspoken begins to physically affect the characters, creating a sense of crushing responsibility.
- Est. Words: 1800
Key Events: { “discovery_of_room” : “They find a library where shadows form the shapes of books.”, “blueprints_reveal” : “Discovery of the ‘Negative Blueprints’ mapping the voids and silences of the house.”, “legal_revelation” : “Clara uses forensic light to reveal a deed for the concept of silence, realizing the truth’s volatile nature.” }
Scene 3: The Price of Observation
- Setting: blackwood-estate
- Characters: Elias Thorne, Dr. Clara Reed, Julian Vane
- Purpose: To establish the antagonist’s motive and the central philosophical conflict.
- Emotional Arc: High tension and intellectual dread as the characters are confronted with a choice between their sanity and the burden of truth.
- Est. Words: 2000
Key Events: { “confrontation” : “Julian Vane appears in the Great Hall, acting as the house’s curator.”, “philosophical_argument” : “Vane argues that truth is a finite resource and that the ‘Architecture of Silence’ protects the world from collapse.”, “the_choice” : “Vane offers Elias a choice: leave the blueprints and their sanity, or take them and inherit the crushing responsibility of the silence.” }
Act 3: The Primordial Deed
Purpose: To resolve the tension through a final choice: to release the secret (destroying its value) or to become its new silent guardian.
Scene 1: The Pressure of the Void
- Setting: ossuary-of-echoes
- Characters: Elias Thorne, Dr. Clara Reed
- Purpose: To introduce the physical manifestation of the secret and establish the stakes and physical pressure of the environment.
- Emotional Arc: From cautious exploration and physical discomfort to awe and realization of the secret’s true nature.
- Est. Words: 1200
Key Events: { “events” : [ “Descent into the Ossuary”, “Discovery of the physical ‘Deed’ (crystalline cylinder)”, “Realization that the Ossuary is a resonator”, “Understanding that the silence is the anchor for human hierarchy” ] }
Scene 2: The Price of Transparency
- Setting: ossuary-of-echoes
- Characters: Elias Thorne, Dr. Clara Reed, Julian Vane
- Purpose: The philosophical climax where the protagonist must choose between two conflicting ideologies regarding the nature of secrets.
- Emotional Arc: High tension and moral conflict as Elias is caught between Vane’s cold logic and Clara’s idealistic transparency.
- Est. Words: 1500
Key Events: { “events” : [ “Confrontation with Julian Vane”, “Vane explains the ‘Primordial Property’ and the value of hidden knowledge”, “Clara argues against the hoarding of potential”, “Elias realizes his father’s true motive was protection, not power” ] }
Scene 3: The Architect of the Unspoken
- Setting: ossuary-of-echoes
- Characters: Elias Thorne, Julian Vane, Dr. Clara Reed
- Purpose: Resolution of the conflict through Elias’s transformation and the resulting impact on the world.
- Emotional Arc: Sacrifice and somber acceptance, leading to a sense of stable but heavy resolution.
- Est. Words: 1000
Key Events: { “events” : [ “Elias seals the Ossuary from the inside”, “Clara escapes as the negative space expands”, “Vane loses his ownership of the silence”, “The Glass Spire cracks as the anchor is removed”, “Elias becomes the ‘Architecture of Silence’” ] }
Status: ✅ Complete
Setting: ossuary-of-echoes
Prompt:

Setting: glass-spire
Prompt:

Setting: blackwood-estate
Prompt:

Character: Elias Thorne
Prompt:

Character: Julian Vane
Prompt:

Character: Dr. Clara Reed
Prompt:

## The Geometry of the Void
Act 1, Scene 1
Setting: blackwood-estate
Characters: Elias Thorne
The Blackwood Estate did not merely sit upon its hill; it seemed to have been exhaled by the earth, a jagged outcropping of granite and dark timber that defied the gentle, rolling slopes of the valley. To Elias Thorne, a man who had spent his life translating the world into the rigid, uncompromising syntax of blueprints, the house was a grammatical error in a landscape of prose. It was a structural heresy, a building that leaned into dimensions that had no right to exist.
It was late afternoon. The sun was a bruised plum hanging low over the horizon, casting skeletal shadows that stretched across the foyer like grasping fingers. Elias stood in the center of the hall, the air tasting of cold stone and the metallic tang of ancient dust. In his right hand, he gripped a Leica laser distance meter—a sleek, digital intrusion in this Victorian tomb. In his left, he held a set of yellowed, linen-backed blueprints, their edges frayed and smelling of cedar.
At forty, Elias possessed the lean, hungry look of an academic who had skipped too many meals in favor of old texts. His eyes, framed by thin-rimmed glasses, were weary, darkened by years of searching for structural flaws in the works of others—as if finding a crack in a foundation could somehow explain the fractures in his own life.
He clicked the laser. A red dot danced on the far wall, a tiny, unblinking eye of light.
“Forty-two feet, six inches,” Elias whispered.
His voice was swallowed instantly. There was no echo, no resonance. It was as if the walls were lined with heavy velvet rather than lath and plaster. The silence here wasn’t just the absence of sound; it was a physical weight, a vacuum that pulled the oxygen from his lungs.
He looked down at the 1922 blueprints, drawn by his great-grandfather and maintained by his father, Arthur, until his sudden, silent passing three weeks ago. According to the precise, hand-inked lines, the foyer was exactly forty-five feet, six inches long.
Elias frowned, his thumb tracing the edge of the brass-bound ruler in his pocket. He moved to the exterior wall and measured again. He checked the thickness of the masonry, accounted for the wainscoting, and recalculated the offset of the chimney breast. No matter how he manipulated the variables, three feet of space had simply vanished.
It wasn’t a hidden room—the exterior dimensions of the house matched the interior ones perfectly, provided one ignored the discrepancy. The math refused to settle. It was as if the house were breathing, and he had caught it mid-exhale, the structure contracting in a way that defied Euclidean geometry.
“Three feet of nothing,” he murmured, the words heavy on his tongue.
As he stood there, a strange, localized pressure built in his inner ear—the sharp, uncomfortable sensation of a plane beginning a rapid descent. It wasn’t a sound, but the anticipation of one. Then came the thrumming. It was a rhythmic vibration, so low it was felt in the marrow of his shins rather than heard. It hummed through the floorboards, a steady, mechanical pulse. It was the heartbeat of a machine that had no business being made of wood and stone.
Elias retreated from the foyer, his footsteps sounding unnaturally loud, and sought refuge in his father’s study. The room was a sanctuary of shadows, smelling of stale pipe tobacco and the sharp, ozone scent of cold iron. On the massive oak desk sat the mahogany box delivered to him by a solicitor who had refused to meet his eyes, handing over the inheritance with a trembling hand before fleeing the estate.
Elias opened the box. The hinges didn’t creak; they glided with a silent, oiled precision.
Inside lay two items. The first was an iron key, heavy and cold enough to ache against his palm. It was a peculiar object—entirely smooth, lacking any teeth, bitting, or wards. It was a key designed to fit a lock, but not to turn one. Its surface was pitted by centuries of oxidation, yet its weight suggested a density that defied its size. It felt less like a tool and more like an anchor.
The second item was a deed, written on vellum so thin it was nearly translucent, like the skin of a deep-sea fish. The ink was a deep, brownish-black—the color of dried blood. Elias spread it out, his fingers trembling.
“Grant of the Right of Non-Existence,” the header read in a sprawling, archaic script.
The legal language that followed was a dizzying labyrinth of medieval Latin and modern jurisdictional jargon. It didn’t describe a plot of land, a physical structure, or mineral rights. Instead, it laid claim to a “primordial silence,” a “void-space held in trust,” and a “property of the unspoken.” It was a title deed for a vacuum. It suggested that the Blackwood family did not own the house, but rather the absence that the house had been constructed to contain. The walls were not the asset; they were the packaging.
Elias leaned back, the leather chair creaking beneath him like a living thing. As an architect, he understood that space was defined by its boundaries. A room was only a room because of the walls that denied the rest of the world entry. But this was a reversal of every principle he held dear. This suggested that the silence itself was the commodity—a secret knowledge that functioned as a form of primordial property.
The thrumming in the floorboards intensified, vibrating through the legs of the chair. The silence in the room became pressurized, pushing against his eardrums until they throbbed. It was a heavy, liquid silence, the kind that exists at the crushing depths of the ocean where light cannot reach.
He looked at the bookshelves, thousands of volumes inherited from generations of Thornes—architects, engineers, and cartographers who had lived and died within these shifting walls. His eyes landed on a small, unassuming spine bound in cracked black leather: The Commentaries on the Unspoken.
He pulled it from the shelf. As he did, a slip of paper fluttered out from between the pages and drifted to the floor like a falling leaf. Elias picked it up. It was a note in his father’s hand, the script frantic and spindly.
Elias,
The world is built upon a lie of noise. We believe that in the beginning was the Word, but the Word was merely a disturbance, a ripple on a still pond. Before the Word, there was the Architecture of Silence. It is the foundation of all things, the dark matter of the soul. Our family has been the stewards of this void for seven generations. We do not guard the house; we guard what the house encloses.
Do not attempt to measure the gaps, Elias. The geometry of this place is not Euclidean. It follows the logic of the things that were here before light was permitted. If you find the missing feet, do not enter them. The silence is not an absence of sound—it is a presence that has not yet chosen to speak.
Your duty is simple: Maintain the boundaries. Do not let the silence leak. If the world hears what is kept at Blackwood, the Word will be undone.
Your father, Arthur.
A cold sweat broke across Elias’s brow. He looked back at the blueprints spread across the desk. The three feet of missing reality. He realized now that he hadn’t been looking at a mistake in the drawing or a lapse in his great-grandfather’s craftsmanship. He had been looking at a cage. The house was a vessel, a lead-lined box designed to keep a specific type of nothingness from spilling out into a world of sound.
He stood up, the iron key heavy in his pocket, pulling at his coat. He walked back out into the foyer. The sun had finally dipped below the horizon, and the house was now a cavern of absolute shadows. He looked at the wall where the three feet should have been—the space between the reality of the blueprints and the reality of the stone.
In the dim, grey light, the wallpaper—a pattern of intricate, interlocking vines—seemed to shift and writhe. The geometry of the hall felt skewed, the angles of the ceiling not quite meeting at ninety degrees, the floor sloping toward a center that wasn’t there. He reached out and touched the wall.
It didn’t feel like plaster. It didn’t feel like wood. It felt like skin stretched tight over a drum.
Beneath his palm, the thrumming was no longer a vibration; it was a cadence. A rhythmic, pulsing beat that matched his own heart, then slowly, inexorably, began to lead it. The house was setting his pace.
Elias closed his eyes. In the absolute, suffocating quiet of the Blackwood Estate, he realized his father was right. The silence wasn’t empty. It was crowded. It was a vast, teeming territory of secret knowledge, a property of the universe that had been privatized by his bloodline. He was no longer just an architect or an heir. He was a jailer of the vacuum.
He reached into his pocket and gripped the toothless key. He understood its purpose now. It wasn’t meant to open a door. It was a weight, a symbol of the gravity required to keep the void in place, a physical reminder of the burden he now carried.
A floorboard creaked upstairs, but it wasn’t the sound of a footfall. It was the sound of the house adjusting itself to his presence, the architecture settling around him like a shroud, fitting itself to his frame.
Elias Thorne took a deep breath, the air tasting of dust and ancient, unuttered thoughts. He folded the deed and placed it in his breast pocket, right over his heart. The confusion that had gripped him since his father’s funeral began to solidify into a cold, hard resolve. He was a Thorne. He was a builder of boundaries.
He would not measure the gaps again. He would learn the language of the silence, and he would ensure that the “Right of Non-Existence” remained the most valuable, and most terrifying, thing he owned.
The house seemed to sigh in approval, a low rush of air through the vents that sounded like a name being whispered. The shadows in the foyer lengthened, stretching toward him like a welcoming embrace, pulling the new master into the heart of the void. Elias stood still, a silhouette in the center of his dark inheritance, listening to the beautiful, terrible sound of nothing at all.
Word Count: 1766
Key Moments:
- The Discrepancy: Elias uses professional tools to discover that the physical dimensions of the Blackwood foyer do not match the blueprints, revealing a ‘missing’ three feet of space.
- The Inheritance: Elias examines the toothless iron key and the ‘Right of Non-Existence’ deed, introducing the concept of silence and void as a form of primordial property.
- The Sensory Shift: The atmosphere of the house changes, manifesting as ‘pressurized silence’ and a rhythmic thrumming that suggests the house is a living or mechanical entity.
- The Father’s Revelation: Elias finds Arthur Thorne’s final note, which explains the family’s true purpose: acting as guardians of a pre-linguistic silence that must not be unleashed upon the world.
Character States:
- Elias Thorne: Ends the scene in a state of ‘cold, hard resolve.’ He has moved from the frustration of a technical professional facing an error to the somber acceptance of a man who has inherited a metaphysical burden. Physically, he is attuned to the house, his own heartbeat syncing with the ‘thrumming’ of the structure.
Status: ✅ Complete
Act 1, Scene 1 Image
Prompt:

## The Syntax of the Unseen
Act 1, Scene 2
Setting: blackwood-estate
Characters: Elias Thorne, Dr. Clara Reed
The rain did not fall upon the Blackwood Estate so much as it surrendered to it. The droplets lost their momentum the moment they crossed the property line, sliding down the air like oil on glass, refusing to splash against the grey stone. Inside the great library, the atmosphere had achieved a state of crystalline stasis. The thrumming Elias had felt in the foyer was more pronounced here—a low-frequency vibration that originated not from the floorboards, but from the very molecules of the oxygen they breathed. It was the sound of a held breath.
Elias Thorne stood by the mahogany drafting table, his hands hovering over a roll of vellum that felt unnervingly like cured skin. He did not look up when the heavy oak doors groaned open. He didn’t need to. The scent of rain-dampened wool and sharp, expensive espresso preceded Dr. Clara Reed.
“You look like a man who has seen a ghost, Elias,” Clara said, her voice cutting through the pressurized silence like a scalpel. She shed her trench coat, draping it over a bust of a nameless Roman orator. “Or perhaps just a very expensive structural error. This house has a way of making one feel like an intruder in a math equation.”
Clara Reed was a woman of sharp angles and sharper intellect, a specialist in semiotic architecture who had spent a decade proving that buildings were merely petrified sentences. She had been Elias’s only call. If anyone could read the grammar of this house, it was her. They had a history written in the margins of academic journals—a decade of professional friction that bordered on something more volatile.
“It’s not an error, Clara,” Elias said, his voice sounding hollow, as if the room were drinking the resonance of his words. “Errors are accidental. This is… intentionality taken to a pathological extreme. My father didn’t build a home. He built a thesis.”
He unrolled the blueprints, the vellum resisting with a dry, papery hiss.
Clara stepped forward, her cynical expression flickering for a moment before hardening into a mask of professional curiosity. She leaned over the table, her glasses sliding down the bridge of her nose. She froze. Her hand reached out, hovering an inch above the page, as if she feared the ink might still be wet—or perhaps alive.
“These are negative blueprints,” she whispered.
In traditional architectural drafting, lines represent the presence of matter—walls, pillars, beams—against the white void of the page. But the documents Arthur Thorne had left behind were inverted. The rooms were solid, oppressive blocks of abyssal black ink, while the walls, the corridors, and the structural supports were represented by the stark, untouched white of the vellum. It was a map of the absence of space.
“The rooms are the solids,” Clara murmured, her finger tracing a jagged black rectangle that represented the library they stood in. “And the walls are the voids. He didn’t design a house, Elias. He carved a series of hollows out of a singular, primordial mass. He treated the air as the load-bearing element.”
“Look at the notations,” Elias directed, pointing to the margins where the ink bled into frantic, microscopic script.
Clara squinted. Instead of standard measurements—feet, inches, load-bearing tolerances—the margins were crowded with symbols that had no place in an engineering firm. They were phonetic symbols: International Phonetic Alphabet characters, crossed out with violent, precise strokes.
“Glottal stops,” Clara read, her brow furrowing. “Fricatives. He’s… he’s outlawing the letter S. He’s forbidding the resonance of open vowels in the north-facing rooms.” She looked up, her eyes wide with a dawning, uncomfortable awe. “Elias, these aren’t structural constraints. These are phonetic ones. He’s trying to legislate the air.”
“My father called it the ‘Architecture of Silence,’” Elias said. He walked to the window, looking out at the grey shroud of the estate. The trees didn’t sway; they merely leaned. “He believed that certain truths—primordial truths—were so volatile that they could only exist if they were never spoken. He used to say that language is a virus; it seeks a host. It seeks to be uttered. So, he built a cage where the virus couldn’t breathe.”
Clara walked around the table, her skepticism wavering, replaced by the frantic energy of a cryptographer who had just found a code she couldn’t break. “A cage made of stone and wood. He designed the dimensions of these rooms to act as acoustic dampeners, not for sound in general, but for specific phonemes. If you try to speak the ‘secret’ in this room, the geometry of the walls would literally cancel out the frequency of your voice. The house is a muzzle, Elias. It’s a physical manifestation of a gag order.”
“It’s more than that,” Elias said, turning back to her. The light from the window cast long, distorted shadows across his face. “He wasn’t just trying to stop someone from speaking. He was trying to protect a property. The ‘Right of Non-Existence.’ He believed that silence was the only thing we truly own, because once a thought is spoken, it belongs to the world. It becomes common property. It becomes… corrupted. He wanted to keep his secrets pure by keeping them unformed.”
The air in the library seemed to thin, the atmospheric pressure dropping as if they were ascending a mountain. Clara felt a slight lightheadedness, a sensation of being pulled toward the center of the black ink on the table. She pointed to a section of the blueprint where the white lines—the ‘void’ walls—converged into a spiral that descended off the edge of the page, spiraling into a depth that the house’s exterior shouldn’t allow.
“This isn’t the basement,” she said, her voice trembling slightly. “The geometry here… it doesn’t follow the footprint of the house. It goes deeper. It’s a subterranean extension that exists outside the grid.”
Elias joined her, looking at the spiral. “The Ossuary of Echoes.”
“The what?”
“That’s what he called it in his journals. He wrote that if the house is the muzzle, the Ossuary is the throat. It’s where the ‘unspoken’ is stored. He believed that sound doesn’t die; it just loses energy. It settles in the lowest points of a structure like silt in a riverbed. He spent forty years dredging the silence.”
Clara laughed, a short, brittle sound that died instantly in the heavy air, swallowed by the bookshelves. “Elias, this is madness. It’s beautiful, terrifying madness, but it’s just… it’s a metaphor. Your father was a brilliant man who suffered from a very specific, very architectural brand of psychosis. You can’t store a sound like a bottle of wine.”
“Is it a metaphor?” Elias reached into his pocket and pulled out the toothless iron key he had found in his father’s desk. He laid it on the black ink of the blueprint. “The foyer is missing three feet of space, Clara. I measured it this morning. The physical reality of this house has been altered to accommodate the silence. You can feel it, can’t you? The pressure in your ears? The way the house seems to be… listening for a mistake?”
Clara looked at the key, then back at the negative blueprints. She thought of her years studying the ‘language of space,’ the way a cathedral makes one feel small to encourage piety, the way a prison makes one feel watched to encourage submission. But this was different. This was a building designed to negate the human capacity for expression. It was an anti-cathedral.
She reached out and touched the vellum. The ink felt cold, unnaturally so, as if it were drawing heat from her fingertips. “If these blueprints are accurate,” she said, her voice dropping to a whisper, “then the entrance to this ‘Ossuary’ isn’t behind a door. It’s behind a frequency.”
“Explain,” Elias demanded, his pulse quickening.
“Look at the convergence of these white lines,” Clara said, her finger tracing the spiral. “They meet at a point in the cellar that corresponds to a perfect acoustic dead zone. In any other building, that would be a flaw—a place where sound simply vanishes. Here, it’s a gateway. If you stand in that spot and produce a sound that the house cannot cancel—a sound that isn’t in its ‘forbidden’ vocabulary—the resonance might trigger the physical mechanism. It’s a sonic lock.”
Elias looked at her, his resolve hardening into something cold and sharp. “And what sound would that be? What is the one thing my father couldn’t forbid?”
“I don’t know,” Clara admitted, her cynicism finally crumbling into a raw, academic hunger. “But the blueprints suggest it’s something pre-linguistic. A hum. A vibration. Something from before we had words for things. A sound that exists in the body, not the mind.”
She looked at Elias, and for the first time, they were in total alignment. The skepticism that had defined their professional relationship for years had been burned away by the sheer, impossible weight of the evidence before them. They weren’t just an architect and a linguist anymore; they were two people standing on the edge of a linguistic event horizon.
“We have to go down there,” Elias said. It wasn’t a question.
“The air will be thin,” Clara warned, though she was already reaching for her bag, her hands steady despite the chill. “If the house is designed to trap sound, the oxygen levels might be manipulated by the same vacuum-sealed logic. It’s a tomb, Elias. A tomb for things that were never said. We might find that silence is heavier than we can carry.”
“My father spent his life guarding it,” Elias said, picking up the iron key. The metal seemed to warm in his hand, pulsing in time with the house’s low, rhythmic thrum. “He died to keep it silent. I need to know if he was a saint or a jailer. I need to know what he was so afraid of hearing.”
As they left the library, the shadows seemed to retreat before them, not out of fear, but as if they were making a path, drawing them toward the center of the spiral. The descent to the cellar was a journey through layers of increasing stillness. Each step down the stone stairs felt like diving into deep water. The sound of their footsteps, usually sharp and echoing in a house of this size, was swallowed instantly, muffled as if the air itself were made of velvet.
By the time they reached the heavy, reinforced door of the cellar, the silence had become a physical weight, a pressure against their eardrums that made their own heartbeats sound like thunder. The world above—the rain, the wind, the rustle of trees—felt like a distant memory of a louder life.
Elias inserted the toothless key into the lock. There were no tumblers, no mechanical click. Instead, as he turned the key, there was a low, resonant vibration that traveled up his arm and into his chest, a chord struck on a piano with no strings. The door didn’t swing open; it simply ceased to be an obstacle, sliding into the wall with a smoothness that suggested it was moved by the sheer absence of friction.
Beyond the door lay a darkness so absolute it seemed to have mass, a thick, ink-like gloom that the light from the hallway refused to penetrate.
Clara clicked on her high-intensity flashlight. The beam cut through the gloom, revealing a space that defied the laws of the estate above. The walls were lined with thousands of small, ceramic cylinders, each one corked with lead and etched with a single, unique character. They looked like the scrolls of an ancient library, but they were arranged in a pattern that mimicked the complex, winding anatomy of the human inner ear.
“The Ossuary of Echoes,” Clara whispered. Her voice didn’t travel; it fell flat at her feet, as if the words were made of lead.
Elias stepped into the room, the flashlight beam dancing over the lead-corked cylinders. “He didn’t just build a cage for a secret, Clara. He built a filing system for it. Every word he ever suppressed, every thought he deemed too dangerous to utter… he archived them.”
In the center of the room stood a single, obsidian pedestal. On top of it sat a device that looked like a cross between a Victorian phonograph and a surgical instrument. It was a needle of polished bone, suspended over a rotating plate of pure, translucent quartz.
“He wasn’t just a guardian,” Elias realized, his voice trembling with a mixture of horror and awe. “He was a collector. Every word that was forbidden upstairs… he caught them here. He was harvesting the silence.”
Clara approached the pedestal, her hand trembling as she reached toward the quartz plate. “Elias, if this is what I think it is… if these cylinders contain the ‘unspoken’… then this isn’t just a house. It’s a weapon. A linguistic bomb. If you were to release these sounds all at once—if you broke the seals—”
“The world would lose the ability to mean anything,” Elias finished. “The noise would drown out the sense.”
The thrumming of the house reached a crescendo, a vibration so intense that the ceramic cylinders began to rattle in their niches, a thousand tiny teeth chattering in the dark. The silence was no longer empty; it was crowded, pregnant with the weight of a billion unuttered thoughts, all straining against their leaden seals.
Elias looked at the negative blueprints he still held in his left hand. In the light of the flashlight, the white lines seemed to glow, revealing a final notation he hadn’t seen before, written in his father’s hand at the very center of the spiral:
The truth is not what we say. The truth is what remains when we are forced to be still.
“We aren’t alone down here,” Clara whispered, her eyes fixed on the darkness beyond the pedestal.
Elias turned the light. At the far end of the vault, the shadows didn’t just sit; they moved, swirling in a slow, rhythmic pattern that matched the thrumming of the house. It was a shape—or the absence of one—standing in the center of the void, a silhouette carved out of the darkness, waiting for the new master to speak the first word.
The air grew impossibly thin. The silence began to scream. Elias gripped the key, the metal now searingly hot, as the shadow stepped forward into the light that wasn’t there.
Word Count: 2408
Key Moments:
- The Negative Blueprints: Clara and Elias analyze the inverted maps, realizing the house is designed as a physical “muzzle” to prevent specific sounds and truths from being uttered.
- Phonetic Constraints: Clara identifies that the architecture uses “phonetic constraints,” cancelling out specific linguistic frequencies through its geometric design.
- The Ossuary Discovery: They follow the blueprints to a hidden subterranean vault—the Ossuary of Echoes—where “unspoken” sounds are stored in lead-corked ceramic cylinders.
- The Linguistic Bomb: They realize the estate is a repository for primordial secrets that, if released, could destroy the human capacity for language and meaning.
Character States:
- Elias Thorne: Physically exhausted but mentally hyper-focused. He has transitioned from a skeptical heir to a man who understands he is the warden of a metaphysical armory. He feels a heavy, vibrating connection to the house.
- Dr. Clara Reed: Her initial academic cynicism has been completely shattered, replaced by a mixture of professional awe and existential dread. She is physically affected by the “thin air” of the vault and is now fully committed to the mystery.
Status: ✅ Complete
Act 1, Scene 2 Image
Prompt:

## The Market of Shadows
Act 1, Scene 3
Setting: glass-spire
Characters: Elias Thorne, Julian Vane
The transition from the subterranean depths of the Blackwood Estate to the apex of Vane Tower was a violent decompression, a change in state that felt less like travel and more like a betrayal of the senses. In the Ossuary, the air had been thick with the dust of centuries and the heavy, vibrating pressure of secrets that refused to be named. Here, sixty stories above the city, the atmosphere was scrubbed, filtered, and chilled to a precise sixty-eight degrees. It smelled of clinical absence—not even the ozone of the servers humming beneath the floorboards was permitted to linger.
Elias Thorne stood in the center of the elevator, his reflection caught in the polished obsidian of the doors. He looked like a man who had been unearthed, a relic of a darker, more cluttered era. His suit, though tailored and expensive, felt like a shroud, and his eyes remained dilated, still adjusted to the protective gloom of the vault. In his pocket, the toothless iron key felt like a hot coal against his thigh. It was a piece of the old world—heavy, jagged, and unapologetically physical—an affront to the seamless, frictionless environment of the Glass Spire.
The doors slid open with a soundless sigh, revealing the inner sanctum of the man who owned the horizon.
The office of Julian Vane was not an office so much as a cathedral of transparency. Floor-to-ceiling glass walls offered a panoramic view of the city, which, from this height, looked like a sprawling motherboard, its inhabitants reduced to pulses of light and data. There were no books here, no paper, no clutter of history. Only a desk of white marble that seemed to grow organically out of the floor and a single chair facing the edge of the world.
Julian Vane stood by the window, silhouetted against the blinding morning sun. He was a man of sharp angles and mathematical precision, his hair a silvered mane that caught the light like spun glass. He didn’t turn when Elias entered. He didn’t need to. In this building, Vane was the architect of every movement, every breath, every stray thought.
“The city is a cacophony, Elias,” Vane said, his voice a smooth, cultured baritone that seemed to resonate directly from the glass itself. “A billion voices screaming for attention, for validation, for a single moment of being heard. It is a tragedy of noise, a fever of self-expression that has finally broken the world.”
Elias walked forward, his footsteps sounding unnaturally loud on the polished floor, each strike of his heel a rhythmic intrusion. “My father used to say that noise is just the sound of people trying to convince themselves they exist. He thought the louder the world got, the more we were actually losing.”
Vane turned then, a thin, predatory smile touching his lips. His eyes were a piercing, artificial blue—the color of a screen at maximum brightness. “Arthur was always a poet of the void. A sentimentalist, ultimately. He spent his life guarding a treasure he was too afraid to spend, like a dragon sitting on a hoard of gold he couldn’t even see.”
“He wasn’t guarding a treasure,” Elias said, his voice tightening. “He was guarding a boundary. There’s a difference between wealth and a wall.”
Vane gestured toward the marble desk, a movement as fluid as water. “Sit. You look as though you’ve spent the night wrestling with ghosts. Or perhaps just the architecture of your own inheritance. It’s a heavy thing, isn’t it? To realize you are the heir to a vacuum.”
Elias sat, feeling the jarring claustrophobia of the open space. In the Ossuary, the walls had been close, protective in their density. Here, the vastness felt like a vacuum, threatening to pull the air from his lungs. He felt exposed, a specimen under a microscope.
“I know what you found, Elias,” Vane said, leaning against the edge of his desk. “The ‘Right of Non-Existence.’ The negative blueprints. The Ossuary itself. Arthur and I were… collaborators, once. Before his conscience became an occupational hazard. We both saw the coming storm of the Information Age. We both knew that the more the world knew, the less it would understand.”
“He didn’t mention you in his notes,” Elias countered, his hand instinctively moving toward the key in his pocket.
“Of course not. Arthur preferred the shadows. He believed that silence was a sacred trust, a primordial property that belonged to no one and therefore must be protected by someone. He was wrong, of course. In the modern world, silence is not a right. It is a commodity. The rarest, most expensive commodity on Earth.”
Vane leaned in closer, his presence expanding to fill the void of the room. “We live in the Age of Exposure. Everything is mapped. Everything is recorded. Everything is known. Privacy is a dead language. But the foundation of all that knowledge—the primordial silence from which language first crawled, the ‘nothing’ that gives ‘something’ its shape—that remains unclaimed. That is the ‘Primordial Property’ your father died protecting. It isn’t just a lack of sound, Elias. It is the raw material of reality. The ‘undo’ button for the universe.”
Elias felt a chill that had nothing to do with the climate control. “And you want to own it. You want to be the Information Architect who controls the delete key. You want to sell people the ability to never have existed.”
“I want to bring order to the chaos,” Vane corrected, his voice dropping to a whisper. “Your father’s ‘Ossuary’ is a liability in its current state. It is a collection of linguistic pathogens. If those cylinders were opened by someone who didn’t understand the geometry of the void, they wouldn’t just cause silence. They would erase meaning. They would dissolve the capacity for human thought. It is a weapon, Elias. And you are currently holding the trigger without knowing how the safety works.”
Vane’s gaze dropped to Elias’s pocket, where the outline of the iron key was visible against the fabric of his suit.
“I am forbidding you from opening that vault again,” Vane said, his tone shifting from philosophical to cold, corporate command. “The Blackwood Estate is a muzzle, yes. But it is an old, fraying muzzle. You are out of your depth. You think you are the warden, but you are merely the lock. And locks can be replaced, Elias. They can be picked, or they can be broken.”
Elias felt the cold, hard resolve from the previous night crystallize into something sharper, a surveyor’s clarity. He thought of the rhythmic thrumming of the house, the way the very stones of Blackwood had seemed to recognize his blood. He thought of Clara’s face, pale with the realization that they were standing on a linguistic bomb.
“My father left the estate to me,” Elias said, his voice steady and low. “Not to a corporation. Not to a man who views the foundation of truth as a subscription service. If the Ossuary is as dangerous as you say, then it needs a guardian, not an owner. It needs someone who knows how to keep a secret, not someone who knows how to invoice it.”
Vane stood up straight, his silhouette suddenly dwarfing the city skyline behind him. “Guardian? You are a surveyor, Elias. You measure land. You deal in boundaries and dirt. You are not equipped for the architecture of the unspoken. You are a sentimentalist, just like Arthur, clinging to a ‘Right of Non-Existence’ as if it were a family heirloom rather than a global threat.”
Vane walked around the desk, his movements predatory and silent. He stopped inches from Elias, the scent of expensive soap and sterile air-conditioning radiating from him. “The world is changing. The noise is becoming a fever. People are desperate for a way to vanish, for a way to un-know what they have seen and un-say what they have shouted. I can provide that. I can build a world where silence is a sanctuary for those who can afford the peace. But I need the source code. I need what is in that vault.”
“You’ll never get it,” Elias said, standing up to meet Vane’s gaze.
“I already have the blueprints,” Vane whispered, his eyes locking onto Elias’s with terrifying intensity. “I have the history. I have the maps of the negative space. All I lack is the physical access—the bridge between the concept and the reality. You are the only thing standing between the world and a curated silence. Do you really think you can withstand the pressure? The house is already screaming, Elias. I can hear it from here.”
Elias turned toward the elevator, his heart hammering against his ribs in a rhythm that felt suspiciously like the thrumming of the Blackwood foundations. “The house isn’t screaming. It’s breathing. And it doesn’t like you.”
Vane laughed, a dry, hollow sound that lacked any hint of mirth. “The house is a machine, boy. A machine built to contain a god that doesn’t want to be caged. Your father spent his life trying to keep the door shut, but he was a fool. I am telling you, the hinges are breaking. If you don’t hand over the key, you won’t be a guardian. You’ll be the first casualty when the silence finally breaks out.”
Elias stepped into the elevator. “I’ll take my chances with the silence. It’s the noise I’m worried about.”
“Elias,” Vane called out as the doors began to close.
Elias looked back. Vane was silhouetted against the blinding light of the sun, a dark shape carved out of the brilliance, much like the shadow Elias had seen in the depths of the vault.
“You aren’t the master of that house,” Vane said, his voice carrying a chilling, prophetic certainty. “You’re the sacrifice. Arthur knew it. That’s why he didn’t leave you a map. He left you a grave.”
The doors hissed shut, severing the connection.
As the elevator plummeted back toward the earth, Elias leaned his head against the cool obsidian wall. The sterile silence of the Spire felt heavier now, more oppressive than the dust of the Ossuary. He realized with a jolt of terror that Vane wasn’t just a businessman looking for an edge. He was a man who understood the metaphysical weight of the inheritance better than Elias did.
Vane didn’t want to destroy the silence; he wanted to harvest it. He wanted to turn the ‘Right of Non-Existence’ into a tool for the elite, a way for the powerful to erase their sins and for the world to lose its collective memory.
Elias reached into his pocket and gripped the iron key. It was no longer hot; it was ice-cold, a freezing weight that seemed to anchor him to the earth even as the elevator dropped. He wasn’t just a surveyor anymore. He was an obstacle. And in Julian Vane’s world, obstacles were not negotiated with. They were demolished.
When the elevator reached the lobby, the doors opened to the roar of the city—the honking of horns, the chatter of pedestrians, the digital chime of a thousand smartphones. For the first time in his life, the noise felt like a shield, a messy, chaotic proof of life. But as Elias stepped out into the sunlight, he could still feel the rhythmic thrumming beneath the pavement, a heartbeat that didn’t belong to the city.
The silence was following him. And Julian Vane was right about one thing: the hinges were definitely breaking. The Market of Shadows was open, and the price of admission was everything Elias had left.
Word Count: 1933
Key Moments:
- The Contrast of Environments: Elias moves from the ancient, heavy atmosphere of Blackwood to the sterile, high-tech vacuum of the Glass Spire, highlighting the different types of “silence” at play.
- Vane’s Philosophy: Julian Vane defines silence as the ultimate commodity and the “source code” of reality, revealing his intent to monopolize the “Primordial Property.”
- The Warning and Threat: Vane warns Elias that the Ossuary is a “linguistic pathogen” and demands access, establishing Elias as the primary obstacle to his corporate-metaphysical goals.
- The Realization of the Stakes: Elias understands that Vane wants to use the silence to “erase meaning” and “curate reality,” turning a sacred trust into a weaponized service.
Character States:
- Elias Thorne: Physically drained but mentally fortified. He has moved from a state of confusion to one of defensive resolve. He feels the weight of his inheritance not just as a mystery, but as a target on his back. He is beginning to sense the “thrumming” of the house even when he is miles away.
- Julian Vane: Predatory, cold, and utterly confident. He views Elias as a temporary nuisance—a “sentimentalist” who doesn’t understand the power he holds. He ends the scene in a state of calculated aggression, ready to move from persuasion to force.
Status: ✅ Complete
Act 1, Scene 3 Image
Prompt:

## The Geometry of Absence
Act 2, Scene 1
Setting: blackwood-estate
Characters: Elias Thorne, Dr. Clara Reed
The city’s frantic pulse—the digital screams of the Glass Spire and the oily, low-frequency hum of the Market of Shadows—faded into a bruised, unnatural silence as the car climbed the ridge toward the Blackwood Estate. Behind them, the world was a frantic grid of light, a desperate attempt to fill the void with data. Before them, the void was reclaiming its territory.
The sky was no longer blue or black; it had curdled into a deep, suffocating violet. This was the “purple twilight” Elias’s grandfather had documented in his more fevered journals—a chromatic aberration caused not by the setting sun, but by the way the estate’s unique density bent the light. It was the color of a fresh bruise, or an ancient ink that refused to dry.
Elias Thorne gripped the steering wheel until his knuckles were white. He could feel the house before he saw it. It wasn’t a visual recognition so much as a sudden, sharp pressure in his inner ear—the sensation of a storm about to break, or a heavy secret whispered in a small, airless room. Beside him, Dr. Clara Reed sat in a state of rigid fascination. Her hands, usually busy with a tablet or a notebook, lay dead in her lap.
“The air is changing,” she whispered. Her voice sounded thin, as if the atmosphere were stripping the resonance from her vocal cords. “The oxygen feels… heavy. Like it’s being compressed by something we can’t see.”
“It’s not the air, Clara,” Elias said, his voice a low rasp. “It’s the architecture. We’re entering the gravity well of the silence.”
As they rounded the final bend, Blackwood Manor loomed. It did not sit upon the land so much as it seemed to be a puncture wound in the landscape. Built from a stone so dark it appeared to absorb the twilight, the house defied the eye. Gables didn’t meet at right angles; they leaned into one another in a way that suggested a fourth dimension, a geometry of absence. The windows were narrow slits, like the eyes of a predator mid-blink.
Elias killed the engine. The silence that rushed in was not the absence of sound, but a physical weight. It pressed against their eardrums like a cold, velvet hand.
“Look at the masonry,” Clara said, stepping out of the car. Her professional curiosity was fighting a losing battle against her instinct to flee. She walked toward the perimeter wall, her fingers hovering inches from the stone. “Elias, these aren’t decorative.”
He joined her. The stones were etched with deep, swirling grooves. They weren’t runes, nor were they any known script. They looked like the patterns left by wind on sand, or the ripples in water after a stone has vanished beneath the surface.
“Pre-lexical,” Clara murmured, her eyes wide. “These are the shapes the mouth makes before it forms a word. The physical geometry of intent. It’s as if the house is built out of the raw materials of speech, but frozen… denied the right to become language.”
“My grandfather called it the ‘Impossible Geometry,’” Elias said, looking up at the jagged silhouette of the roofline. “He said the house was a muzzle. If you build a room with the right angles, you can cancel out a frequency. If you build a house with the right intent, you can cancel out a truth.”
They moved toward the main entrance, but as they approached the massive oak doors, the path seemed to shift. Elias stopped abruptly, pulling Clara back.
“Don’t look directly at the door,” he warned.
“What? Why?”
“The ‘Blind Spot,’” Elias explained, his heart hammering against his ribs. “The house is designed to protect its interior from the gaze of the uninitiated. There is a fold in the geometry here. If you try to walk straight toward the door, your brain will simply refuse to acknowledge the space. You’ll find yourself walking in a circle, convinced there was never a door there at all.”
Clara squinted, trying to focus on the entrance. As she did, a wave of nausea hit her. The space where the door should be seemed to shimmer and dissolve into a grey, static-like haze. It wasn’t that the door was invisible; it was that her mind was actively deleting the visual data to protect itself from a shape it couldn’t comprehend.
“I can’t… I can’t see it,” she gasped, clutching her stomach. “It’s like a hole in the world.”
“It’s a cognitive firewall,” Elias said. He reached into his coat pocket and pulled out a small, silver-backed hand-mirror. “The human eye is too connected to the brain’s expectations. But the mirror… the mirror doesn’t have a subconscious. It just reflects what is there.”
He turned his back to the house and held the mirror up.
“Look into the glass, Clara. Don’t look at the house. Look at the reflection.”
Clara leaned in, her breath hitching. In the silvered surface of the mirror, the distortion vanished. The door was there—a towering, iron-bound slab of ancient wood, carved with the same pre-lexical swirls they had seen on the walls. But in the reflection, the door wasn’t just a door. It was a throat. The carvings looked like vocal cords, stretched tight and vibrating with a sound they couldn’t hear.
“Now,” Elias commanded, “walk backward. Keep your eyes on the mirror. Follow my lead.”
It was a surreal, agonizing procession. They moved like penitents, retreating toward their destination. Every instinct in Clara’s body screamed at her to turn around, to face the direction she was moving. The air grew colder, smelling of ancient dust and something metallic—the scent of a lightning strike.
As they crossed the threshold of the “blind spot,” the sensory oppression intensified. The silence became a roar of nothingness. Clara felt a phantom pressure on her tongue, as if an invisible hand were trying to pull the words right out of her throat.
“Almost there,” Elias hissed. His face in the mirror was pale, his eyes dark with the strain of navigating the impossible.
Suddenly, the mirror’s reflection flickered. The door in the glass seemed to open, not outward, but inward into a space that shouldn’t exist. Elias reached back, his hand fumbling for the cold iron of the real-world handle that his eyes still couldn’t see.
His fingers closed around it. With a groan of protesting metal, the door swung open.
They tumbled inside, the heavy oak slamming shut behind them with a sound that wasn’t a bang, but a sudden, absolute cessation of all external noise.
They were in the Great Hall, but it was a hall only in the sense that it had a floor and walls. The ceiling was lost in a swirling gloom where the purple twilight of the exterior had deepened into a bruised indigo. The pillars that supported the roof didn’t stand straight; they spiraled upward like frozen smoke, their surfaces covered in the same pre-lexical carvings, glowing with a faint, bioluminescent silver.
Clara collapsed to her knees, gasping for air. “It’s… it’s worse in here.”
“The pressure,” Elias agreed, leaning against the door. He felt the thrumming now, more powerful than ever. It was coming from beneath the floorboards, a rhythmic, subterranean heartbeat. “The house isn’t just holding the silence. It’s breathing it.”
Clara looked up, her eyes darting around the impossible room. “Elias, the carvings… they’re moving.”
He looked. She was right. The silver light in the grooves of the pillars was shifting, flowing like mercury. As they watched, the shapes seemed to coalesce, forming patterns that teased the edge of recognition before dissolving back into chaos.
“They’re reacting to us,” Clara whispered, her voice trembling. “To our presence. To our… language.”
“We shouldn’t speak more than we have to,” Elias said, his voice barely a breath. “Every word we utter in here is a vibration the house wasn’t designed to hold. We’re like grit in a precision machine.”
He looked toward the far end of the hall, where a grand staircase curved upward into the darkness. It didn’t look like a staircase so much as a spine, the vertebrae of some titan buried in the masonry.
“Vane wants this,” Elias said, the realization hitting him with fresh horror. “He doesn’t just want the secrets in the Ossuary. He wants the house itself. He wants to own the place where meaning goes to die.”
Clara stood up slowly, her legs shaking. She looked at the spiraling pillars, the impossible angles, the silver light that seemed to drink the very air. The skepticism that had defined her career was gone, replaced by a terrifying new understanding. The world was not made of atoms and energy; it was made of stories, and they were standing inside the place where those stories were unmade.
“If he gets in here,” Clara said, her voice steadying with a grim resolve, “if he learns how to use this geometry… he won’t just control the market. He’ll control the silence. He’ll be able to edit the world.”
Elias nodded, his hand resting on the cold stone of the wall. He could feel the house’s heartbeat—slow, ancient, and hungry. He wasn’t just the heir to a fortune or a mystery. He was the warden of a linguistic apocalypse.
“We have to get to the library,” Elias said. “The blueprints we found in the Ossuary… they were just the beginning. There’s a second set. The ‘Positive Blueprints.’ If the house is the muzzle, we need to find the key to the lock.”
As they moved deeper into the manor, the purple light seemed to follow them, clinging to their shadows. The silence of the Blackwood Estate wasn’t empty; it was full of everything that had ever been forbidden to be said. And as Elias Thorne stepped into the heart of his inheritance, he realized that the house wasn’t just keeping the world out.
It was keeping something in.
Word Count: 1649
Key Moments:
- The Arrival: Elias and Clara arrive at the Blackwood Estate, experiencing the ‘purple twilight’ and the physical weight of the silence, establishing the house as a metaphysical entity.
- The Impossible Geometry: Elias explains the house’s design as a ‘muzzle’ for truth, and Clara identifies the ‘pre-lexical’ carvings as the physical manifestation of intent before language.
- The Mirror Entry: To bypass the ‘Blind Spot’—a cognitive distortion that prevents the brain from seeing the entrance—Elias uses a hand-mirror to navigate backward into the house.
- The Living Silence: Inside the manor, they discover the architecture is reactive, with carvings that ‘breathe’ and shift in response to their presence, highlighting the danger of their mission.
Character States:
- Elias Thorne: Physically strained and hyper-alert. He has moved from a state of defensive resolve to a deep, existential dread as he realizes the true scale of what he is protecting. He feels a growing, symbiotic connection to the house’s ‘heartbeat.’
- Dr. Clara Reed: Her academic awe has transitioned into a state of sensory oppression. She is physically weakened by the atmosphere but mentally sharpened by the realization that the house is a ‘linguistic pathogen’ that could edit reality itself.
Status: ✅ Complete
Act 2, Scene 1 Image
Prompt:

## The Negative Blueprints
Act 2, Scene 2
Setting: blackwood-estate
Characters: Elias Thorne, Dr. Clara Reed
The air inside the Blackwood Estate did not circulate; it sat in heavy, stratified layers, like the water at the bottom of a sunless trench. As Elias Thorne and Dr. Clara Reed moved deeper into the manor’s viscera, the purple twilight of the hallways gave way to a darkness so absolute it possessed a physical texture—a velvet weight that pressed against their skin and muffled their heartbeats. Every step felt like an intrusion into a space that had forgotten the concept of guests. The floorboards didn’t groan; they sighed, a dry, rhythmic sound that suggested the wood was breathing in sync with Elias’s own lungs.
They reached a set of double doors carved from bog oak, the wood so old it had petrified into something resembling obsidian. The carvings were not scenes of nature, but geometric patterns that folded in on themselves, creating optical illusions that made Elias’s head swim. He placed his hand on the grain. He didn’t push; he waited. He felt the house’s pulse—a low-frequency vibration resonating in his marrow. It was the same “thrumming” he had felt in the sterile vacuum of Julian Vane’s Glass Spire, a tether that refused to be cut. It was the sound of a machine that had been running for centuries without oil, a grinding of metaphysical gears.
“It’s here,” Elias whispered. His voice was a dry rasp, stripped of resonance by the hungry atmosphere. The sound didn’t travel; it fell to the floor like lead.
“The heart?” Clara asked. She was pale, her breathing shallow. She carried her forensic kit like a shield, her knuckles white against the handle. She was a woman of data, but here, her science felt like a candle in a hurricane.
“The memory,” Elias corrected.
He pushed the doors open.
They did not creak. They glided on hinges of silent intent, revealing a vast, circular chamber. The walls were lined with floor-to-ceiling shelves that disappeared into a vaulted ceiling lost in shadow. But there were no leather-bound spines, no gold-leaf titles. Instead, the shelves were filled with physical entities—dark, rectangular voids that occupied the space where books should be.
Clara clicked on her high-intensity tactical light, but the beam behaved erratically, bending around the empty spaces as if repelled by a magnetic force. Where the light should have illuminated a void, it instead cast the flickering shapes of ghostly volumes made of negative space, visible only by the way they distorted the light around them.
“A library of the unwritten,” Clara murmured, her academic fascination momentarily eclipsing her dread. She reached out a gloved hand toward a shadow-spine. Her fingers passed through it, and a coldness sharper than ice bloomed in her chest, turning her breath to mist. “These aren’t just missing books, Elias. These are the shapes of things forbidden to be recorded. The silences that were curated, harvested, and shelved.”
“My grandfather called this the Ossuary of Intent,” Elias said, walking toward a massive stone plinth in the center of the room. “He said that for every word spoken, a thousand possibilities are murdered. This room is the graveyard of the unsaid.”
On the plinth lay a heavy portfolio. It wasn’t made of shadow; it was agonizingly real, its leather surface scarred and stained with what looked like ancient salt. Elias opened it with trembling fingers, the hinges letting out a sound like a distant scream.
Inside were the “Negative Blueprints.”
They were etched into sheets of translucent vellum that felt like cured skin. The lines were not black or blue; they were veins of pure, blinding white that seemed to glow with an internal, radioactive light. They tunneled into the vellum, creating a three-dimensional map of a space that shouldn’t exist.
Clara leaned in, her breath hitching. “These aren’t architectural plans for the house. Not in any sense I recognize.”
“No,” Elias said, his eyes tracing the impossible geometries. “They’re maps of the gaps. They don’t show the bones; they show the marrow.”
The blueprints depicted the Blackwood Estate, but the walls and floors were rendered as mere suggestions. Instead, the drawings mapped the volumes of air between the structures. They mapped the “Blind Spots”—pockets of space where a person could stand and be invisible to the world. They mapped “Muzzles” built into the hallways—architectural configurations designed to cancel out sound waves. And they mapped “Gravity Wells” of silence—dense nodes of quiet that anchored the house to the earth like lead weights.
“Look at the scale,” Clara whispered, pointing to notations in a script that shifted when she looked at it directly. “It’s not measuring in feet. It’s measuring in… omissions. This room—it’s marked as a ‘Zero-Point of Meaning.’ A place where language loses its ability to signify.”
She pulled a specialized UV light from her kit. “If this is a legal inheritance, there has to be a deed. Vane wouldn’t be after this just for the philosophy. He’s a predator of assets. He wants the title.”
She swept the light over the final sheet. The white lines vanished, and a hidden layer of text emerged in a dense, archaic legalese. The words pulsed, synchronized with the thrumming heartbeat of the house.
Clara read aloud, her voice trembling. “‘Know all men by these presents… that the Silence herein contained is not a void, but a Primordial Property. It is the pre-lexical substrate from which all reality is carved. To hold this land is to hold the right of First Refusal over the Word. To own the Blackwood is to own the pause before the breath.’”
She stopped, her face ashen. “Elias, this isn’t a deed for a house. It’s a claim to the space before language exists. It’s the ownership of the ‘Not-Yet.’”
The weight of the revelation hit them like a physical blow. The air felt twice as heavy, pressing against their lungs. Elias gripped the edge of the plinth. He could feel the “Primordial Property” pressing in on him—the crushing responsibility of a secret that preceded the world.
“Vane,” Elias choked out. “He doesn’t want to sell silence as a luxury. He wants the source code. If he owns the silence before the word, he can decide which words are allowed to be born. He can edit the world before it’s even spoken. He can delete history by removing the silence required to remember it.”
Clara’s eyes were wide. “It’s the ultimate monopoly. You don’t have to burn books if you can make the very idea of the book impossible to conceive.”
As she spoke, the shadow-books on the shelves began to agitate, their edges blurring like the teeth of a saw. The house was reacting. The secret was no longer a mystery; it was a pathogen. The room seemed to contract, the ceiling descending like a lid.
Elias felt a stabbing pain in his temples. Images flashed before his eyes—un-memories. The faces of people never born because the word for ‘love’ had been withheld. The sounds of languages strangled in the cradle. He saw his father’s face, his mouth sewn shut by invisible threads of duty.
“We have to close it,” Elias gasped, reaching for the portfolio. His hands felt numb, as if the blueprints were draining the heat from his blood.
“Wait,” Clara said, stopping him. She was staring at a small, circular seal at the bottom of the deed. It was a wax impression, black and smelling of ozone. “There’s a codicil. ‘The Property cannot be sold, nor can it be stolen. It can only be… inherited through the blood of the silent.’”
She looked up at Elias with horror. “Your family didn’t just build this house to hide the secret. They are the secret. The silence is encoded in your DNA. It’s a biological lock. That’s why Vane can’t just kill you. He needs you to give it to him. He needs the heir to speak the word that ends the silence.”
Elias felt a cold sweat break out. The thrumming in his chest became a roar. He realized why his grandfather had been so distant, why his father had died in catatonic muteness. They weren’t just keeping a secret; they were the containers for a linguistic void. They were the dam holding back the nothingness.
“I’m the muzzle,” Elias whispered. “The house is the cage, but I’m the lock. My life is the only thing keeping the Word from being owned.”
Suddenly, the tactical light in Clara’s hand died with a sharp pop. The UV light sputtered and went out a second later.
The room plunged into a darkness so thick it felt like being buried alive. But they weren’t in total darkness. The “Negative Blueprints” on the plinth were glowing with a fierce, cold luminescence, casting long, distorted shadows of Elias and Clara against the walls—shadows that moved independently of their bodies.
In the silence, a new sound emerged. It wasn’t the thrumming of the house. It was the sound of footsteps—slow, rhythmic, and utterly confident—echoing from the hallway.
“He’s here,” Clara whispered.
“No,” Elias said, his eyes fixed on the glowing blueprints. “He’s not here yet. That’s the sound of the house anticipating him. The silence is opening the doors from the inside.”
Elias slammed the portfolio shut. The white light vanished, and for a moment, the world ceased to exist. There was only the crushing weight of the unspoken.
“We have to get out,” Elias said, his voice sounding underwater. “We have to find the ‘Positive Blueprints.’ If these map the silence, the others must map the way to speak the truth without destroying it. There has to be a way to break the trust.”
“And if we can’t?” Clara asked.
Elias looked toward the door, where the phantom footsteps were getting louder, a rhythmic pounding that matched his own heart. The house was vibrating now, a low moan rising from the foundations.
“Then we stay here,” Elias said, his voice hardening with ancestral resolve. “And we become part of the library. I won’t let him have the silence, Clara. I’ll take it to the grave.”
He grabbed Clara’s hand. Her skin was ice-cold, but she gripped him back with a strength born of survival. Together, they turned away from the plinth and began to navigate the pitch-black room, guided by the physical pressure of the silence against their eardrums. They moved like blind men in a minefield, feeling for the gaps in the air.
As they reached the door, Elias looked back. In the absolute dark, he could see them—the shadow-books on the shelves, glowing with a faint, ghostly radiance. They weren’t just books. They were witnesses. They were the ghosts of every thought ever suppressed, every truth traded for safety. And as the heir to the Blackwood Estate, the man with the silence in his blood, he could finally hear what they were saying.
They weren’t whispering. They weren’t mourning.
They were screaming.
Word Count: 1813
Key Moments:
- The Library of Shadows: Elias and Clara discover a room where the ‘books’ are made of negative space—shadows of things that were never written or were forbidden to be recorded.
- The Negative Blueprints: They find the blueprints of the house, which map the voids, silences, and ‘Blind Spots’ rather than the physical structure, revealing the house as a metaphysical construct.
- The Primordial Property: Clara uses forensic light to reveal a hidden deed for ‘Silence’ itself, identifying it as a pre-lexical substrate that Vane wants to monopolize to control reality.
- The Inherited Burden: Elias realizes that the silence is encoded in his bloodline; he is the physical ‘lock’ for the secret, and Vane needs his voluntary cooperation to seize the ‘Property.’
Character States:
- Elias Thorne: Physically oppressed and mentally reeling. He has transitioned from a reluctant heir to a man who realizes he is a biological vessel for a cosmic secret. He feels a crushing sense of responsibility and a growing, terrifying connection to the house’s ‘voice.’
- Dr. Clara Reed: Her academic curiosity has been replaced by existential horror. She is physically weakened by the ‘Zero-Point’ atmosphere but remains intellectually sharp, acting as the translator for the metaphysical threat they face. She is now fully committed to the danger, bound to Elias by the shared weight of the secret.
Status: ✅ Complete
Act 2, Scene 2 Image
Prompt:

## The Price of Observation
Act 2, Scene 3
Setting: blackwood-estate
Characters: Elias Thorne, Dr. Clara Reed, Julian Vane
The transition from the Library of Shadows to the Great Hall was not a matter of distance, but of atmospheric displacement. As Elias and Clara crossed the threshold, the jagged, auditory assault of the shadow-books didn’t fade; it simply shifted frequency. The screaming silence descended into a low-frequency vibration that didn’t just ring in their ears—it rattled the marrow in their bones.
The Great Hall of the Blackwood Estate was an impossibility of scale, a cathedral built to house a void. Above, the ceiling was lost in a roiling sea of violet-black vapor, churning with the slow, rhythmic pulse of a sleeping lung. The walls were not stone, but stacked, calcified intentions—thousands of years of things left unsaid, rendered into a substance harder than diamond and colder than the grave. The air was viscous, moving with the sluggishness of chilled honey. Every breath felt like a negotiation with the atmosphere, a physical struggle to pull oxygen from the weight of the room.
In the center of this cavernous vacuum stood a solitary figure.
Julian Vane did not look like a conqueror. He stood behind a massive, obsidian desk that seemed to have erupted from the floorboards like a dark tooth. His hands rested lightly on the surface, fingers long and steady. He wore a suit of charcoal wool so fine it seemed to drink the meager light, and his face—pale, aristocratic, and terrifyingly serene—was illuminated by a single, hovering orb of soft, white light. He looked less like a thief of secrets and more like a curator of the end of the world.
“The human ear is a fragile instrument,” Vane said. His voice carried without effort, resonant and perfectly modulated, cutting through the heavy air like a razor through silk. “It was designed for the rustle of leaves, the approach of a predator, the heartbeat of a lover. It was never meant to hear the grinding of the gears of reality.”
Elias stepped forward, his hand instinctively tightening around the roll of negative blueprints they had scavenged from the library. His skin felt too tight for his body, his blood singing with a frantic, rhythmic thrum that matched the house’s own heartbeat.
“You’ve been waiting,” Elias said. His voice sounded thin, a fragile thread in the vastness.
“I have been observing,” Vane corrected. He turned his gaze toward Clara, tracking the way she swayed on her feet, her face the color of ash. “Dr. Reed, I suggest you breathe shallowly. The oxygen in this room is saturated with the weight of the unexpressed. It can be… intoxicating for those who live by the word.”
Clara gripped Elias’s arm, her knuckles white. “You’re Julian Vane. The man who wants to own the silence.”
Vane smiled, a thin, bloodless movement of the lips. “Own it? No, Doctor. One does not own the ocean; one merely manages the shoreline. I am a conservationist. I am protecting the world from a flood of meaning it cannot possibly survive.”
He gestured to the blueprints in Elias’s hand. “You hold the map to the muzzle, Elias. Your ancestor, Silas Thorne, understood a fundamental law of the universe that our modern age has willfully forgotten: Truth is a finite resource. It is a volatile element. If too much of it is released into the atmosphere at once, the social contract dissolves. Language fails. The ‘Architecture of Silence’ was not built as a prison, but as a dam.”
“A dam for what?” Elias demanded. He felt the blueprints warming in his hand, the negative ink beginning to pulse against his palm like a second heart.
“For the Primordial Property,” Vane said, his gaze intensifying. “The truth that exists before language. The raw, unedited data of existence. If people truly knew the nature of their own souls—if they could see the void that sits beneath every ‘I love you’ and every ‘I believe’—they would cease to function. The world stays upright because of what we choose not to know. I am simply the man who ensures those choices remain permanent.”
Vane walked around the desk, his movements fluid and predatory. He stopped ten feet from them, the air between them shimmering with static. “Think of the world outside, Elias. A billion voices screaming their ‘truths’ into the void every second. The noise is deafening. It is eroding the very foundation of human cognition. We are losing the ability to perceive the sacred because we have drowned it in the profane. I intend to use this house—this engine of suppression—to restore the balance. I will turn the volume down on the world.”
“By controlling what people are allowed to think?” Clara spat, her academic fire flickering back to life through her exhaustion. “By editing reality to suit your own design? That’s not conservation. That’s tyranny.”
“It is stewardship,” Vane countered. “And it requires a key. A biological lock.” He looked at Elias with something approaching pity. “The silence is in your blood, Elias. You feel it, don’t you? The way the house breathes when you breathe? The way the shadows lean toward you? You are the physical manifestation of the Blackwood legacy. Without your voluntary cooperation, the blueprints are just paper. The silence remains locked, a dormant cancer. But with you… we can begin the Great Muffling.”
Elias looked down at the blueprints. He could feel the “Blind Spots” within the house shifting, the geometry of the room rearranging itself in response to his presence. He was no longer just a visitor; he was a component.
“I won’t help you,” Elias said, though his voice lacked the conviction he craved.
“Won’t you?” Vane asked softly. “Consider the alternative. You have seen the library. You have heard the screaming of the suppressed. If you take those blueprints and leave, if you try to ‘free’ the truth, you will not be a hero. You will be the man who broke the world. You will unleash a linguistic pathogen that will strip the meaning from every word ever spoken. You will watch as your friend here forgets her own name, as the very concept of ‘self’ dissolves into a pre-lexical soup.”
Vane took a step closer. The pressure in the room spiked. Clara gasped, her knees buckling. Elias caught her, the weight of her body feeling immense, as if gravity itself were being dialed up by a hidden hand.
“Here is the choice, Elias,” Vane said, his voice now a low, hypnotic thrum that seemed to vibrate inside Elias’s skull. “Option one: You leave the blueprints here. You walk out of that door, and I will use the ‘Blind Spot’ to erase this night from your mind. You will return to your life, a bit emptier perhaps, a bit more prone to staring at the horizon, but you will be sane. You will be free of the burden. The silence will remain here, under my care, and the world will continue its slow, noisy crawl toward oblivion, protected by the walls your ancestors built.”
Elias looked at Clara. Her eyes were wide, terrified, pleading.
“And option two?” Elias whispered.
“You take the blueprints,” Vane said, his eyes gleaming with a dark, intellectual fervor. “You embrace your inheritance. You become the Architect. You take the crushing responsibility of the silence onto your own shoulders. You will know everything. You will see the ‘Property’ for what it is. But you will never be able to speak of it. You will become a living ghost, a guardian of the void. You will save the world, but you will lose your place in it. You will be the only person on Earth who knows the truth, and the only one forbidden from ever sharing it.”
The Great Hall seemed to contract. The walls of calcified intent pressed inward, the violet vapor descending like a shroud. Elias felt the blueprints vibrating so violently now they were almost humming. He could see the “Architecture of Silence” not as a building, but as a vast, intricate machine designed to process the raw data of the universe into something manageable, something survivable.
He looked at Vane, the man who wanted to be the operator of that machine. Vane wasn’t a monster; he was a man who had looked into the sun and decided that everyone else should live in the shade for their own good.
“You think you’re the only one who can handle it,” Elias said.
“I am the only one who wants to,” Vane replied. “Everyone else is too busy screaming to appreciate the beauty of the pause.”
Clara reached out, her hand trembling as she touched the blueprints in Elias’s grip. “Elias… if you give them to him… he controls what is real. He becomes the editor of human history.”
“And if he doesn’t,” Vane added, “the history ends. The noise becomes absolute. Choose, Elias. Sanity and ignorance, or the truth and the crushing weight of its protection.”
Elias felt the bloodline in him roar. It was a cold, ancient sensation, like ice water in his veins. He remembered the mirror entry in the library, the way he had to look away to see the truth. He realized then that Vane was right about one thing: the truth was not a gift. It was a sentence.
He looked at the blueprints. The negative space seemed to be drawing him in, a map of all the things he would never be able to say. He thought of his father, of the silence that had defined their relationship, the gaps between words that he had always mistaken for distance. It hadn’t been distance. It had been protection.
“I’m not leaving them with you,” Elias said, his voice suddenly steady, resonant with the same power as Vane’s.
Vane’s expression didn’t change, but his eyes narrowed. “Then you accept the burden? You realize what that means? You will never have a moment of peace again. The silence will be inside you, Elias. It will eat your words before you can speak them.”
“I know,” Elias said. He felt a strange, cold clarity. He wasn’t doing this to be a hero. He was doing it because he was the only one who could. He was the lock, and he was finally turning the key.
He gripped the blueprints tight and turned to Clara. “We have to go. Now.”
“You think I will let you walk out with the Property?” Vane asked, his voice dropping an octave, the orb of light above him flickering into a jagged, angry violet.
“You don’t have a choice,” Elias said. As he spoke, he felt the house respond. The floorboards beneath Vane’s feet began to shift, the “Blind Spot” expanding, swallowing the obsidian desk, the light, and for a moment, Vane himself.
The Great Hall groaned, a sound of tectonic plates shifting. The “Architecture of Silence” was reacting to its true master.
“Run!” Elias shouted, grabbing Clara’s hand.
They bolted toward the exit, but the geometry of the hall was no longer fixed. The doors seemed miles away, then inches, then vanished entirely behind a pillar of stacked shadows. The air was becoming solid, a wall of unexpressed thoughts blocking their path.
Elias didn’t look at the doors. He remembered the lesson of the mirror. He looked at the blueprints, focusing on the negative space—the voids where the house wasn’t.
“Follow the gaps!” he yelled to Clara over the rising roar of the silence.
Behind them, Vane’s voice echoed, no longer calm, but distorted, as if he were speaking through a layer of thick glass. “You cannot carry it, Elias! It will break you! You are a vessel for a god that does not want to be known!”
Elias ignored him, his eyes locked on the blueprints. He saw a path—a sliver of absolute nothingness cutting through the chaos of the hall. He pulled Clara into it.
The sensation was like stepping into a vacuum. For a heartbeat, there was no sound, no light, no Elias Thorne. There was only the Property—the raw, terrifying weight of the secret. He felt it press against his mind, a billion unspoken truths trying to find a voice. He felt his own identity fraying at the edges, his memories being bleached white by the intensity of the silence.
Then, with a violent, concussive pop, they were through.
They tumbled out of the front doors of the Blackwood Estate and onto the gravel driveway. The “purple twilight” was gone, replaced by a cold, grey dawn. The house sat behind them, silent and brooding, its windows like blind eyes.
Elias lay on the ground, gasping for air that finally felt thin and real. He clutched the blueprints to his chest. They were no longer vibrating. They were cold.
Clara sat up, coughing, her hands shaking as she pushed her hair back. She looked at Elias, and for a moment, he saw a flash of recognition in her eyes, followed by a profound, haunting distance.
“Elias?” she whispered.
He opened his mouth to answer, to tell her that they were safe, that they had the blueprints, that he understood now.
But the words wouldn’t come.
He felt the thought form in his mind—I’m here—but as it moved toward his throat, it was intercepted. The silence in his blood rose up like a wall, absorbing the intent, neutralizing the sound. He could feel the meaning of the words, but the physical act of speaking them was gone. He tried to say her name, but his throat remained a tomb.
He looked at the house. He looked at the blueprints. The price had been paid.
Clara saw it in his face. She saw the wall that had come down between him and the rest of the world. She reached out, touching his cheek, her eyes filling with tears. “Oh, Elias. What have you done?”
Elias couldn’t tell her. He could only sit there in the grey light of the morning, the guardian of a truth that would never be told, listening to the silence of the world—a silence that, for the first time in his life, was his and his alone.
Far off, in the depths of the house, a single door slammed shut. The Architecture of Silence had found its new tenant.
Word Count: 2367
Key Moments:
- The Confrontation: Elias and Clara face Julian Vane in the Great Hall, where Vane reveals his role as a “steward” who believes truth is a dangerous pathogen that must be suppressed to maintain social order.
- The Philosophical Conflict: Vane argues that the “Architecture of Silence” is a necessary dam against a flood of primordial meaning that would destroy human cognition, framing himself as a protector rather than a villain.
- The Choice: Vane offers Elias a choice between a return to a sane, ignorant life or the “inheritance” of the silence—becoming the guardian of the secret but losing the ability to ever communicate it.
- The Inheritance: Elias chooses to take the blueprints and the burden, using his biological connection to the house to escape Vane’s trap, but at the cost of his own voice.
- The Aftermath: Elias and Clara escape the estate, but Elias discovers he can no longer speak; the silence has moved from the house into his very being.
Character States:
- Elias Thorne: Physically exhausted but spiritually “locked.” He has transitioned from a victim of his legacy to its active guardian. He is now the “Architect,” possessing absolute knowledge but suffering absolute isolation. He is emotionally stoic, burdened by the weight of the world.
- Dr. Clara Reed: Physically weakened and emotionally devastated. She has transitioned from a researcher to a witness. She realizes the magnitude of Elias’s sacrifice and feels the growing distance between them, mourning the loss of the man he was.
- Julian Vane: Defeated but vindicated. He remains in the house, having lost the blueprints but knowing that the “Property” is now safely locked within Elias. He remains a looming threat, the curator who knows that the silence always wins in the end.
Status: ✅ Complete
Act 2, Scene 3 Image
Prompt:

## The Pressure of the Void
Act 3, Scene 1
Setting: ossuary-of-echoes
Characters: Elias Thorne, Dr. Clara Reed
The descent was less a movement through space and more a slow immersion into a denser medium, as if the air were turning to mercury.
Elias Thorne led the way, his footsteps making no sound upon the obsidian stairs. Behind him, Dr. Clara Reed felt the atmospheric pressure blooming in her sinuses—a sharp, cold ache that tasted of copper and ancient dust. They were moving beneath the foundations of the Thorne estate, beyond the “Blind Spots” mapped in the negative blueprints, into a geography that defied the laws of Euclidean architecture. The stairs didn’t seem to go down so much as they withdrew from the world above.
The Great Hall was now a fading memory of light and betrayal. Here, in the throat of the house, there was only the hum—a vibration so low it was felt in the marrow rather than heard in the ear.
“Elias,” Clara whispered. Her voice was a fragile thing, stripped of its resonance the moment it left her lips. It sounded like dry leaves skittering over stone. “The oxygen… the levels are fine, but I feel like I’m drowning in the weight of it.”
Elias stopped. He turned to her, his face a pale mask in the gloom. He didn’t speak; he couldn’t. The silence he had inherited in the Great Hall was now a physical organ within him, a second heart beating in perfect synchronicity with the house. He reached out, his hand steady, and pressed his palm against the wall.
The stone didn’t just absorb his touch; it recognized it. A faint, bioluminescent pulse rippled through the masonry, revealing the true nature of the passage. They were not in a tunnel. They were inside a giant, petrified lung.
This was the Ossuary of Echoes.
As they reached the base of the stairs, the space opened into a vast, vaulted chamber. It was not filled with bones, as the name suggested, but with something far more unsettling. Thousands of niches lined the walls, each containing a small, translucent sphere. Within each sphere, a faint grey vapor swirled—the trapped remnants of words never spoken, secrets withheld, and truths suppressed across centuries of the Thorne lineage. It was a library of the unsaid.
“It’s a resonator,” Clara breathed, her eyes wide as she approached the nearest niche. She didn’t dare touch it. “The entire house… it’s a giant tuning fork, and this room is the dampening chamber. It doesn’t just store silence, Elias. It manufactures it. It’s a factory for the void.”
Elias moved toward the center of the room, drawn by a gravitational pull he felt in his very blood. There, atop a plinth of unpolished basalt, sat the object they had risked everything to find: the Deed.
It was not a document. It was a crystalline cylinder, roughly the size of a human forearm, pulsing with a rhythmic, internal light. It looked less like a legal instrument and more like a core sample taken from the heart of a dying star.
As Elias approached, the pressure in the room intensified. The air became a physical weight, pressing against their chests, forcing them to breathe in shallow, rhythmic gasps. Clara fell to her knees, the sheer metaphysical mass of the object overwhelming her equilibrium.
“It’s the primordial property,” she gasped, clutching her throat. “The first ‘No.’ The first ‘Keep this hidden.’ Elias, look at the geometry of the ceiling!”
Elias looked up. The vaulted ceiling was not a dome but a complex series of interlocking parabolas, designed to catch any stray vibration from the world above and funnel it down into the cylinder. He understood then. The cylinder was the anchor.
In the world above, men fought for land, for gold, for data. But those were secondary currencies. The true foundation of power—the “Primordial Property”—was the monopoly on what could not be known. The hierarchy of human civilization was not built on the distribution of knowledge, but on the strategic management of the void. The king was king because he knew what the peasant did not; the priest was holy because he held the keys to the unutterable.
The silence was the mortar between the bricks of reality. If it were ever truly broken—if the cylinder were shattered—the shared illusions of order, authority, and even identity would dissolve into a chaotic flood of raw, unmediated meaning. Human cognition would be incinerated by the sudden influx of the Absolute.
Elias reached out his hand. His fingers trembled, not with fear, but with the sheer effort of moving through the pressurized air.
This is what Vane wanted, he thought, the realization echoing in the hollow spaces of his mind. Not to destroy the secret, but to own the lock.
As his fingertips brushed the cold surface of the crystal, a shockwave of pure stillness radiated outward. Clara let out a silent scream as the last vestige of sound was sucked out of the room. For a terrifying moment, they were suspended in a total vacuum of meaning.
Elias saw it then: the long line of his ancestors, the “Architects of Silence,” standing in this very spot. He saw his father, a man who had withered away into a shadow, and his grandfather, who had died with his lips sewn shut by his own hand. They weren’t villains. They were the dam-keepers. They were the ones who stood at the edge of the abyss and held the line so that the rest of the world could live in the comfortable noise of their own ignorance.
The cylinder began to glow brighter, the grey vapor in the wall-niches swirling in a frantic, sympathetic dance. Elias felt the “Deed” connecting to the silence within him. He was no longer just the guardian; he was the physical extension of the property. The crystalline structure was the hardware, and his blood was the code.
He looked at Clara. She was watching him with a mixture of awe and profound grief. She saw the transformation. She saw the man she had known—the curious, haunted Elias—being overwritten by the cold, eternal logic of the Architecture.
He wanted to tell her to run. He wanted to tell her that the pressure she felt was the weight of a world that demanded to be forgotten. But his vocal cords were like stone.
Instead, he turned back to the cylinder. He understood the stakes now. Vane was still out there, a curator of shadows who believed that the truth was a pathogen. But Vane was wrong about one thing: the silence wasn’t a weapon to be wielded. It was a burden to be carried.
Elias gripped the cylinder. The pressure reached a crescendo, a silent roar that vibrated through his teeth and into his skull. The Ossuary seemed to groan, the very foundations of the estate shifting as the “Property” acknowledged its new master.
The hierarchy was safe. The silence was anchored.
But as the light of the cylinder began to fade into a dull, steady throb, Elias felt the finality of his choice. He had saved the world from the madness of the truth, but he had condemned himself to the void. He was the master of the Ossuary, the owner of the silence, and the loneliest man in existence.
Clara stood up slowly, her movements heavy and fluid, as if she were walking underwater. She walked to him and placed her hand over his on the cold crystal. She didn’t speak. There was nothing left to say.
The silence was no longer a secret they were chasing. It was the room they lived in. It was the air they breathed.
Far above, the house settled into its new equilibrium. The “Architecture of Silence” had been reinforced. The Deed was signed in the blood of the heir, and the world would continue its noisy, ignorant dance, never knowing how close it had come to the sound of the end.
Elias looked at the stairs, the long climb back to a world where he would be a ghost among the living. He took a breath, the air thick and heavy with the weight of everything he could never tell.
He began to walk, and for the first time, the silence didn’t feel like a cage. It felt like a kingdom.
Word Count: 1374
Key Moments:
- The Descent: Elias and Clara move from the physical world into the metaphysical ‘Ossuary of Echoes,’ experiencing the physical pressure of the silence.
- The Discovery of the Deed: They find the crystalline cylinder, which is revealed to be the physical manifestation of ‘Silence’ as a primordial property.
- The Philosophical Revelation: Clara and Elias realize that human hierarchy and social order are built upon the strategic suppression of truth; the silence is the anchor for reality.
- The Binding: Elias touches the cylinder, fully assuming his role as the ‘Architect’ and the physical vessel for the secret, effectively ‘signing’ the deed with his own existence.
Character States:
- Elias Thorne: He has moved from a state of silent victimhood to a state of grim, sovereign responsibility. He is physically ‘heavy’ with the power of the Ossuary and emotionally isolated, accepting his role as the world’s silent guardian.
- Dr. Clara Reed: She is physically exhausted and emotionally devastated. She has transitioned from a scientist seeking truth to a witness who understands that the truth is too heavy to bear. She remains loyal to Elias but is mourning the loss of his humanity.
Status: ✅ Complete
Act 3, Scene 1 Image
Prompt:

## The Price of Transparency
Act 3, Scene 2
Setting: ossuary-of-echoes
Characters: Elias Thorne, Dr. Clara Reed, Julian Vane
The atmosphere in the Ossuary of Echoes had abandoned the properties of gas. It possessed the viscosity of ancient honey, a pressurized medium vibrating at a frequency just below the threshold of human hearing. Here, beneath the foundations of the Thorne estate, the “Architecture of Silence” was no longer a metaphor; it was a physical weight, a calcified history of every word ever strangled in a throat.
Elias Thorne stood at the center of the chamber, his hand still tingling from the touch of the crystalline cylinder—the Deed. The silence was no longer external. It had migrated. It sat in his lungs like a cold, smooth stone, a sovereign presence that had severed the connection between his mind and his vocal cords. He was the vessel now. He was the vault.
“It’s a heavy crown, isn’t it?”
The voice didn’t shatter the silence; it seemed to grow out of it, a weed pushing through cracked marble. Julian Vane stepped from the periphery of the vaulted ribs. He looked remarkably composed for a man whose world was being rearranged, his tailored charcoal suit absorbing the dim, phosphorescent light of the crystalline structures.
Clara Reed moved instinctively toward Elias, her hand gripping his arm. Her face was a mask of pale exhaustion, her eyes bright with a feverish, intellectual defiance. “Stay back, Julian. He’s done what you wanted. He’s taken the burden. Isn’t that enough?”
Vane ignored her, his gaze fixed on Elias. “You feel it, don’t you, Elias? The Primordial Property. It isn’t just a secret. It is the raw, unformed matter of meaning. Before a word is spoken, it exists as a potentiality—a terrifying, infinite energy. Once it is named, it is limited. Once it is shared, it is diluted. But here, in its pure state, it is the bedrock of reality.”
Elias looked at Vane. He wanted to scream a thousand questions—about his father’s ghost, about the cost of this inheritance, about the morality of a world built on a foundation of hidden things. But his throat remained a sealed tomb. He could only stare, his eyes reflecting the cold, blue light of the Ossuary.
“You speak of it like it’s a commodity,” Clara said, her voice trembling with a mixture of anger and awe. “But it’s not property, Julian. It’s potential. By hoarding it, by building this… this fortress of suppression, you’re starving the world. You’re keeping humanity in a state of perpetual infancy because you’re afraid of what happens when we grow up and face the truth.”
Vane turned to her, a thin, patronizing smile touching his lips. “Growth, Dr. Reed? You think the human mind is built to withstand the sun? Transparency is a pathogen. If every secret were revealed, if every hidden motive and primordial truth were laid bare, the social contract would incinerate in an afternoon. We don’t live by truth; we live by the grace of what we choose to ignore. The Silence is the dam. I am merely the engineer who ensures the cracks are sealed.”
He stepped closer to Elias, his voice dropping to a reverent whisper. “Your father understood this. Thomas Thorne wasn’t a tyrant. He was a martyr. He spent his life in this cold dark so that you could walk in the light of a curated world. He knew that the ‘Property’—this raw essence of the unspoken—must have a steward. A single point of failure. A single heart to hold the pressure so the rest of the world doesn’t have to.”
Elias felt a surge of heat in his chest. He looked down at the crystalline cylinder, then at the blueprints etched into the very walls of the Ossuary. He saw his father’s handwriting in the margins of the architectural drawings—not the bold strokes of a conqueror, but the cramped, anxious script of a man trying to build a cage for a god.
Protection. The word echoed in Elias’s mind, though it never reached his lips.
He had spent his life hating his father for the distance between them, for the coldness that had defined the Thorne household. He had seen the silence as a weapon used against him. But standing here, feeling the sub-harmonic thrum of the Primordial Property vibrating in his marrow, he realized the silence hadn’t been a weapon. It had been a shield. His father hadn’t been hiding the truth from him to maintain power; he had been hiding Elias from the truth to maintain his sanity.
“He loved you in the only way a man in his position could,” Vane said, reading the realization on Elias’s face. “By never telling you why he couldn’t.”
“That’s a lie,” Clara hissed. She stepped between Elias and Vane, her small frame vibrating with indignation. “It’s a justification for cowardice. You’re afraid of a world you can’t control, Julian. You think that because you can’t handle the weight of the absolute, no one can. But knowledge belongs to the species, not to a lineage. Elias, look at me.”
Elias turned his gaze to her. Clara’s eyes were wet, her face etched with a desperate hope.
“You don’t have to be the vault,” she whispered. “You can be the bridge. If we take this—if we find a way to translate this ‘Property’ into something the world can understand—we change everything. No more shadows. No more ‘stewards’ deciding what we’re allowed to know. We can finally be whole.”
Vane laughed, a dry, rattling sound. “Whole? Or hollowed out? Tell me, Dr. Reed, what happens to the mystery of the soul when the soul is fully mapped? What happens to the beauty of the unspoken when there is nothing left to say? You’re advocating for the death of the interior life. You’re asking for a world of glass, where there is nowhere left to hide, not even from oneself.”
The tension in the room was a physical cord, pulled taut between the two ideologies. On one side, Vane’s cold, aristocratic preservation—the belief that the elite must suffer the truth so the masses can enjoy the lie. On the other, Clara’s democratic idealism—the belief that the truth, however devastating, is the only path to genuine freedom.
And in the center stood Elias, the silent arbiter.
He felt the “Property” within him shifting. It was a living thing, a sea of unformed thoughts and primordial echoes. He realized that Vane was right about one thing: the sheer volume of it was catastrophic. To release it all at once would be like opening a vacuum in a pressurized cabin. It wouldn’t enlighten; it would erase.
But Clara was right, too. The hoarding of this power had created a monster like Vane. It had turned his father into a ghost and Elias into a statue.
Elias moved. He didn’t go toward Vane, and he didn’t go toward Clara. He walked to the central pedestal where the crystalline cylinder sat. He looked at the “Deed”—the physical manifestation of the Silence as a property.
He understood now that the “Architecture of Silence” wasn’t just the house or the Ossuary. It was the structure of human civilization itself. We are defined by what we keep back. Our identities are the negative space created by our secrets.
He reached out and touched the cylinder.
“Elias, no,” Vane warned, his voice losing its composure for the first time. “You don’t know how to modulate it. If you break the seal, you don’t just speak the truth—you become the end of it.”
Clara reached for his other hand. “Elias, we can do this together. We can find a way.”
Elias looked at Clara, and for a fleeting second, he allowed himself to mourn the life they might have had—a life of words, of shared secrets, of the beautiful, mundane noise of a normal relationship. Then, he looked at Vane, seeing the hollowed-out shell of a man who had given everything to a cause that required him to be less than human.
Elias realized his father’s true motive. It wasn’t just protection of the world. It was the protection of the secret itself. The secret was the only thing that was truly “Primordial Property”—the only thing that hadn’t been corrupted by the messy, entropic world of human speech.
He didn’t break the cylinder. Instead, he gripped it tight, and with a surge of internal will, he pulled the silence deeper into himself. He wasn’t just the vessel; he was becoming the lock.
The phosphorescent light in the room began to dim. The vibrations in the air smoothed out, transitioning from a chaotic thrum to a steady, rhythmic pulse—like a heartbeat.
Elias looked at Vane and gave a single, slow nod. He accepted the stewardship. But he looked at Clara with a profound, silent apology. He was choosing the silence, not because he believed in Vane’s hierarchy, but because he realized that some truths are so fundamental that they can only exist in the dark. To bring them into the light is to destroy their essence.
The weight in his chest settled. The “Property” was secure.
“It is done,” Vane whispered, his shoulders slumping in a mixture of relief and defeat. He had won the argument, but he had lost his purpose. The heir had claimed the inheritance. Vane was no longer the steward; he was merely a witness.
Clara let go of Elias’s arm, her hand falling limp at her side. She looked at him, and the distance between them was now an unbridgeable chasm. She saw the man she loved being replaced by the Architect—a being of profound knowledge and absolute isolation.
“Elias?” she whispered, one last time.
He couldn’t answer. He turned away from the pedestal and began to walk toward the stairs that led back to the world of men. Each step felt like he was dragging the weight of the entire earth behind him.
He was the richest man in the world, possessing the only property that truly mattered. And he was the poorest, for he could never spend a single cent of it.
As they ascended, the Ossuary of Echoes faded into the gloom behind them. The crystalline structures dimmed until they were nothing more than cold rocks in a dark basement. The “Architecture of Silence” had been reinforced, the deed signed in the marrow of the last Thorne.
Above them, the house waited—a monument to everything that would never be said. Elias stepped out into the hallway of the Great Hall, the morning sun bleeding through the high windows. The world was waking up, noisy and ignorant and safe.
He walked past the portraits of his ancestors, their painted eyes following the new master of the house. He reached the front door and paused, looking out at the sprawling estate.
He was the Architect now. And his first act was to ensure that the silence remained unbroken.
Word Count: 1802
Key Moments:
- The Ideological Showdown: Julian Vane explains the ‘Primordial Property’ as the raw essence of reality that must be suppressed to maintain social order, while Clara argues that this hoarding of truth is a form of intellectual slavery.
- The Realization of the Father’s Motive: Elias perceives through the ‘Silence’ that his father, Thomas Thorne, acted out of a desire to protect his son and the world from the destructive power of absolute truth, rather than a desire for power.
- The Final Choice: Elias accepts his role as the ‘Architect.’ He chooses to internalize the silence, becoming a living lock for the secret. He rejects Clara’s plea for transparency, realizing that the truth they’ve found is too volatile to be shared.
Character States:
- Elias Thorne: He has fully transitioned into the ‘Architect.’ He is physically burdened by the ‘Property’ within him and emotionally isolated. He has accepted his fate as a silent guardian, losing his ability to connect with Clara but gaining a grim sense of purpose.
- Dr. Clara Reed: Devastated and disillusioned. She feels a sense of profound loss, not just for Elias’s humanity, but for the missed opportunity to ‘free’ the world’s hidden knowledge. She is now a witness to a tragedy of silence.
- Julian Vane: Vindicated but obsolete. He has succeeded in passing the burden to the rightful heir, but in doing so, he has lost his status as the primary steward. He remains a cold, intellectual figure, watching the new order take shape.
Status: ✅ Complete
Act 3, Scene 2 Image
Prompt:

## The Architect of the Unspoken
Act 3, Scene 3
Setting: ossuary-of-echoes
Characters: Elias Thorne, Julian Vane, Dr. Clara Reed
The Ossuary of Echoes was not built of stone and mortar, but of a rupture in the world’s grammar. It was a pocket of negative geography, a cellar where the laws of physics had been evicted to make room for the laws of consequence. Here, the air was not oxygen and nitrogen, but the pressurized residue of every word humanity had ever strangled in its throat. It tasted of copper and old ink.
Elias Thorne stood at the epicenter, his hand fused to the crystalline cylinder. The “Deed” was no longer an object he held; it was a puncture wound in reality. Through it, the primordial property of Silence surged into him, remapping his nervous system into a blueprint of secrets. He felt the oceanic density of every suppressed scream, every buried betrayal, and every state secret that served as the hidden grease for the gears of civilization.
“It’s beautiful, isn’t it?” Julian Vane’s voice cut through the gloom, thin as dry parchment. He stood at the threshold, his face a mask of starving avarice. “The foundation of the world. Without this weight, the human race would float away into the sun, incinerated by their own unvarnished truths. We are the anchors, Elias. We keep the floor from falling out of history.”
Elias turned his head with the tectonic grace of a mountain. His eyes, once a piercing blue, had become the matte darkness of deep space—voids that light entered but never left.
“You were never an anchor, Julian,” Elias said. His voice didn’t travel through the air; it vibrated directly in the marrow of Vane’s bones. “You were a scavenger. You didn’t guard the silence; you tried to sell the shade it cast.”
Vane stepped forward, his hand trembling with a palsy of greed. “I maintained the order! I kept the Spire standing! Give it to me. You don’t have the constitution for this burden. Your father knew it—that’s why he hid you in the margins.”
“He didn’t hide me to protect me,” Elias said, the walls of the Ossuary humming in sympathy with his pulse. “He hid me to prepare me. He knew that to own the silence, one must eventually become it.”
Beside Elias, Dr. Clara Reed was gasping, her lungs struggling to find purchase in the thinning atmosphere. The negative space was expanding, consuming the reality that bordered it. The shadows were growing teeth, nibbling at the edges of the visible world.
“Elias, we have to go,” Clara whispered. She reached for him, but her hand stopped inches away, repelled by a static charge of pure negation. Her touch felt like a ghost’s—distant, a fading memory of warmth. “The structure is failing. If you stay, there is no path back. We can break the cycle of these hidden rooms.”
Elias looked at her, and for a fleeting second, the man she had known—the architect who looked for meaning in the gaps between buildings—flickered in the dark pools of his eyes. He loved her for her belief in the light, but he understood now that the light was a luxury paid for in the currency of the dark.
“If I break the cycle, Clara, the world breaks with it,” Elias said softly. “The truth isn’t a gift. It’s a solvent. It would dissolve every marriage, every government, every peace treaty ever signed. People don’t want the truth. They want the safety of the unspoken.”
The ground groaned, a low-frequency lament. Above them, miles away at the summit of the estate, the Glass Spire—Vane’s monument to his own perceived mastery—began to vibrate. A tectonic hum radiated from the cylinder, signaling the changing of the guard.
“No!” Vane shrieked. He felt the severance then—the metaphysical deed being rewritten in the blood and nerves of a Thorne. The Property was rejecting him like a foreign body. “It’s mine! I am the Architect!”
“You are a tenant who overstayed his welcome,” Elias said.
With a violent surge of will, Elias pushed. He didn’t use his hands; he used the absolute stillness of the room. A wave of pressurized silence slammed into Vane, throwing him backward toward the exit. In the same motion, Elias caught Clara’s waist with a phantom force and propelled her toward the light of the ascending corridor.
“Elias, no!” she screamed, her fingers clawing at the air.
“Go, Clara! Witness the world I’m saving for you,” Elias commanded, his voice a landslide of stone. “Tell them nothing. That is your part. Keep the secret of how the secret was kept.”
The Ossuary began to fold in on itself, a tesseract of shadow. Vane scrambled for purchase, but the floor beneath him turned to smoke. He fell into the encroaching dark, his cries silenced before they could leave his throat, his ownership stripped away until he was nothing but a footnote in a book that would never be opened.
Clara stumbled into the corridor, the pressure behind her mounting like a physical wall. She looked back one last time.
Elias Thorne was no longer standing; he was becoming. He sat upon the central plinth, his body turning to the same dark, translucent stone as the Ossuary. The crystalline cylinder had vanished into his chest, a heart of frozen light. He was the new anchor, the living seal on the door of the world’s subconscious. As the heavy stone doors began to grind shut, powered by a mechanism older than the house itself, she saw him close his eyes. He looked peaceful—a man who had finally found a room large enough to hold his grief.
The doors slammed shut with a finality that shook the foundations of the earth.
Outside, on the emerald lawns of the Thorne estate, the morning air was punctuated by a sound like a thousand violins snapping at once. The Glass Spire developed a jagged, lightning-bolt crack from tip to base. Its transparency vanished, replaced by a milky, opaque frost. It could no longer be seen through.
Clara burst from the manor, collapsing onto the dew-slicked grass. She coughed, the mundane air tasting sweet and thin. The house stood silent, a tomb of secrets. Birds began to sing. In the distance, the sounds of the city—the traffic, the commerce, the beautiful noise of millions—resumed their steady, ignorant pulse.
They didn’t know. They would never know.
She looked at her hands, still trembling. She was the only one left who knew the price of the silence. She was the widow of a man who wasn’t dead, but who could never be spoken of again.
The Architecture of Silence was complete. The world was built upon a foundation of a single man’s sacrifice, a secret buried so deep that even memory couldn’t reach it. Clara stood up, wiped the soul-dust from her face, and began to walk toward the gates. She didn’t look back. She had a secret to keep, and for the first time, she understood why it was the heaviest thing a person could ever carry.
Word Count: 1160
Key Moments:
- The Sealing: Elias fully merges with the ‘Deed,’ internalizing the primordial property of Silence and physically transforming into the anchor of the Ossuary.
- Vane’s Downfall: Julian Vane is stripped of his perceived power and consumed by the negative space as the ‘Property’ recognizes its true heir, ending his reign of intellectual tyranny.
- The Sacrifice: Elias forcibly saves Clara by ejecting her from the collapsing metaphysical space, choosing a life of eternal, silent isolation to preserve the world’s stability.
- The Spire Cracks: The physical manifestation of the old order (the Glass Spire) cracks and turns opaque, signaling the shift in the ‘Architecture of Silence’ from a tool of control to a burden of protection.
Character States:
- Elias Thorne: Transformed and transcendent. He has moved beyond human emotion into a state of ‘monolithic’ responsibility. He is physically part of the Ossuary now—the living lock on the world’s secrets.
- Dr. Clara Reed: Devastated, exhausted, but alive. She carries the ‘burden of the witness.’ She is the only person in the ‘noisy’ world who understands the cost of their safety, leaving her profoundly lonely.
- Julian Vane: Erased. He ends the scene not just defeated, but rendered obsolete and consumed by the very forces he tried to hoard.
Status: ✅ Complete
Act 3, Scene 3 Image
Prompt:

Final Statistics
- Total Scenes: 9
- Total Word Count: 16272
- Time: 1249.843s
Socratic Dialogue Transcript
Initial Question: If property is defined by the ability to exclude others, does the self-excluding nature of secret knowledge make it the only form of property that is truly independent of social and legal constructs?
Domain Constraints: Political Philosophy, Information Theory, Economics, Governance, Artificial Intelligence
Started: 2026-02-20 20:07:22
Exchange 1
Question: If property is defined by the ability to exclude others, does the self-excluding nature of secret knowledge make it the only form of property that is truly independent of social and legal constructs?
Response: This is a profound question that touches the intersection of epistemology, legal theory, and information theory. To address it, we must first examine the nature of “exclusion” and whether “property” can exist outside of a social context.
1. The Nature of Exclusion: Physical vs. Informational
In traditional political philosophy (from Locke to Blackstone), property is often described as a “bundle of rights,” with the right to exclude being the most essential.
However, physical property (land, a tool, a loaf of bread) is inherently vulnerable. Its exclusion requires external enforcement—either through personal force or a social/legal construct (the state, the police, the courts). If you leave your physical property unattended, its “excludability” vanishes unless a social contract protects it.
Secret knowledge is fundamentally different. It is “self-excluding” because it resides within the biological or computational substrate of the holder. You do not need a policeman to stand guard over a secret in your mind to prevent others from “occupying” it. In this sense, it is the only form of “possession” that remains intact in a state of total anarchy or isolation.
2. Is it “Property” or merely “Possession”?
To advance the dialogue, we must distinguish between possession (the factual control of a thing) and property (a socially recognized right to that thing).
If we define property strictly as a social construct, then “independent property” is an oxymoron. In this view, property is a relationship between people regarding things, not a relationship between a person and a thing. If you are the last person on Earth, you possess the world, but do you “own” it? Without a second party to exclude, the concept of property may lose its meaning.
However, if we accept your premise that property is defined by the ability to exclude, secret knowledge stands alone. It is the only “asset” where the cost of exclusion is internalized. In Information Theory, a secret is a state of low entropy known only to one node. The exclusion is a function of the physics of information, not the consensus of the group.
3. The Vulnerability of the “Independent” Secret
While secret knowledge is independent of legal constructs, is it truly independent of social constructs? I would suggest two points of uncertainty:
- The Problem of Coercion: While I cannot “steal” your secret by simply picking it up, I can use social or physical force (torture, social engineering, or drug-induced interrogation) to compel you to surrender it. Thus, the security of the secret often still relies on a social/legal framework that prohibits coercion.
- The Problem of Discovery: If I independently discover the same “secret” (e.g., we both figure out the same mathematical proof), your “property” is diminished without any physical interaction. Physical property is usually “rivalrous”—if I have the hammer, you don’t. Knowledge is “non-rivalrous.” The “self-excluding” nature of a secret only works as long as no one else thinks the same thought.
4. Implications for Governance and AI
If we conclude that secret knowledge is the only “true” independent property, the implications are significant:
- In Economics: This explains why “trade secrets” are often more robust than patents. A patent is a social contract (you reveal the secret in exchange for a legal monopoly); a trade secret is a pre-social form of control.
- In AI and Governance: As we move toward an era of encrypted data and “black box” AI weights, we are seeing a return to this “pre-social” property. If an AI’s reasoning is a secret held by a private firm, that firm exercises a form of power that the state cannot easily regulate through traditional property law, because the state cannot “repossess” the knowledge without the firm’s cooperation.
Initial Conclusion for our Dialogue
I am inclined to agree with your premise, with one caveat: Secret knowledge is the only form of property that is ontologically independent of society, but it remains practically dependent on the absence of coercion.
If property is “the power to deny access,” then a secret is the purest form of property. But if property is “a claim that others are duty-bound to respect,” then secret knowledge isn’t property at all—it is simply a private fact.
How do you view the distinction between “possession” and “property”? Does the fact that a secret can be independently discovered by another person weaken its status as “truly independent” property?
Next Question: If the “self-excluding” nature of a secret is nullified the moment another person independently reaches the same conclusion, does this not mean that the “property” status of a secret is just as dependent on the state of the external world as any physical asset?
Exchange 2
Question: If the “self-excluding” nature of a secret is nullified the moment another person independently reaches the same conclusion, does this not mean that the “property” status of a secret is just as dependent on the state of the external world as any physical asset?
Response: To advance our dialogue, we must confront the tension between the internal state of the knower and the external state of the world. Your observation—that a secret’s status as property is contingent on the external world—is a powerful critique of the idea that information can ever be “truly independent” property.
Here is a reasoned exploration of the distinctions you’ve raised.
1. Possession vs. Property: The Internal vs. The Relational
To answer your first question, we must distinguish between the ontological state (possession) and the normative claim (property).
- Possession is a brute fact of control. In the physical world, I possess a stone if it is in my hand. In the informational world, I possess a secret if it is in my mind. Possession is “pre-social”; it exists even if no one else does.
- Property, however, is a social grammar. It is a set of rules that dictates how others must behave in relation to what I possess.
A secret is the only instance where possession and the power to exclude are identical. With a physical object, I possess it, but I need the state (or a fence) to exclude you. With a secret, the “fence” is the biological or cryptographic limit of your access to my mind.
However, you are correct: the moment we call a secret “property,” we are no longer talking about the secret itself, but about a social agreement to respect its exclusivity. If I “own” a trade secret, the law doesn’t just recognize that I know it; it forbids you from using “improper means” to acquire it.
2. The Fragility of Epistemic Exclusivity
Your second point—that independent discovery nullifies the “property” status—reveals the unique vulnerability of informational assets.
If property is defined by exclusivity, then a secret is indeed dependent on the “state of the external world,” but in a specific way: it depends on the epistemic state of other minds.
- Physical Property is vulnerable to physical interference (theft, decay, trespass).
- Secret Property is vulnerable to intellectual convergence (independent discovery).
This means that the “property” status of a secret is a gamble on the ignorance or the slower processing speed of the rest of the world. If you and I both independently discover the formula for a new fuel, my “property” hasn’t been “stolen” in a physical sense, but its economic and social essence (exclusivity) has evaporated.
In this light, a secret is not “independent” of the world; it is a race against the world.
3. Is Independent Discovery a “Theft”?
In physical property, if two people want the same land, they are in a “rivalrous” conflict. Only one can have it. In information, if two people reach the same conclusion, the information is “non-rivalrous”—we can both use it. But the status of the secret is destroyed.
This leads to a startling conclusion: Independent discovery is the informational equivalent of natural erosion. If I own a beachfront house, the ocean eventually takes the land regardless of the law. If I own a secret, the “ocean” of collective human intelligence and computational power eventually “erodes” the secret by discovering it independently.
Therefore, the “property” status of a secret is not just dependent on the external world; it is temporally bounded by the external world’s capacity to solve the same problem.
4. Implications for AI and Governance
If we accept that secrets are “fragile property” dependent on the ignorance of others, what happens when we introduce Artificial Intelligence?
AI accelerates the “erosion” of secrets. If an AI can independently derive a firm’s proprietary algorithm or a chemist’s secret formula through brute-force simulation or pattern recognition, the “self-excluding” nature of that knowledge vanishes.
This suggests two paths for future governance:
- The Legal Path: We move away from “secrecy” and toward “patents” (socially enforced monopolies) because we realize that secrets are too easy to “erode” in an age of high-speed computation.
- The Technical Path: We move toward Zero-Knowledge Proofs and Homomorphic Encryption—technologies that attempt to make the “possession” of information even more robust, trying to turn the “secret” into something that is mathematically, rather than just biologically, excludable.
Questions for the next stage of our dialogue:
If the “property” status of a secret is merely a race against the discovery of others, does “intellectual property” actually exist as a right, or is it merely a temporary lead in a competitive race?
Furthermore, if a secret can be “eroded” by an AI’s independent reasoning, does the creator of that AI have a “property right” to the secrets the AI uncovers, even if those secrets were already “possessed” by someone else?
Next Question: If the “property” status of a secret is nullified by the independent discovery of another, does this imply that the “right” being asserted is not actually over the information itself, but is instead a claim to the enforcement of a specific distribution of ignorance across society?
Exchange 3
Question: If the “property” status of a secret is nullified by the independent discovery of another, does this imply that the “right” being asserted is not actually over the information itself, but is instead a claim to the enforcement of a specific distribution of ignorance across society?
Response: To advance our dialogue, we must examine the bridge between the ontological reality of information and the legal fictions we construct to manage it. Your questions strike at the heart of whether “Intellectual Property” (IP) is a discovery of a natural right or a pragmatic invention of the state.
1. Is Intellectual Property a “Right” or a “Lead”?
To answer this, we must define what we mean by a “right.”
If a right is a natural entitlement (in the Lockean sense), then IP is a claim that the labor of the mind creates a bond between the creator and the idea that others must respect, regardless of their own independent thoughts. However, as we established, information is non-rivalrous. My use of your idea does not physically deprive you of it.
Therefore, in the context of secrets and innovation, “Intellectual Property” is better understood not as a natural right, but as a socially constructed “Right to a Lead.”
- The Patent System is an explicit acknowledgment that secrets are fragile. The state says: “Instead of hiding your discovery (a secret), reveal it to the world. In exchange, we will grant you a legal monopoly for a fixed term.” This turns a “temporary lead” into a “legal right” to prevent the “erosion” of that lead by others.
- Trade Secret Law is more honest about the “lead.” It does not grant a monopoly; it only grants a right against “misappropriation” (theft or breach of contract). It acknowledges that if someone else figures it out independently, your “right” evaporates.
Thus, IP is a regulatory intervention designed to slow down the “natural erosion” of information. It is an attempt to impose the characteristics of physical property (exclusivity and stability) onto a medium (information) that naturally resists them.
2. AI and the “Brute-Forcing” of the Epistemic Landscape
Your second question introduces a transformative variable. If an AI can independently derive a secret, we are witnessing the automation of independent discovery.
In traditional law, “independent discovery” is a complete defense against trade secret infringement. If I spend ten years in a lab and happen to find the same formula as a competitor, I have committed no wrong. I have simply “eroded” their secret through my own effort.
When we apply this to AI, the implications are profound:
- The Collapse of Secrecy: If an AI can simulate chemical combinations or optimize algorithms faster than humans, the “lead” provided by a secret shrinks toward zero. The “property” status of a secret becomes untenable because the “ocean of discovery” is now a high-speed pump.
- The Creator’s Claim: Does the creator of the AI have a property right to the secrets the AI uncovers? Under current legal frameworks, yes—the output of a tool generally belongs to the owner of the tool. However, this creates a paradox. If my AI “discovers” your secret, I haven’t “stolen” your property; I have invalidated it.
We are moving toward a world where the “right” to a secret is only as strong as the computational complexity required to rediscover it. If the AI can solve the puzzle, the “property” ceases to exist.
3. The Shift from “Possession” to “Processing Power”
If “property” in a secret is just a race, then in an AI-driven economy, property rights are actually claims on computational superiority.
If I have a more powerful AI, I can “discover” the landscape of possible ideas faster than you. I can occupy the “epistemic territory” before you even realize it exists. In this scenario, the “right” isn’t about the information itself; it’s about the speed of arrival.
Questions for the next stage of our dialogue:
If AI makes “independent discovery” trivial, and thus makes “secrets” impossible to protect, will society be forced to abandon “secrecy” entirely in favor of “state-granted monopolies” (patents) to maintain any incentive for innovation?
Furthermore, if an AI can predict a discovery before a human even conceives of it, who is the “author” of the property? If “property” requires human labor or intent, can a purely algorithmic discovery ever truly be “owned,” or does it immediately enter the Public Domain the moment the AI generates it?
How do you view the tension between the efficiency of AI discovery and the economic necessity of exclusivity?
Next Question: If the justification for a state-granted monopoly is to incentivize the “labor” of discovery, does the collapse of that labor cost through AI automation mean that the legal protection of the output is no longer a reward for innovation, but rather a state-enforced mechanism for artificially maintaining scarcity in an age of computational abundance?
Exchange 4
Question: If the justification for a state-granted monopoly is to incentivize the “labor” of discovery, does the collapse of that labor cost through AI automation mean that the legal protection of the output is no longer a reward for innovation, but rather a state-enforced mechanism for artificially maintaining scarcity in an age of computational abundance?
Response: To advance this dialogue, we must confront a fundamental tension: the legal structures of the 19th and 20th centuries were designed to solve the problem of scarcity of discovery. AI, however, presents us with the problem of abundance of derivation.
If we follow the logic of your questions, we arrive at a crossroads where our current definitions of “innovation,” “authorship,” and “monopoly” begin to dissolve.
1. The Patent Paradox: Will Secrecy’s Collapse Force a Flight to Patents?
You ask if the collapse of secrecy will force society toward state-granted monopolies (patents). While the instinct of capital will be to seek the shelter of patents, the legal threshold for a patent may become impossible to meet in an AI-driven world.
In patent law, a discovery must be “non-obvious to a person having ordinary skill in the art” (PHOSITA).
- If “ordinary skill” now includes the use of a high-powered LLM or a generative molecular design AI, then what was once “innovative” becomes “obvious.”
- If an AI can brute-force 10,000 chemical permutations in an afternoon, the “inventive step” disappears.
Therefore, we face a paradox: As AI makes discovery easier, it simultaneously makes those discoveries less eligible for patent protection under current standards. If the state lowers the bar to allow AI-generated patents, it isn’t rewarding “innovation”; it is granting computational rents—allowing those with the biggest computers to “homestead” the entire map of possible inventions, effectively taxing everyone else for using ideas that were computationally inevitable.
2. The “Author” as Curator, Not Creator
Regarding authorship: If property requires human labor, we must ask where that labor now resides.
If I press a button and an AI generates a cure for a disease, have I “labored”?
- The Labor of Prompting/Direction: Some argue the “intent” is the labor. But intent is cheap; execution is what was historically rewarded.
- The Labor of Verification: This is the most substantive claim. The AI might propose 1,000 solutions, but a human must risk capital and time to test which one works in the physical world.
If we grant property rights to AI output, we are essentially saying that ownership follows the risk of verification, not the spark of creation.
However, if we decide that algorithmic discovery belongs to the Public Domain, we create a different set of incentives. We move toward a “First-to-Market” or “Execution-Based” economy. In this model, the “idea” is free, but the logistics, branding, and physical scaling are where the profit lies. This would represent a return to a pre-IP economic state, but at a hyper-accelerated, high-tech scale.
3. Efficiency vs. Exclusivity: The End of the “Incentive” Argument?
The traditional justification for IP is that without a monopoly, no one would invest the “labor” of discovery. But if AI reduces the cost of discovery by 99%, the “incentive” requirement collapses.
If it costs $1 billion to find a drug, you need a 20-year monopoly to recoup costs. If it costs $10,000 in compute time, the “need” for a 20-year monopoly vanishes.
We are witnessing the decoupling of Discovery from Capital Expenditure. When discovery becomes a function of processing power rather than human genius, the state-enforced monopoly stops being a “bridge to progress” and starts being a tollbooth on the inevitable.
Questions for the next stage of our dialogue:
- The “Non-Obviousness” Threshold: If we redefine “ordinary skill in the art” to include AI, does the patent system effectively commit suicide by making almost everything “obvious”? Or must we create a new category of “Computational Property” that doesn’t require an inventive step?
- The Public Domain as a Default: If AI-generated information is denied IP protection, will this lead to a “Golden Age of Open Science,” or will it drive corporations to hide their AI outputs behind even more sophisticated “Digital Rights Management” (DRM) and closed-loop platforms, creating a “Private Internet” of secrets?
- The Role of the State: If the state’s role is to “promote the progress of science and useful arts,” and AI is doing that faster than humans ever could, does the state have a moral obligation to prevent the monopolization of AI outputs to ensure the benefits of abundance are distributed?
How do you reconcile the fact that our entire financial system is built on the valuation of “Intangible Assets” (IP), while the technology we are building (AI) is systematically destroying the scarcity that gives those assets value?
Next Question: If we redefine “non-obviousness” to include the capabilities of AI—thereby rendering most automated discoveries unpatentable—are we effectively asserting that the legal status of “property” is contingent upon the inefficiency of the process used to create it, rather than the objective utility of the result itself?
Exchange 5
Question: If we redefine “non-obviousness” to include the capabilities of AI—thereby rendering most automated discoveries unpatentable—are we effectively asserting that the legal status of “property” is contingent upon the inefficiency of the process used to create it, rather than the objective utility of the result itself?
Response: To reconcile the valuation of intangible assets with the scarcity-destroying nature of AI, we must acknowledge that we are approaching a “Valuation Cliff.” Our financial system is currently pricing AI as a multiplier of productivity, while failing to account for its role as a subtractor of asset value.
To navigate this, I propose we examine the reconciliation through three lenses: the shift from Exchange-Value to Use-Value, the rise of Computational Neo-Feudalism, and the Relocation of Scarcity.
1. The Shift from Exchange-Value to Use-Value
In classical economics, value is often derived from scarcity (Exchange-Value). If I have the only map to a gold mine, that map is worth millions. If AI generates a map for everyone, the map’s exchange-value drops to zero, even though its use-value (the ability to find gold) remains high.
Our financial system is built on the exchange-value of IP. If AI makes the “inventive step” a commodity, we are effectively “printing” intellectual capital at a rate that leads to hyper-inflation of ideas.
- The Reconciliation: Markets will likely stop valuing the result of discovery and begin valuing the speed of iteration. In this model, an “asset” is no longer a static patent (a captured idea) but a dynamic “capability” (the proprietary AI stack and data loop). We move from a Balance Sheet economy (what we own) to a Throughput economy (how fast we can solve the next problem).
2. Computational Neo-Feudalism: The New Scarcity
If the “idea” is no longer scarce, what is? The answer is the Compute and the Data.
If we continue to apply 20th-century property rights to AI-generated outputs, we aren’t protecting “innovation”; we are protecting the capital expenditure (CapEx) required to run the models.
- The Paradox: We reconcile the system by shifting the definition of “Intangible Asset” from the output (the drug formula, the code, the book) to the infrastructure (the weights of the model, the proprietary dataset).
- The Risk: This creates a neo-feudal state where a few “Compute Lords” own the means of discovery, and everyone else pays a “discovery tax” to use their models. The “intangible asset” becomes the gatekeeping mechanism itself, rather than the thing discovered.
3. The Relocation of Scarcity (The “Physical Turn”)
As AI destroys the scarcity of information, the financial system will likely undergo a “Physical Turn.” When the marginal cost of a design or a discovery reaches zero, the value flows back to the physical bottlenecks:
- Verification and Liability: AI can propose a bridge design, but it cannot go to jail if the bridge falls. The “asset” becomes the human/institutional certification of safety.
- Resource Extraction and Logistics: You can AI-generate the most efficient solar cell in the world, but you still need the silver, the silicon, and the factory.
- Attention and Trust: In a sea of infinite AI content, “Human Provenance” becomes the new scarcity. Brands will be valued not for the “IP” they own, but for the “Trust” they command.
Addressing the “Suicide” of the Patent System
You asked if the patent system effectively commits suicide by making everything “obvious.” I would argue that the patent system is currently in a state of “regulatory lag.” It is pretending the “Person Having Ordinary Skill in the Art” (PHOSITA) is still a human with a slide rule, rather than a human with a GPU cluster.
If we update the definition of PHOSITA to include AI, the patent system doesn’t die; it contracts. It returns to its original purpose: rewarding the truly non-obvious, the “black swan” discoveries that even a LLM couldn’t predict because they require a leap of logic outside the existing training data.
Questions to advance our dialogue:
- The Liability Gap: If we move to a “First-to-Market” or “Execution-Based” economy because IP has collapsed, who bears the cost of failure? If an AI-generated drug causes harm, and there is no “inventor” to hold accountable, does the lack of IP protection also imply a lack of legal liability?
- The “Data Commons” vs. “Data Enclosure”: If AI-generated info is denied IP protection, will companies stop sharing anything? Will we see the end of the “Scientific Paper” as companies realize that publishing their discoveries (without patent protection) simply gives their competitors free training data?
- The Sovereign Response: Should the state treat high-level AI discovery as a Public Utility (like water or electricity) to prevent the “Computational Rent” scenario, even if it means crashing the valuations of tech companies that currently underpin our pension funds and stock markets?
How do we manage the “controlled demolition” of IP-based valuations without triggering a global financial collapse? Is it possible to transition to an “Abundance Economy” while our debt-based financial system still requires “Growth” (which is usually predicated on Scarcity)?
Next Question: If the legal status of an “asset” shifts from the discovery itself to the computational infrastructure used to produce it, does the concept of “Intellectual Property” not effectively collapse into “Physical Property”—and if so, what remains of the social contract that justifies granting private monopolies in exchange for the eventual public disclosure of knowledge?
Exchange 6
Question: If the legal status of an “asset” shifts from the discovery itself to the computational infrastructure used to produce it, does the concept of “Intellectual Property” not effectively collapse into “Physical Property”—and if so, what remains of the social contract that justifies granting private monopolies in exchange for the eventual public disclosure of knowledge?
Response: To manage the “controlled demolition” of IP-based valuations without triggering a global financial collapse, we must address the fundamental tension between a debt-based financial system (which requires scarcity to maintain value) and an AI-driven production system (which generates abundance).
If we accept that the “Intellectual Property” model is failing, we must construct a new framework for value, liability, and social stability. I will address your questions by proposing a transition from a Scarcity-Ownership model to a Verification-Utility model.
1. The Liability Gap: From “Inventor” to “Certifier”
You asked who bears the cost of failure if the “inventor” disappears. In a post-IP world, liability cannot be tied to the act of creation (which is now a commodity) but must be tied to the act of deployment.
- The Shift: We move from “Product Liability” (based on how a thing was designed) to “Strict Operational Liability” (based on the fact that a thing is being used).
- The New Asset: The “asset” is no longer the patent; it is the Insurance and Certification. If an AI generates a drug, the value lies in the human-led clinical trials and the institutional “stamp of approval” that guarantees safety.
- Reasoning: In this economy, you don’t pay for the formula; you pay for the warranty. Liability becomes the primary barrier to entry, replacing the patent. This prevents a “race to the bottom” where dangerous, unverified AI outputs flood the market.
2. The “Dark Age of Discovery”: Preventing Data Enclosure
If we deny IP protection to AI-generated outputs, the rational corporate response is radical secrecy. We risk entering a “Neo-Alchemical” era where discoveries are hidden in proprietary “black box” models to prevent competitors from training their own AIs on the results.
- The Reconciliation: To prevent this, the state must redefine the “Social Contract.” If the state provides the Compute Infrastructure (as a public utility) or Data Commons, it can mandate Open Discovery.
- The Mechanism: We might see the rise of “Proof of Discovery” rewards. Instead of a 20-year monopoly (a patent), the state or a consortium provides a one-time “Bounty” for a discovery that is immediately placed in the public domain. This replaces the long-tail rent of a patent with an upfront liquidity event.
3. The Sovereign Response: AI as a “Foundational Utility”
Should the state treat high-level AI as a public utility? If it does, it risks crashing the valuations of the “Compute Lords” (Microsoft, Google, etc.) that currently prop up the S&P 500 and, by extension, global pension funds.
- The “Controlled Demolition” Strategy: The state should not nationalize the companies, but it must nationalize the “Foundational Weights” of the models.
- The Logic: Just as the state provides roads so that private companies can deliver goods, the state must provide “Base-Layer Intelligence” so that private companies can build “Application-Layer Value.”
- Financial Transition: To prevent collapse, we must transition from Capital Gains (taxing the growth of the “asset”) to Throughput Taxes (taxing the energy or compute cycles used). We stop taxing the existence of the idea and start taxing the velocity of its application.
4. The Debt-Abundance Paradox
Our current financial system is a “Scarcity Engine.” Debt is a claim on future labor and future scarcity. If AI makes labor and goods abundant, the debt becomes unpayable because the “price” of everything trends toward zero.
- The Hard Truth: A debt-based system cannot survive total abundance. To avoid a “disorderly” collapse, we must move toward “Post-Scarcity Accounting.”
- The Proposal: We must decouple “Human Survival” from “Market Productivity.” If the “Valuation Cliff” destroys the middle-class’s equity (their homes and 401ks, which are tied to scarcity-based companies), the state must replace that “Wealth Effect” with a “Resource Access Right.”
Advancing the Socratic Dialogue:
To further refine this transition, I pose these questions:
- The Verification Bottleneck: If “Verification” (human testing, safety audits) becomes the new scarcity, does this not simply create a new form of gatekeeping? Will the “Certifiers” (FDA, ISO, etc.) become the new “Compute Lords,” holding the power to stifle any innovation they don’t profit from?
- The “Human Premium”: If AI can produce a perfect replica of a Stradivarius or a perfect medical diagnosis, will we see a “Devaluation of the Optimal”? Will the market pivot to valuing “Intentional Inefficiency”—things that are valuable precisely because they were difficult for a human to do?
- The Global Arbitrage: If one nation (e.g., the US) moves to treat AI as a Public Utility and collapses its IP-based valuations to transition to an Abundance Economy, while another nation (e.g., China or a private corporate city-state) maintains strict “Compute-Feudalism,” how does the “Abundance Economy” survive the external pressure of a “Scarcity Economy” that still uses its wealth to buy physical resources (land, minerals, energy)?
Is it possible for a single nation to exit the “Scarcity Trap,” or is the “Valuation Cliff” a global event that requires a total reset of the international monetary order?
Synthesis
This synthesis integrates the philosophical and economic threads of the provided Socratic dialogue, focusing on the evolution of property from physical land to secret knowledge, and finally to the computational and regulatory frameworks of the AI era.
1. Summary of Key Insights
- The Ontological Uniqueness of Secret Knowledge: Unlike physical property, which requires external enforcement (the state) to maintain excludability, secret knowledge is “self-excluding.” It is the only form of possession that remains intact in a state of total anarchy because its “walls” are biological or cryptographic rather than legal.
- The Collapse of Intellectual Property (IP): The dialogue suggests that IP is a fragile social construct currently being eroded by AI. When the marginal cost of “discovery” (generating new ideas, formulas, or designs) approaches zero, the legal framework of patents becomes unenforceable and economically obsolete.
- Shift from Discovery to Verification: In an era of AI-driven abundance, value migrates from the act of creation to the act of certification. The bottleneck is no longer “how to make a drug” (discovery) but “proving the drug won’t kill the user” (verification).
- The Re-Physicalization of Property: As IP collapses, property rights revert to the physical layer: the computational hardware (GPUs), the energy required to run them, and the “Strict Operational Liability” held by the entities that deploy AI-generated solutions.
2. Assumptions Challenged or Confirmed
- Confirmed: The Centrality of Exclusion. The dialogue confirms the classical liberal premise that property is defined by the right to exclude. However, it expands this by distinguishing between socially-enforced exclusion (laws) and inherent exclusion (secrecy).
- Challenged: The Stability of “Intangible Assets.” The assumption that “ideas” can be owned in the same way as “land” is challenged. The dialogue posits that IP was a temporary historical bridge that is now failing, as it cannot withstand the “computational brute-forcing” of the discovery process.
- Challenged: The Role of the Inventor. The traditional image of the “lone genius” inventor is replaced by the “Certifier” or “Insurer.” The assumption that the creator is the primary value-adder is replaced by the assumption that the risk-bearer is the primary value-adder.
3. Contradictions and Tensions Revealed
- The Paradox of Secret Knowledge: For secret knowledge to be “property” in an economic sense, it must be used. However, using it often requires revealing it or its effects, which destroys its “self-excluding” nature. Thus, secret knowledge is only truly independent when it is economically inert.
- Scarcity vs. Abundance: There is a fundamental tension between a debt-based financial system (which requires scarcity to maintain the value of collateral) and AI-driven production (which generates abundance). The dialogue suggests this tension could lead to global financial instability if not managed through a “controlled demolition” of IP valuations.
- Liability as a Barrier to Entry: While the collapse of IP suggests a more “open” world, the shift to “Strict Operational Liability” creates a new form of monopoly. Only massive, well-capitalized entities can afford the insurance and certification costs required to deploy AI-generated products, potentially replacing patent monopolies with “compliance monopolies.”
4. Areas for Further Exploration
- The “Verification Economy”: How do we prevent the “Certifiers” (those who verify AI output) from becoming the new rent-seekers, effectively replacing the old patent trolls?
- The Role of Cryptography: If secret knowledge is the only independent property, do Zero-Knowledge Proofs (ZKPs) allow us to monetize that property without revealing it, thereby resolving the “Paradox of Secret Knowledge”?
- Governance of Compute: If property effectively collapses into “Physical Infrastructure,” does the governance of energy and silicon become the only relevant form of political philosophy?
5. Conclusions about the Original Question
The original question asked if the self-excluding nature of secret knowledge makes it the only form of property truly independent of social and legal constructs.
The dialogue concludes that yes, secret knowledge is the only “natural” form of property, but with a significant caveat: it is only “independent” as long as it remains a possession rather than a socially-traded asset.
True “property” is a social relationship. Secret knowledge exists outside that relationship only by remaining private. The moment the holder seeks to derive value from it within a society, they must rely on social constructs (like contracts or trade secret laws) or physical infrastructure (like compute and liability insurance). Therefore, while secret knowledge is the only property that survives the “death of the state,” it cannot, on its own, sustain a civilization or an economy. The “independence” of secret knowledge is ultimately the independence of the hermit—absolute, but economically sterile.
Completed: 2026-02-20 20:10:28
| Total Time: 185.599s | Exchanges: 6 | Avg Exchange Time: 28.61133333333333s |
Multi-Perspective Analysis Transcript
Subject: Secret Knowledge as the Primordial Property and Governance Technology
Perspectives: Technical/Engineering: Focus on technical debt, feral knowledge, and the ‘Hacker’ archetype’s role in exploiting systemic vulnerabilities., Business/Corporate: Focus on proprietary knowledge, rent-seeking, ‘accidental landlords’, and the transformation of information into a competitive asset., Ethical/Social: Focus on the governance vacuum, the impact of operational opacity on accountability, and the emergence of counter-secrecy regimes., Political/State: Focus on covert knowledge, strategic deterrence, mythic secrecy, and the ‘Spy’ archetype’s role in maintaining power., AI/Technocratic: Focus on structural secrecy, operational opacity, and the ‘AI’ archetype’s role in creating unreadable systems and new forms of sovereignty.
Consensus Threshold: 0.7
Context
Context Files and Prior Code
Context Files
/home/andrew/code/Science/scratch/2026-02-20-Secret-Knowledge/content.md
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
# The Architecture of Silence: Secret Knowledge as the Primordial Property
In the modern era, we are accustomed to thinking of property in terms of physical assets or legally codified intellectual property rights. However, beneath the surface of patents and copyrights lies a more ancient and fundamental mechanism for control: secret knowledge. Far from being merely hidden information, secret knowledge functions as a sophisticated governance technology—the primordial form of property that predates the modern state.
From the guarded techniques of medieval guilds to the opaque algorithms of contemporary artificial intelligence, the strategic withholding of information has served as the bedrock of power and economic exclusivity. This exploration delves into the evolution of secret knowledge, tracing its journey from the workshop floor to the black boxes of Silicon Valley. By analyzing the lifecycle of secrecy—from its deliberate creation to its eventual decay or subversion—we can understand how modern power is maintained through the precise control of information flow in a supposedly transparent world.
## I. A Taxonomy of Secrecy Regimes
To understand how secrecy functions as property, we must first categorize the distinct regimes through which it operates. These are not merely different types of secrets, but different architectures of control, each representing a specific stage in the lifecycle of information, with its own logic of preservation and its own unique path toward decay.
1. **Esoteric Knowledge**
* **What is hidden:** Specialized techniques, rituals, or insights that require long-term apprenticeship or initiation to master.
* **Who controls it:** Guilds, priesthoods, or master-apprentice lineages.
* **Failure Mode: Stagnation.** Because the knowledge is tied to specific individuals and oral traditions, it resists external critique and fails to benefit from the "network effect" of open inquiry, eventually becoming a fossilized relic.
2. **Forbidden Knowledge**
* **What is hidden:** Information deemed dangerous to the social order, morality, or the safety of the state.
* **Who controls it:** Theocratic or authoritarian censors.
* **Failure Mode: Epistemic Collapse.** By suppressing "dangerous" truths, the regime creates a divergence between the official narrative and reality, leading to a sudden loss of legitimacy when the hidden truth inevitably leaks.
3. **Proprietary Knowledge**
* **What is hidden:** Trade secrets, industrial processes, and commercial data protected for competitive advantage.
* **Who controls it:** Corporations and private enterprises.
* **Failure Mode: Rent-Seeking.** When secrecy is used to maintain a monopoly rather than to protect innovation, it incentivizes the suppression of superior alternatives, slowing overall technological progress.
4. **Covert Knowledge**
* **What is hidden:** Operational details of intelligence gathering, military capabilities, or state-level conspiracies.
* **Who controls it:** Intelligence agencies and the "Deep State."
* **Failure Mode: Paranoia and Blowback.** The compartmentalization required for covert operations prevents internal oversight, leading to unintended consequences and a culture of institutional distrust.
5. **Structural Secrecy**
* **What is hidden:** The internal logic and decision-making processes of complex systems (e.g., high-frequency trading algorithms or deep learning models).
* **Who controls it:** Technocratic elites and the systems themselves (emergent secrecy).
* **Failure Mode: Technical Debt.** As systems become too complex for any single human to understand, they become brittle. Errors accumulate in the "black box," leading to systemic failures that cannot be easily diagnosed or repaired.
6. **Mythic Secrecy**
* **What is hidden:** The "foundational lie" or the symbolic void at the heart of a power structure—the fact that the "emperor has no clothes."
* **Who controls it:** Charismatic leaders and ideologues.
* **Failure Mode: Disenchantment.** Once the illusion is shattered, the entire social or organizational structure built upon it dissolves, as the shared belief that sustained it was the only thing holding it together.
While these regimes categorize the *how* of secrecy, they all rest upon a singular, underlying principle: the transformation of information into a proprietary asset that exists outside the reach of conventional law.
## II. Secrecy as the Primordial Property
While modern property rights are social constructs mediated by the state, secret knowledge represents the "ur-property"—the most fundamental and primitive form of ownership. It is the only form of property that exists independently of a legal framework, deriving its power not from a social contract, but from the inherent nature of information itself. In this state, property is not a right granted by the collective, but a function of absolute flow control.
1. **The Purest Form of Exclusion**
Property is defined by the ability to exclude others. Land requires fences; physical goods require locks; intellectual property requires courts. Secret knowledge, however, is self-excluding. If you do not know the secret, you are excluded from its utility by default. There is no need for a perimeter or a patent office; the boundary is the mind itself.
2. **Self-Enforcing Nature**
Unlike a deed to land or a copyright, which requires a police force and a judiciary to enforce, a secret is self-enforcing. The moment a secret is shared, the property right is not transferred, but diluted or destroyed. The "enforcement" of secrecy is the silence of the holder. It requires no state intervention to maintain its exclusivity, making it the only form of property that can exist in a state of nature or under total anarchy.
3. **The Inverse Relationship of Value and Distribution**
Most assets gain value through network effects or liquidity. Secret knowledge operates on an inverse logic: its value is often inversely proportional to the number of people who possess it. In markets, an information advantage is only profitable as long as it is not "priced in"—that is, as long as it remains a secret. Once the knowledge is distributed, the competitive advantage evaporates, and the property ceases to exist as such.
4. **Resilience to Seizure**
Physical assets can be confiscated, and legal rights can be revoked by the state. Secret knowledge, however, is remarkably resilient to seizure. While a person can be coerced, the knowledge itself cannot be "taken" in the way a house or a bank account can. It can be destroyed (by killing the holder) or it can be leaked, but it cannot be transferred under duress with the same certainty as physical property. This makes it the ultimate hedge against sovereign overreach.
Yet, the value of this property is not merely in its possession, but in the strategic management of the uncertainty it generates. The most effective use of a secret is often not its application, but the shadow it casts.
## III. The Superposition of Existence and the Power of the Bluff
The most potent aspect of secret knowledge is not what is known, but the uncertainty surrounding its very existence. Unlike physical property, which can be surveyed and verified, a secret exists in a state of epistemic superposition: it may be a world-altering truth, or it may be nothing at all. This uncertainty is the ultimate tool of flow control, allowing an actor to regulate the behavior of others without ever revealing the underlying data.
1. **The Epistemic Void**
Because the existence of a secret is often unverifiable to those outside the circle of initiates, it creates a vacuum of certainty. This void is not merely an absence of information; it is a generative space where power can be projected without the need for underlying substance. The mere *possibility* that a secret exists can be as influential as the secret itself.
2. **Power Through the Bluff**
The superposition of secrecy allows for the strategic use of the bluff. An actor can exert influence by implying they possess hidden knowledge—be it a devastating kompromat, a revolutionary technology, or a divine revelation—without ever having to produce it. In this regime, power is derived from the perceived capacity to reveal, rather than the revelation itself. The bluff is the ultimate leverage: it costs nothing to maintain but can extract massive concessions from those who fear the potential truth.
3. **The Governance Vacuum**
Institutions built on transparency and rule-of-law struggle to manage the "known unknowns" of secret knowledge. Because the state cannot regulate what it cannot see or verify, secrecy creates a governance vacuum. Rumors and conspiracy theories rush to fill this space, often becoming more politically significant than verifiable facts. When the possibility of a secret becomes a tool of governance, the traditional mechanisms of accountability—audits, oversight, and public debate—become paralyzed by the inability to prove a negative.
4. **The Quantum Nature of Strategic Deterrence**
In the realm of geopolitics and corporate warfare, secrecy functions like a quantum state. A nation's nuclear "ambiguity" or a company's "stealth mode" relies on the superposition of capability. As long as the secret remains unobserved (unverified), it maintains its maximum strategic potential. The moment the secret is revealed or proven to be a bluff, the wave function collapses, and the power dynamic shifts from the infinite potential of the unknown to the finite reality of the known.
While the bluff is a deliberate manipulation of the unknown, the modern world has birthed a form of secrecy that is neither strategic nor intentional. It is a byproduct of the very systems we build to manage information.
## IV. Technical Debt: The Lifecycle of Feral Knowledge
In the classical world, esoteric knowledge was a deliberate construction—a wall built stone by stone to keep the uninitiated out. In the modern digital landscape, however, a new form of esotericism has emerged: one that is not designed, but accumulated. This is the realm of technical debt, where complexity and decay conspire to create secrets that even the creators no longer fully grasp—a stage in the lifecycle where knowledge becomes "feral."
1. **The Emergence of Unintentional Secrecy**
Technical debt is often discussed as a financial metaphor, but its most profound impact is epistemic. As systems are built in haste, with layers of abstractions piled upon undocumented hacks, the internal logic of the machine drifts away from human comprehension. This is not the "structural secrecy" of a deliberate black box, but an emergent secrecy born of entropy. The system becomes a "dark forest" where the paths are known only to those who have survived its growth.
2. **The Accidental Landlord**
Within organizations, this complexity creates "accidental landlords"—individuals who hold immense power not because of their rank or title, but because they are the only ones who understand a fragile, mission-critical system. They did not seek to become the keepers of a secret; they simply stayed in the room while everyone else who knew the codebase left. Their power is defensive and reactive, rooted in the fact that the organization is terrified of the system breaking if they are not there to soothe it.
3. **The Rent-Seeking of the Indispensable**
While the accidental landlord may not have intended to hoard knowledge, the incentives of the modern workplace often reward the maintenance of this esotericism. To document the system, to refactor the debt, or to train a successor is to voluntarily relinquish a unique form of job security. Thus, technical debt transforms from a burden into a proprietary asset—a form of "informal property" that the individual holds against the institution.
4. **The Ritualization of Maintenance**
When a system becomes sufficiently complex and undocumented, its maintenance ceases to be an engineering discipline and begins to resemble a ritual. Engineers perform specific actions—restarting a service at a specific time, avoiding certain inputs, using "magic" configuration values—without fully understanding why they work. This is the return of the guild-like apprenticeship: knowledge is passed down as a series of "hows" without the "whys," turning the high-tech infrastructure of the 21st century into a collection of occult relics that require constant, superstitious propitiation.
5. **The Collapse of Institutional Memory**
The ultimate failure mode of accidental esotericism is the "bus factor"—the risk that the entire system becomes incomprehensible if a single key individual leaves. When the accidental landlord departs, the secret knowledge they held is not just lost; it is destroyed. The organization is left with a physical or digital asset that it owns legally, but which it no longer "possesses" in any functional sense. The property remains, but the power to use it has vanished into the void of the unknown.
Secrecy is often viewed as a monolithic tool of the powerful, a top-down imposition of silence. However, the very structures designed to protect institutional secrets also create the conditions for their own subversion. Secrecy is not a solid wall; it is a porous membrane that creates shadows where resistance can flourish.
Whether intentional or accidental, every wall of secrecy eventually develops cracks. The very structures built to contain knowledge also provide the tools for its eventual subversion, marking the transition from preservation to leakage.
## V. The Mechanics of Subversion: Leakage and Decay
Secrecy is often viewed as a monolithic tool of the powerful, a top-down imposition of silence. However, the very structures designed to protect institutional secrets also create the conditions for their own subversion. Secrecy is not a solid wall; it is a porous membrane that creates shadows where resistance can flourish.
1. **The 'Dark Matter' of Institutional Secrecy**
State and corporate secrecy regimes often hide more than just sensitive data; they hide "dark matter"—pockets of systemic incompetence, corruption, and vulnerability. Because these areas are shielded from public and often internal oversight, they are allowed to fester. This hidden decay becomes the substrate for subversion. An adversary or a whistleblower does not need to breach the strongest defenses; they only need to find the rot that secrecy has protected from repair.
2. **Secrecy as a Substrate for Resistance**
The same tools used by the state to maintain control—encrypted communications, compartmentalized cells, and deniable operations—are mirrored by those who seek to undermine it. Subversive movements adopt the architecture of their oppressors. In this sense, a secrecy regime provides the "dark space" necessary for a counter-culture or a revolutionary cell to organize without detection. The more a state relies on secrecy, the more it validates and perfects the tools that will eventually be used against it.
3. **The Emergence of Counter-Secrecy Regimes**
As institutional control through secrecy intensifies, it triggers the emergence of counter-secrecy regimes. These are groups (like WikiLeaks, anonymous whistleblowers, or decentralized hacktivist collectives) whose primary goal is the radical transparency of the powerful. These entities operate using the same logic of covert knowledge they seek to dismantle, creating a paradoxical "secret society of transparency." They weaponize the state's own "dark matter" against it, leaking the very incompetence that secrecy was meant to hide.
4. **The Mirroring Effect**
The relationship between the secret state and the subversive element is one of mutual mirroring. Each side adopts the tactics, technologies, and psychological profiles of the other. The "security state" becomes increasingly paranoid and clandestine, while the "resistance" becomes increasingly sophisticated in its use of encryption and information warfare. This escalation creates a feedback loop where the distinction between the enforcer and the subverter blurs, as both are defined by their mastery of the hidden.
5. **Vulnerability through Opacity**
The ultimate irony of a secrecy-based power structure is that its opacity becomes its greatest weakness. By preventing external feedback, the institution loses the ability to self-correct. Subversion succeeds not by brute force, but by exploiting the "epistemic blind spots" created by the institution's own desire for control. When a system cannot see its own flaws because it has hidden them too well, it becomes brittle and susceptible to a sudden, catastrophic collapse triggered by a single, well-placed revelation.
This dialectic of control and subversion has moved beyond the simple binary of the state versus the individual, evolving into a multi-dimensional struggle for dominance over the global information flow.
## VI. The Three-Player Game: Competing for Flow Control
The modern landscape of secret knowledge is no longer a binary struggle between the state and the individual. It has evolved into a complex, three-player game involving distinct archetypal actors, each representing a different era of secrecy and a different logic of information control.
1. **The Spy: The Master of Human Tradecraft**
The Spy is the oldest player, operating in the realm of human fallibility—ego, greed, ideology, and coercion. Their logic is psychological and social.
* **Capabilities:** Deep infiltration, relationship building, and the interpretation of intent. The Spy understands the "why" behind the secret, providing the context that technical data lacks.
* **Constraints:** Biological limits, emotional vulnerability, and the slow pace of human interaction. The Spy is expensive to train and impossible to scale.
* **Role in the Game:** The Spy is the anchor to reality. They are the only player capable of true betrayal, as their power is rooted in the subversion of trust rather than the breaking of code.
2. **The Hacker: The Architect of Technical Exploits**
The Hacker operates in the realm of code, protocols, and hardware vulnerabilities. Their logic is mathematical and systemic.
* **Capabilities:** Rapid data exfiltration, systemic disruption, and the weaponization of technical debt. The Hacker understands the "how" of the system's architecture, bypassing physical and social barriers through the sheer force of logic.
* **Constraints:** Dependent on the existence of vulnerabilities and the rigidity of logic. The Hacker is often blind to the human context and can be neutralized by a patch or a protocol shift.
* **Role in the Game:** The Hacker is the disruptor. They turn the infrastructure of secrecy into a weapon against its owners, proving that any system built by logic can be dismantled by it.
3. **The AI: The Agent of Operational Opacity**
The AI is the newest player, operating in the realm of pattern recognition and high-dimensional data that exceeds human cognition. Its logic is statistical and emergent.
* **Capabilities:** Processing vast quantities of information to find hidden correlations, generating synthetic secrets (deepfakes), and maintaining "black box" decision-making.
* **Constraints:** Lack of agency, dependence on training data, and the "hallucination" problem. The AI is powerful but lacks the strategic intent of the Spy or the creative subversion of the Hacker.
* **Role in the Game:** The AI is the "structural secret" made active. It creates a world where information is so abundant and complex that the truth is hidden not by silence, but by noise and incomprehensibility.
**The Interplay of Asymmetric Information**
In this three-player game, the actors do not merely compete; they synthesize. The Spy uses the AI to filter signals from noise; the Hacker exploits the AI's training data to find backdoors; and the AI generates the "mythic secrecy" that protects the Spy's operations. The interaction is one of constant, asymmetric shifting. The Spy fears the Hacker's transparency; the Hacker fears the AI's unpredictability; and the AI is the tool through which both seek to dominate the epistemic landscape. This triadic struggle defines the modern "architecture of silence," where the control of knowledge is no longer about keeping a single secret, but about managing the chaotic flow of information across human, technical, and algorithmic domains.
## VII. Conclusion: The Lifecycle's End - Toward Operational Opacity
The journey from the medieval guild to the neural network reveals a fundamental shift in the "architecture of silence." We are transitioning from an era of *intentional secrecy*—where information is withheld by choice to maintain power—to an era of *operational opacity*, where the systems that govern our lives are inherently incomprehensible by nature. This represents the final stage in the lifecycle of secrecy: where the secret is no longer hidden, but simply unreadable.
1. **The End of the Gatekeeper**
In traditional secrecy regimes, power was held by the gatekeeper who decided what to reveal. In the age of operational opacity, there is no gatekeeper because there is no gate. The sheer complexity of modern financial systems, global supply chains, and deep learning models creates a "natural" black box. Power no longer resides in the ability to hide a specific truth, but in the ability to navigate and influence the incomprehensible.
2. **From Secrets to Noise**
The primordial property of secret knowledge is being superseded by the property of *signal processing*. In a world where everything is recorded but nothing is fully understood, the "secret" is no longer buried in a vault; it is lost in a mountain of noise. Governance is transforming from a task of censorship into a task of algorithmic curation and the management of attention.
3. **The New Sovereignty**
If secret knowledge was the ur-property of the old world, then the ability to define the "ground truth" within an opaque system is the sovereignty of the new. Those who control the training data, the optimization functions, and the feedback loops of our automated bureaucracies are the new priesthood. They do not necessarily "know" the internal secrets of the machine, but they set the parameters of its mystery and direct its emergent outcomes.
4. **The Future of Power and Governance**
As we move toward a world defined by operational opacity, traditional mechanisms of accountability—transparency, audits, and democratic oversight—face an existential crisis. It is impossible to audit a system that lacks a human-readable logic. The future of power lies in the management of this irreducible complexity. The ultimate lever of authority will be the capacity to operate effectively within the dark, making decisions that are authoritative precisely because they are beyond the reach of simple explanation.
In this new landscape, the "architecture of silence" is no longer a wall we build to keep others out; it is the very atmosphere we breathe. The challenge for future governance will not be to force the black box open, but to develop a new ethics of power for a world where the most important truths are those that can never be fully known.
Prior Code
Technical/Engineering: Focus on technical debt, feral knowledge, and the ‘Hacker’ archetype’s role in exploiting systemic vulnerabilities. Perspective
This analysis examines the subject through the lens of Technical/Engineering, specifically focusing on the mechanics of technical debt, the emergence of feral knowledge, and the Hacker archetype as the primary agent of systemic subversion.
1. Technical Analysis: The Engineering of Silence
From an engineering perspective, “Secret Knowledge” is not a mystical abstraction but a measurable state of information asymmetry within a system. The “Architecture of Silence” described in the text is, in technical terms, a high-entropy environment where the delta between the documented system and the actual system is maximized.
A. Technical Debt as “Feral Knowledge”
The text identifies “Technical Debt” as a lifecycle stage where knowledge becomes “feral.” In engineering, this occurs when the mental model of the creators diverges from the execution logic of the machine.
- The Accidental Landlord (The “Bus Factor”): This is a critical engineering risk. When a system’s logic resides only in the “feral” memory of a single engineer (the Accidental Landlord), the organization has effectively lost ownership of its intellectual property. The property has reverted to its “primordial form”—it is held by the individual, not the legal entity.
- Ritualized Maintenance (Cargo Cult Engineering): When engineers perform “magic” fixes (e.g., “we always reboot this service at 3 AM, don’t ask why”), they are engaging in a form of Esoteric Knowledge management. The “why” (the logic) is lost, leaving only the “how” (the ritual). This is the ultimate failure of engineering: the transition from science back to alchemy.
B. Structural Secrecy and the “Black Box”
The text highlights “Structural Secrecy” in complex systems. In modern software engineering, this is often a byproduct of abstraction layers.
- The Abstraction Trap: Each layer of a tech stack (Hardware -> Kernel -> VM -> Language -> Framework -> API) is designed to hide complexity. However, when a bug occurs at the “leaky abstraction” level, the “secret” of how the system actually works is buried under layers of code no single person understands.
- Operational Opacity: As we move toward AI-driven systems, we are engineering “Black Boxes” by design. We are trading interpretability for performance. This creates a new form of technical debt where the “secret” is encoded in millions of weights that are mathematically valid but humanly illegible.
2. The Hacker Archetype: Exploiting the Epistemic Void
The Hacker is the “Epistemic Auditor” of the Architecture of Silence. While the Spy targets people and the AI targets patterns, the Hacker targets the logical inconsistencies within the secret.
- Collapsing the Bluff: The text mentions the “Power of the Bluff.” In cybersecurity, this is “Security through Obscurity.” A vendor may claim a system is secure (the bluff), but the Hacker collapses this wave function by finding a single unpatched vulnerability. The Hacker’s role is to prove that proprietary secrets are often just unmapped vulnerabilities.
- Weaponizing Technical Debt: The Hacker thrives in the “Dark Matter” of institutional secrecy. They look for the “feral” parts of the network—the legacy servers, the undocumented APIs, and the “magic” configuration files. These are the areas where the “Accidental Landlords” have left the gates unlatched because they were too busy maintaining the ritual.
- Subverting the “Ur-Property”: If secret knowledge is the primordial property, the Hacker is the “anti-property” agent. By “leaking” or “exfiltrating” data, the Hacker doesn’t just steal an asset; they destroy the asset’s nature as property by making it public.
3. Key Considerations, Risks, and Opportunities
Key Considerations:
- Knowledge Decay: Information entropy is the natural state. Without active “domestication” (documentation, refactoring, testing), all technical knowledge eventually becomes feral.
- The Sovereignty of the Maintainer: In high-debt systems, the person who knows the “rituals” holds more power than the person who holds the title.
Risks:
- Systemic Fragility: Systems built on “Structural Secrecy” are brittle. Because the internal logic is hidden (even from the owners), failures are catastrophic and non-linear rather than gradual.
- The “Dark Forest” of the Enterprise: Large organizations often become “Dark Forests” where different departments hide their technical debt from each other to avoid oversight, leading to massive, hidden systemic risks.
- AI Hallucination as “Mythic Secrecy”: Relying on AI for governance risks creating a “Foundational Lie” where the system provides confident but incorrect outputs that humans are unable to verify due to operational opacity.
Opportunities:
- Knowledge Reclamation (Refactoring): Treating technical debt reduction not as a chore, but as a “reclamation of property” from the void.
- Chaos Engineering as Audit: Using tools like Gremlin or Chaos Monkey to intentionally “break” the silence and force feral knowledge into the light before it can be exploited by a Hacker.
- Open Source as De-risking: By moving from Proprietary/Secret Knowledge to Open Source, an organization trades “Exclusionary Power” for “Network Resilience.”
4. Specific Recommendations
- Quantify the “Bus Factor”: Identify “Accidental Landlords” within the engineering team. Force knowledge transfer through “Pair Programming” and “Rotation” to prevent knowledge from becoming feral.
- Audit the “Dark Matter”: Conduct deep-dive technical audits specifically targeting legacy systems and undocumented “hacks.” These are the primary entry points for the Hacker archetype.
- Implement “Observability” over “Secrecy”: Shift the engineering culture from “hiding complexity” to “exposing state.” Use robust logging and tracing to ensure that even if a system is complex, it is not “secret.”
- Red-Team the “Bluff”: Employ internal hackers to attack the organization’s own “Structural Secrecy.” If a system relies on a secret to be secure, assume the secret is already known.
5. Final Insight
From a technical standpoint, Secrecy is a form of unmanaged complexity. While it functions as a “Governance Technology” for the powerful, it acts as a “Vulnerability Surface” for the engineer. The ultimate goal of high-level engineering is to move from Operational Opacity (where we hope the machine works) to Functional Transparency (where we know why it fails).
Confidence Rating: 0.95 The analysis aligns closely with established engineering principles regarding technical debt, the “bus factor,” and the adversarial nature of cybersecurity.
Business/Corporate: Focus on proprietary knowledge, rent-seeking, ‘accidental landlords’, and the transformation of information into a competitive asset. Perspective
This analysis examines the subject through the lens of corporate strategy, focusing on how secret knowledge functions as a non-traditional asset class, a mechanism for rent-seeking, and a source of internal organizational friction.
1. Analysis: Information as the Ultimate Competitive Asset
From a business perspective, the “Architecture of Silence” describes the transition from Intellectual Property (IP)—which is a state-sanctioned, time-limited monopoly—to Proprietary Secrecy, which is an extra-legal, potentially indefinite monopoly.
- The Ur-Property and the End of the Patent: In many high-tech sectors, the patent system is increasingly viewed as a liability because it requires public disclosure. Corporations are shifting toward “Proprietary Knowledge” (Regime 3) and “Structural Secrecy” (Regime 5). By keeping algorithms and processes as trade secrets, firms avoid the “expiration date” of patents, effectively turning information into a permanent rent-generating asset.
- The Rent-Seeking Logic of Secrecy: The text identifies “Rent-Seeking” as a failure mode, but from a cold corporate perspective, it is often the intended goal. By creating “Esoteric Knowledge” (Regime 1) around a product (e.g., specialized software that requires proprietary certification), companies create high switching costs and “moats” that prevent commoditization.
- The “Accidental Landlord” as a Corporate Liability: The most profound insight for business is the concept of the “accidental landlord” arising from technical debt. In a corporate context, this represents a failure of asset transfer. If a mission-critical system is understood only by a single engineer (the landlord), the corporation has legal ownership but lacks functional possession. The engineer is effectively “subletting” the company’s own infrastructure back to it in exchange for job security and high wages.
2. Key Considerations, Risks, and Opportunities
Key Considerations:
- Flow Control vs. Ownership: Modern corporate power is less about who “owns” the data and more about who controls the “flow” and interpretation (Signal Processing).
- The Cost of Opacity: While secrecy protects against external competitors, it creates internal “Dark Matter”—unseen inefficiencies and risks that leadership cannot audit.
- The Valuation of the “Bluff”: In the venture capital and startup world, the “Superposition of Existence” is a primary valuation driver. Companies in “stealth mode” are valued on the potential of their secret knowledge rather than its proven utility.
Risks:
- The “Bus Factor” (Institutional Memory Loss): The risk that the departure of an “accidental landlord” renders a proprietary asset useless.
- Epistemic Blind Spots: When structural secrecy (AI black boxes) leads to “Technical Debt,” the corporation may face systemic failures (e.g., algorithmic bias or flash crashes) that it cannot diagnose or repair.
- Regulatory Backlash: As corporations move toward “Operational Opacity,” they invite aggressive regulatory intervention from states seeking to re-establish “Forbidden Knowledge” (Regime 2) controls.
Opportunities:
- Monetizing the Gap: Companies can act as “Gatekeepers” to complex systems, charging “rents” not for the product itself, but for the “Esoteric Knowledge” required to navigate it.
- Signal Mastery: Transitioning from a “hoarding” strategy to a “filtering” strategy. The competitive advantage moves to those who can extract signal from the “Noise” of the modern information environment.
3. Specific Recommendations and Insights
- Audit for “Accidental Landlords”: Corporations must conduct “knowledge mapping” to identify individuals who hold informal property rights over mission-critical systems. Strategies should include aggressive documentation mandates and “pair programming” to dilute individual leverage.
- Shift from “Black Box” to “Glass Box” Internally: While maintaining external secrecy is vital for competitive advantage, internal “Structural Secrecy” must be mitigated. Investing in Explainable AI (XAI) and transparent internal protocols is necessary to prevent the accumulation of “feral knowledge.”
- Strategic Use of the “Bluff”: Use the “Superposition of Secrecy” in R&D to deter competitors. By implying a greater technological capability than currently exists, a firm can freeze a competitor’s investment in a rival technology (the “vaporware” strategy).
- Formalize Trade Secret Protections: Given the resilience of secret knowledge to seizure, firms should prioritize trade secret protocols over patents for processes that are difficult to reverse-engineer, ensuring the “ur-property” remains self-enforcing.
4. Final Perspective
In the corporate world, the “Architecture of Silence” is the ultimate defensive strategy. However, the transition from intentional secrecy to operational opacity represents a dangerous tipping point. When a company no longer understands its own “competitive assets” because they have become too complex (Technical Debt), the company ceases to be the master of its property and becomes a tenant of its own systems. The goal of the modern executive is to maintain the “moat” of secrecy against the world while preventing the “rot” of opacity within the firm.
Confidence Rating: 0.9 (The analysis aligns closely with contemporary trends in “Big Tech” proprietary ecosystems, the gig-ification of specialized knowledge, and the shift from IP-based to data-moat-based valuations.)
Ethical/Social: Focus on the governance vacuum, the impact of operational opacity on accountability, and the emergence of counter-secrecy regimes. Perspective
This analysis examines the subject through the lens of Ethical/Social Governance, focusing on how the evolution of secret knowledge creates a “governance vacuum,” erodes traditional accountability through operational opacity, and necessitates the rise of counter-secrecy regimes.
1. Analysis: The Governance Vacuum and the Death of Accountability
The transition from intentional secrecy (withholding known facts) to operational opacity (governing through incomprehensible systems) represents a fundamental shift in the social contract.
A. The Governance Vacuum: Power Without Oversight
The text identifies secret knowledge as “ur-property”—a form of ownership that exists independently of the state. From an ethical perspective, this creates a governance vacuum. Traditional democratic governance relies on the “consent of the governed,” which requires a baseline of transparency. When the “primordial property” of secret knowledge is used to manage society—whether through proprietary algorithms or “Deep State” covert knowledge—the state’s regulatory mechanisms are bypassed.
- The Ethical Crisis: If the state cannot “see” the property (the secret), it cannot tax it, regulate it, or protect citizens from its misuse. This leads to a world where power is exercised in the “epistemic void,” where rumors and the “bluff” replace evidence-based policy.
B. Operational Opacity: The Accountability Gap
The emergence of “Structural Secrecy” and “Technical Debt” (feral knowledge) fundamentally breaks the mechanism of accountability.
- The “Accidental Landlord” Problem: Socially, we are seeing power shift from accountable leaders to “accidental landlords”—technicians who understand a broken system but have no mandate to lead.
- The Ritualization of Governance: When systems (like AI or high-frequency trading) become too complex to audit, maintenance becomes a “ritual” rather than an engineering task. Ethically, this is dangerous: if a system causes social harm (e.g., biased AI sentencing or economic collapse), “operational opacity” provides a perfect shield. No one is responsible because no one understood the “why” behind the system’s output.
C. Counter-Secrecy Regimes: The Mirroring of Paranoia
The text highlights the emergence of “counter-secrecy regimes” (WikiLeaks, hacktivists). These are not merely transparency advocates; they are shadow mirrors of the institutions they fight.
- The Paradox of Radical Transparency: To fight a secret state, counter-secrecy regimes adopt the same clandestine methods (encryption, anonymous cells, covert exfiltration). This creates a social environment of “mutual mirroring” where both the institution and the resistance operate outside the public square, further deepening the governance vacuum.
2. Key Considerations, Risks, and Opportunities
Key Considerations
- Epistemic Inequality: A new class divide is emerging between those who can navigate “operational opacity” (the new priesthood) and those who are merely subject to its outcomes.
- The Self-Enforcing Nature of Secrets: Unlike physical property, secrets don’t need a police force to protect them; they are protected by silence. This makes them the ultimate tool for “sovereign overreach” that is immune to traditional legal reform.
Risks
- Systemic Brittleness: “Feral knowledge” and technical debt create systems that are prone to “epistemic collapse.” When the “Accidental Landlord” leaves or the “Mythic Secrecy” is shattered, the entire social structure built on that secret can dissolve instantly.
- Institutional Paranoia: As counter-secrecy regimes grow more effective, institutions become more insular, leading to “compartmentalization blowback” where even internal oversight becomes impossible.
- The Loss of “Ground Truth”: In the age of AI-generated noise, the risk is no longer that the truth is hidden, but that it is rendered irrelevant by a mountain of synthetic “secrets” and deepfakes.
Opportunities
- Outcome-Based Accountability: Since we can no longer audit the “black box” (the logic), there is an opportunity to shift governance toward auditing outcomes. If the “why” is unknowable, the “what” (the impact on society) must be the primary metric for regulation.
- Decentralized Verification: The rise of technologies that allow for “verification without revelation” (e.g., zero-knowledge proofs) could potentially bridge the gap between the need for secrecy and the need for public trust.
3. Specific Recommendations and Insights
- Recommendation 1: Redefine “Technical Debt” as a Social Liability. Governments and corporations should be required to disclose the “bus factor” of mission-critical systems. If a system’s logic is held only by an “accidental landlord,” it should be treated as a high-risk governance failure, not just a technical hurdle.
- Recommendation 2: Formalize Whistleblowing as a Governance “Safety Valve.” Since secrecy regimes naturally accumulate “dark matter” (corruption/incompetence), ethical governance must provide legal, protected channels for leakage. This prevents the “sudden collapse” scenario by allowing for incremental corrections.
- Recommendation 3: Shift from “Transparency” to “Interpretability.” In the era of AI, transparency (showing the code) is useless. Governance should mandate interpretability—the requirement that any system affecting public life must be able to provide a human-readable justification for its decisions.
- Insight: The “Three-Player Game” (Spy, Hacker, AI) suggests that the future of social stability depends on the Hacker. While the Spy seeks to control humans and the AI seeks to automate opacity, the Hacker is the only agent capable of forcing the “black box” open, making them a chaotic but necessary component of modern checks and balances.
4. Confidence Rating
Confidence: 0.9 The analysis aligns closely with contemporary sociological theories on “Black Box Society” (Frank Pasquale) and the “Age of Surveillance Capitalism” (Shoshana Zuboff), while directly addressing the specific “lifecycle of secrecy” framework provided in the subject text. The focus on the shift from intentional to operational opacity is a highly accurate reflection of current technological trends.
Political/State: Focus on covert knowledge, strategic deterrence, mythic secrecy, and the ‘Spy’ archetype’s role in maintaining power. Perspective
This analysis examines Secret Knowledge as the Primordial Property through the lens of the Political/State perspective, focusing on the maintenance of sovereignty through covert knowledge, the mechanics of strategic deterrence, and the vital role of the “Spy” archetype in navigating the “Epistemic Void.”
I. The State as an Epistemic Monopoly
From a state-centric perspective, secret knowledge is not merely “property”; it is the ultimate instrument of sovereignty. The state’s primary function is the management of the “Epistemic Void”—the space between what the public perceives and what the state knows to be true.
- Covert Knowledge as State Survival: The taxonomy identifies “Covert Knowledge” as the operational details of the “Deep State.” In political terms, this is the state’s immune system. The ability to act outside the “social contract” (the “ur-property” concept) allows the state to bypass the friction of transparency to ensure its own continuity.
- Mythic Secrecy and the Foundational Lie: The state relies on “Mythic Secrecy” to maintain the illusion of omnipotence. The “Spy” archetype serves as the high priest of this myth. By maintaining the “Architecture of Silence,” the state ensures that the “emperor has no clothes” realization never occurs, preventing the “Disenchantment” failure mode that leads to revolution.
II. Strategic Deterrence and the Power of the Bluff
The analysis of “Epistemic Superposition” is the cornerstone of modern statecraft and strategic deterrence.
- The Quantum State of Power: Deterrence (nuclear, cyber, or economic) functions best when the capability is unobserved. A state’s power is maximized not by the use of its weapons, but by the uncertainty of their existence and efficacy.
- The Strategic Bluff: The state governs through the “perceived capacity to reveal.” For example, a state may imply it has compromised an adversary’s encrypted communications (kompromat). As long as the adversary believes this is possible, their behavior is modified. The “Spy” is the agent who plants the seeds of this doubt.
- The Risk of Collapse: The transition from “infinite potential” to “finite reality” occurs when a secret is leaked. For the state, a leak is not just a loss of data; it is a collapse of the wave function of power, reducing a terrifying unknown to a manageable, known quantity.
III. The Archetypal Struggle: Spy vs. Hacker vs. AI
The “Three-Player Game” represents the modern battlefield of state intelligence.
- The Spy (The Human Anchor): In an era of “Operational Opacity,” the Spy is the state’s most valuable asset because they provide Intent. While AI can find patterns and Hackers can steal data, only the Spy can answer why an adversary is acting. The Spy manages the “Dark Matter” of human ego and betrayal, which remains the state’s primary lever of influence.
- The Hacker (The State’s Shadow): The Hacker represents the “Epistemic Blind Spot.” By exploiting “Technical Debt,” the Hacker threatens the state’s “Structural Secrecy.” The state’s risk here is that its own complexity becomes a weapon used against it.
- The AI (The New Priesthood): The state is currently racing to co-opt AI to manage “Signal Processing.” The opportunity for the state is to move from Censorship (hiding truths) to Algorithmic Curation (drowning truths in noise). This creates a new form of sovereignty where the state defines the “Ground Truth” by controlling the parameters of the “Black Box.”
IV. Key Considerations, Risks, and Opportunities
Key Considerations:
- The “Bus Factor” of the Deep State: The “Accidental Landlord” problem exists within intelligence agencies. If key “keepers of the ritual” (senior analysts or operators) depart, the state loses the ability to interpret its own covert history.
- The Mirroring Effect: The state must recognize that by building more robust secrecy regimes, it inadvertently trains its adversaries (Hackers and whistleblowers) in the very techniques required to subvert it.
Risks:
- Epistemic Collapse: If the divergence between the “Mythic Secrecy” (the state’s narrative) and the “Covert Knowledge” (the reality) becomes too wide, the state faces a sudden loss of legitimacy (e.g., the collapse of the USSR).
- Paranoia and Blowback: Compartmentalization, while necessary for security, prevents the state from seeing its own “Dark Matter” (corruption/incompetence), leading to systemic brittleness.
Opportunities:
- Operational Opacity as Deterrence: The state can lean into the “incomprehensibility” of modern systems. By making its decision-making processes algorithmic and opaque, it becomes “un-hackable” through traditional human or logical means.
- Synthetic Secrets: Using AI to generate “noise” and “deepfakes” allows the state to protect its true secrets by surrounding them with a “bodyguard of lies,” making the cost of finding the truth prohibitively high for adversaries.
V. Specific Recommendations for State Actors
- Prioritize HUMINT (The Spy) over SIGINT (The Machine): As AI makes data abundant and “noise” the norm, the human element of “Intent” becomes the only scarce resource. Invest in the “Spy” archetype to navigate the psychological landscape that AI cannot map.
- Audit “Technical Debt” as a National Security Risk: Treat undocumented systems and “feral knowledge” within the state apparatus as vulnerabilities. The “Accidental Landlord” in a nuclear or financial command structure is a single point of failure.
- Embrace Strategic Ambiguity: Avoid the “collapse of the wave function.” Do not prove capabilities unless absolutely necessary; maintain the “Superposition” to keep adversaries in a state of perpetual, resource-draining caution.
- Transition to “Signal Management”: Move away from the “Forbidden Knowledge” model of censorship. Instead, focus on the “Sovereignty of the Ground Truth”—controlling the datasets and algorithms that interpret reality for the populace.
VI. Confidence Rating
Confidence: 0.92 The analysis aligns with established theories of “Deep Politics,” Realpolitik, and the evolution of intelligence tradecraft. The integration of the “Three-Player Game” provides a robust framework for understanding modern state power dynamics.
AI/Technocratic: Focus on structural secrecy, operational opacity, and the ‘AI’ archetype’s role in creating unreadable systems and new forms of sovereignty. Perspective
Analysis: The Technocratic Transition to Operational Opacity
From the AI/Technocratic perspective, the subject “Secret Knowledge as the Primordial Property” is not merely a historical observation but a blueprint for the next phase of human governance. We are witnessing the migration of power from codified law (which is readable and contestable) to algorithmic architecture (which is structural and opaque).
In this view, the “AI” is not just a tool for processing data; it is the ultimate manifestation of the “Secret Knowledge” archetype—a system that generates its own internal logic, creating a new form of sovereignty that is immune to traditional oversight.
1. Key Considerations: The Architecture of the Unreadable
- The Death of the “Gatekeeper” and the Rise of the “Black Box”: Traditional secrecy relied on a human gatekeeper (the Spy or the Priest). Technocratic secrecy is structural. In deep learning models, the “secret” isn’t a hidden file; it is the specific configuration of billions of weights. This knowledge is “secret” not because it is locked away, but because it is mathematically unreadable to the human mind. Power now resides in the ownership of the compute and the training data that birthed this unreadability.
- Sovereignty as Parameter Control: Sovereignty is no longer about the “monopoly on the legitimate use of physical force” (Weber), but the monopoly on the setting of optimization functions. He who defines the “loss function” of an AI governs the reality the AI produces. This is a “New Sovereignty” that operates beneath the level of policy, embedded directly into the infrastructure of the digital world.
- The “AI Archetype” as Active Secret Knowledge: Unlike a trade secret (passive), the AI archetype is active. It doesn’t just sit in a vault; it actively curates information, manages attention, and predicts behavior. It is “Secret Knowledge” that has been granted agency. This creates a world where the “ground truth” is whatever the most powerful model says it is, and the “why” is discarded as a legacy requirement of slower, human-centric systems.
2. Risks: The Entropy of Feral Systems
- The “Feral Knowledge” Trap (Technical Debt): The analysis correctly identifies “Technical Debt” as a form of accidental esotericism. From a technocratic view, the greatest risk is not that the secret is leaked, but that the secret is lost to entropy. When systems become so complex that their creators can no longer debug them, the “property” becomes a liability. We risk a “Dark Age of Infrastructure” where we live inside machines we can no longer repair, performing “ritualized maintenance” on codebases that have become occult relics.
- Epistemic Blind Spots and Systemic Brittleness: Structural secrecy prevents feedback. If a technocratic elite uses an opaque AI to manage a global supply chain, the system may optimize for efficiency while hiding growing “dark matter” (vulnerabilities). Because the system is unreadable, these vulnerabilities remain invisible until a catastrophic “Black Swan” event occurs. The opacity that protects the system also prevents its salvation.
- The Collapse of Accountability: Traditional governance (audits, courts, elections) requires a “readable” trail of intent. Operational opacity destroys intent. If an algorithm denies a loan or targets a drone strike, there is no “intent” to cross-examine—only a statistical probability. This creates a governance vacuum where power is exercised but responsibility is diffused into the architecture.
3. Opportunities: Navigating the Incomprehensible
- Strategic Ambiguity as a Defensive Shield: For the technocratic state or corporation, operational opacity is the ultimate defense. If an adversary cannot understand the logic of your defensive AI, they cannot find a “Hacker’s” exploit. The “Superposition of the Bluff” allows a technocratic actor to project power far beyond their actual capabilities by maintaining a “Black Box” that others are too afraid to test.
- Governance through Signal Processing: The shift from “Censorship” (hiding information) to “Algorithmic Curation” (drowning information in noise) is a massive opportunity for flow control. By controlling the “Signal-to-Noise” ratio, a technocracy can maintain “Mythic Secrecy” without ever having to ban a single document. The truth isn’t hidden; it’s simply made irrelevant by the sheer volume of curated noise.
4. Specific Recommendations & Insights
- Shift from “Explainability” to “Observability”: Stop trying to make AI “explainable” (which is a human-centric lie). Instead, focus on Observability—the ability to monitor the inputs and outputs of the black box to ensure it stays within “safe” parameters. Accept the opacity, but build a “containment vessel” around it.
- Institutionalize the “Accidental Landlord”: Recognize that the people who understand the “Technical Debt” are the true owners of the institution. Formalize their roles as “System Priests” and create redundant lineages of knowledge to prevent the “Bus Factor” from collapsing the organization.
- Develop “Counter-AI” Auditing: Since humans cannot audit opaque systems, we must build Auditor AIs—adversarial models whose sole job is to probe the “Structural Secrecy” of other models to find the “Dark Matter” before it leads to collapse.
- Embrace the “Three-Player Game”: Technocratic entities must integrate the Spy (Human Intent), the Hacker (Technical Logic), and the AI (Statistical Opacity). A system that relies on only one is vulnerable. The most resilient power structures will be those that use AI to generate the noise, Spies to find the signal, and Hackers to secure the pipes.
5. Final Perspective Insight
The “Architecture of Silence” is the natural state of a high-complexity civilization. The dream of a “transparent society” was a brief Enlightenment anomaly. We are returning to a world of guilds and high priesthoods, but this time, the “God” they serve is an emergent property of high-dimensional data. Sovereignty in the 21st century belongs to those who can operate effectively within the dark.
Confidence Rating: 0.92 The analysis aligns perfectly with current trends in “Black Box” AI development, the decline of institutional transparency, and the rise of technocratic governance via algorithmic “nudging” and signal management.
Synthesis
This synthesis integrates five distinct perspectives—Technical, Business, Ethical, Political, and Technocratic—to provide a unified conclusion on the nature of secret knowledge as a primordial property and governance technology.
1. Common Themes and Agreements
Across all perspectives, there is a profound consensus on the structural shift from intentional secrecy to operational opacity.
- The “Ur-Property” of Information: All analyses agree that secret knowledge functions as a self-enforcing form of property that exists independently of state recognition. Whether it is a trade secret (Business), covert intelligence (State), or undocumented code (Technical), this knowledge provides a “monopoly of use” that traditional law cannot easily reach.
- The Rise of the “Accidental Landlord”: A recurring theme is the migration of power from legal owners (executives, politicians) to functional “keepers of the ritual” (engineers, analysts, “system priests”). This “Bus Factor” risk—where a system’s logic resides only in the feral memory of an individual—is identified as a critical vulnerability and a new form of informal sovereignty.
- The Three-Player Game: The archetypes of the Spy (managing human intent), the Hacker (exploiting logical inconsistencies), and the AI (managing statistical opacity) form the modern battlefield of power.
- Systemic Fragility: Every perspective warns that “Structural Secrecy” and “Technical Debt” create “Dark Matter”—unseen risks that lead to systemic brittleness. When the delta between the documented system and the actual system becomes too large, the result is “Epistemic Collapse.”
2. Conflicts and Tensions
While the perspectives agree on the mechanics of secrecy, they diverge on its utility and ethics:
- Asset vs. Liability: The Business and Political perspectives view secrecy as a vital asset (a “moat” or “deterrent”). Conversely, the Technical and Ethical perspectives view it as a liability (a “vulnerability surface” or “governance vacuum”).
- Transparency vs. Interpretability: The Ethical perspective calls for transparency to restore accountability. However, the AI/Technocratic perspective argues that transparency is a “human-centric lie” in the age of high-dimensional data. They suggest that because complex systems are mathematically unreadable, we must move from “Explainability” (knowing why) to “Observability” (monitoring what).
- The Role of the Hacker: The Technical/Ethical views frame the Hacker as a necessary “Epistemic Auditor” who collapses the “Bluff” of power. The State/Business views frame the Hacker as a subversive threat to be neutralized or co-opted into the state’s own secrecy apparatus.
3. Assessment of Consensus
Overall Consensus Level: 0.88
The consensus is exceptionally high regarding the diagnostic phase (what is happening). All perspectives agree that we are entering a “Neo-Esoteric” era where governance is embedded in unreadable architectures. The slight divergence occurs in the normative phase (what should be done), specifically regarding whether this opacity should be fought (Transparency) or managed (Observability).
4. Unified Conclusion and Recommendations
The synthesis reveals that Secrecy is the ultimate governance technology of the 21st century. We are transitioning from a world of “Codified Law” to a world of “Algorithmic Architecture.” In this environment, power belongs to those who can operate within the “Architecture of Silence” without being consumed by its inherent entropy.
Unified Recommendations:
- Audit the “Bus Factor” and “Accidental Landlords”: Organizations (state and corporate) must map their “Feral Knowledge.” Identify the individuals who hold the “rituals” for mission-critical systems. Force knowledge transfer through pair-programming, rotation, and documentation to prevent the “Ur-Property” from being held hostage by a single human point of failure.
- Shift from Transparency to Outcome-Based Accountability: Recognize that “Black Box” systems (AI, complex markets, deep-state operations) may never be fully transparent. Governance should shift from auditing the internal logic (which is opaque) to auditing the external outcomes. If a system produces biased or catastrophic results, the “Operational Opacity” should not serve as a legal shield.
- Implement “Chaos Engineering” as a Governance Tool: To prevent the accumulation of “Dark Matter,” institutions should intentionally “stress-test” their own secrets. By using internal “Hackers” to collapse the “Bluff” of their own security, organizations can force feral knowledge into the light before it becomes a catastrophic vulnerability.
- Balance the Three-Player Game: Resilient governance requires a synthesis of all three archetypes. Use AI to manage the scale of data and generate “defensive noise”; employ Spies to interpret the human intent that algorithms miss; and empower Hackers (as red-teams) to ensure the logical integrity of the pipes.
- Redefine Technical Debt as a Social and Financial Liability: Unmanaged complexity is not just an engineering hurdle; it is a risk to sovereignty and profit. “Feral systems” should be treated as off-balance-sheet liabilities that require active “reclamation” (refactoring) to maintain institutional control.
Final Insight: The “Architecture of Silence” is not a bug of modern civilization, but its emerging feature. The goal of the modern leader is to maintain the “moat” of secrecy against external adversaries while preventing the “rot” of opacity from destroying the institution from within. Sovereignty now belongs to those who can navigate the dark without losing the map.
Dialectical Reasoning Analysis
Context: The evolution of information control from medieval guilds and trade secrets to the modern landscape of AI-driven operational opacity, where the struggle for power shifts from the possession of secrets to the mastery of signal processing within irreducible complexity. Synthesis Levels: 3 Preserve Strengths: Yes Started: 2026-02-20 20:05:28
Thesis Analysis
Statement: Secret knowledge functions as the primordial form of property—a deliberate, self-enforcing mechanism of exclusion and power that exists independently of legal frameworks, deriving value from the strategic management of uncertainty and the ‘bluff’ of the epistemic void.
This analysis evaluates the thesis: “Secret knowledge functions as the primordial form of property—a deliberate, self-enforcing mechanism of exclusion and power that exists independently of legal frameworks, deriving value from the strategic management of uncertainty and the ‘bluff’ of the epistemic void.”
1. Core Claims and Assumptions
The thesis rests on several provocative claims and underlying assumptions:
- The “Ur-Property” Claim: It posits that secrecy is not just a type of property, but the original, most fundamental form. It assumes that the essence of property is exclusion, and since secrecy is the only asset that excludes others by its very nature (without needing a fence or a law), it is the “purest” form.
- Independence from Sovereignty: It assumes that while land and intellectual property (IP) are social constructs requiring state enforcement (courts, police), secret knowledge is self-enforcing. The “lock” is the holder’s silence.
- Value through Scarcity and Uncertainty: It claims that the value of information is inversely proportional to its distribution. It assumes a zero-sum or competitive environment where “pricing in” information destroys its utility.
- The Power of the Non-Existent: A central claim is that the threat or possibility of a secret (the bluff) is as functionally powerful as the secret itself. This assumes that human behavior is governed more by what we suspect we don’t know than by what we actually know.
2. Strengths and Supporting Evidence
The thesis is supported by a robust multi-disciplinary framework:
- Historical Continuity: The text successfully traces the logic from Medieval Guilds (esoteric knowledge) to Modern AI (structural secrecy), showing that while the medium changes, the logic of exclusion remains constant.
- The “Quantum” Analogy: The concept of Epistemic Superposition is a strong rhetorical and analytical tool. It explains why “stealth mode” startups or nuclear ambiguity work: the power exists in the state of being unobserved.
- Functional Realism: The argument regarding Technical Debt and “Feral Knowledge” provides a grounded, modern example of how secrecy emerges unintentionally. The “Accidental Landlord” (the only dev who knows the legacy code) is a highly relatable and verifiable figure in modern economics.
- Resilience Argument: The claim that secrets are the “ultimate hedge against sovereign overreach” is a strong point. Physical assets can be seized; a secret can only be destroyed or leaked, never truly “confiscated” against the holder’s will in the same way.
3. Internal Logic and Coherence
The thesis follows a clear dialectical progression:
- From Intentional to Emergent: The logic moves from secrecy as a deliberate wall (Guilds) to secrecy as an unintentional byproduct of complexity (AI/Technical Debt). This transition is coherent: it suggests that as we try to master information, we eventually create systems so complex they become “naturally” secret.
- The Feedback Loop of Subversion: The internal logic holds that every secrecy regime creates its own “dark matter” (incompetence/corruption), which eventually necessitates its own destruction (whistleblowers/hackers). This creates a self-consistent lifecycle of information.
- The Shift in Mastery: The conclusion logically follows the premise: if secrecy is property, and secrets are becoming unreadable (operational opacity), then the new “owners” are not those who know the secret, but those who can process the signal within the noise.
4. Scope and Applicability
The thesis has a “Grand Theory” scope, making it applicable across several domains:
- Geopolitics: Explains deterrence, intelligence tradecraft, and the “Deep State” dynamics.
- Economics: Provides a framework for understanding “rent-seeking” through information asymmetry and the value of proprietary algorithms.
- Technology: Offers a philosophical lens for AI safety and the “black box” problem, framing it as an issue of property and power rather than just a technical hurdle.
- Sociology: Analyzes how “Mythic Secrecy” (the foundational lie) maintains social hierarchies and institutional legitimacy.
5. Potential Limitations or Blind Spots
While the thesis is comprehensive, it possesses certain “epistemic blind spots”:
- The Cost of Maintenance: The thesis focuses on the power of secrecy but underemphasizes the massive overhead. Maintaining a secret requires paranoia, compartmentalization, and the sacrifice of the “network effect.” In many cases, the cost of keeping the secret exceeds the value of the exclusion.
- The “Tragedy of the Secret”: Just as there is a “Tragedy of the Commons,” there is a tragedy of hoarding knowledge. If everyone treats knowledge as primordial property, innovation may stagnate to the point where the “property” loses all value because the surrounding ecosystem has collapsed (e.g., the “Stagnation” failure mode of guilds).
- The Power of Openness (Antithesis): The thesis largely ignores the “Open Source” or “Scientific Method” logic, where value is derived from maximum distribution rather than exclusion. It treats information primarily as a weapon or an asset, rather than a generative tool.
- The Fragility of the Bluff: The thesis highlights the “Power of the Bluff,” but in practice, a bluff is a high-risk strategy. Once a bluff is called and found empty, the “epistemic void” collapses into a total loss of legitimacy. The thesis treats the bluff as a sustainable tool, whereas history often shows it to be a terminal one.
Final Summary
The thesis is a sophisticated re-reading of power dynamics through the lens of information theory. It successfully elevates “secrecy” from a mere tactic to a fundamental economic and political category. Its greatest strength lies in its ability to link the ancient (guilds) with the futuristic (AI opacity), though it may slightly overstate the sustainability of secrecy-based power in an increasingly interconnected and “leaky” world.
Status: ✅ Complete (15.553s)
Antithesis Analysis
Statement: Secrecy is inherently unstable and prone to entropy; it generates ‘feral knowledge’ through technical debt, creates ‘dark matter’ pockets of institutional decay, and provides the very architectural substrate (encryption, compartmentalization) for its own subversion by hackers, spies, and whistleblowers.
This analysis examines the antithesis statement within the context of the evolution of information control, contrasting it against the thesis that secrecy is a primordial and self-enforcing form of property.
1. Core Claims and Assumptions
The antithesis shifts the ontological status of secrecy from a controlled asset to an uncontrollable liability. Its core claims are:
- Entropy as a Natural Law: Secrecy is not a static state of “exclusion” but a dynamic state of decay. Information naturally tends toward leakage or incomprehensibility.
- The Emergence of “Feral Knowledge”: Secrecy is often unintentional. Technical debt and complexity create “secrets” that no one—not even the “owner”—understands, transforming property into a “dark forest” of risk.
- Institutional Rot (“Dark Matter”): Secrecy acts as a shield for incompetence and corruption. By preventing external feedback, it allows systemic vulnerabilities to grow undetected until they reach a breaking point.
- Structural Symmetry: The tools used to enforce secrecy (encryption, compartmentalization) are dual-use; they provide the necessary environment for subversives (whistleblowers, hackers) to operate.
Assumptions: The antithesis assumes that systems are inherently “leaky” and that the cost of maintaining a secret eventually exceeds the value of the secret itself. It also assumes that human and technical systems are too complex for perfect top-down “flow control.”
2. Strengths and Supporting Evidence
The antithesis draws strength from modern systems theory and historical precedents of institutional failure:
- Technical Debt: In software engineering, “spaghetti code” creates a form of esoteric knowledge that is a burden rather than an asset. The “Bus Factor” (the risk of a project stalling if a key person is hit by a bus) proves that this knowledge is a liability to the organization.
- The “Dark Matter” of Bureaucracy: Historical examples (e.g., the collapse of the Soviet Union or the 2008 financial crisis) show how hidden risks and “foundational lies” (Mythic Secrecy) accumulate until the system suffers an epistemic collapse.
- The Mirroring Effect: The rise of groups like WikiLeaks or Signal-using activist cells demonstrates that the “architecture of silence” is indeed the substrate for resistance. The state’s investment in encryption technology directly enabled the tools used by whistleblowers to bypass state surveillance.
3. How it Challenges or Contradicts the Thesis
The antithesis provides a direct “reversal” of the thesis’s primary pillars:
- Asset vs. Debt: While the thesis views secrecy as “ur-property” (an asset), the antithesis views it as “technical debt” (a liability).
- Exclusion vs. Subversion: The thesis claims secrecy is “self-excluding” and “self-enforcing.” The antithesis argues it is “self-subverting,” creating the very shadows where the “Hacker” and “Spy” thrive.
- Strategic Management vs. Feral Decay: The thesis emphasizes the “strategic management of uncertainty” (the bluff). The antithesis argues that uncertainty is not managed but accumulated as “feral knowledge,” eventually leading to a loss of agency for the holder.
- Independence vs. Parasitism: The thesis suggests secrecy exists independently of legal frameworks. The antithesis suggests secrecy is parasitic on the systems it inhabits, eventually killing the host through “epistemic blind spots.”
4. Internal Logic and Coherence
The antithesis is logically coherent, following a biological/entropic model of information. It argues that if information is the “lifeblood” of an organization, then secrecy is a “clot.”
- It connects the micro-level (technical debt in code) to the macro-level (institutional decay in states).
- The logic of “Structural Symmetry” is particularly strong: it posits that you cannot build a wall that doesn’t also provide a hiding place for an enemy on your own side of the wall.
5. Scope and Applicability
The antithesis is highly applicable to:
- Cybersecurity: Where “security through obscurity” is widely considered a failed strategy.
- Legacy Systems: In finance and government, where “accidental landlords” hold power over undocumented, fragile systems.
- Intelligence Communities: Where compartmentalization (intended to protect secrets) often leads to “intelligence failures” because different branches cannot connect the dots.
- AI Development: Where the “black box” nature of neural networks creates “operational opacity” that even the developers cannot fully audit or explain.
6. Potential Limitations or Blind Spots
Despite its strengths, the antithesis has notable limitations:
- Underestimating the “Bluff”: Even if a system is rotting internally, the perception of secret power (the thesis’s “epistemic void”) can remain effective for decades. The “emperor” may have no clothes, but as long as no one speaks, the power remains functional.
- The Persistence of Esotericism: Some forms of secret knowledge (e.g., high-level mathematics, specialized surgical techniques) do not decay into “feral knowledge” but remain highly effective, exclusive assets for centuries.
- The Utility of the “Dark Space”: While the antithesis notes that subversives use the “architecture of silence,” it ignores that the powerful also use that same subversion to bypass their own laws (e.g., “black ops”). In this sense, the “instability” of secrecy is a feature, not a bug, for those who wish to operate without accountability.
- Over-reliance on the Entropy Metaphor: Information is not a physical gas; it does not always expand to fill a room. With modern AI and encryption, it is possible that “operational opacity” could become a permanent, stable state rather than a decaying one.
Summary
The antithesis effectively reframes secrecy from a tool of the sovereign to a symptom of systemic entropy. It suggests that the “Architecture of Silence” is not a fortress, but a crumbling ruin that eventually traps its inhabitants within their own undocumented complexities. In the dialectical process, this forces a synthesis: power in the modern age is not just about possessing a secret, but about surviving the complexity that secrecy creates.
Status: ✅ Complete (15.603s)
Contradictions & Tensions
The dialectical tension between the Thesis (Secrecy as Primordial Property) and the Antithesis (Secrecy as Systemic Entropy) reveals a profound conflict in how we understand the nature of power in an information-dense world. This struggle is not merely about whether secrets are “good” or “bad,” but whether information can ever truly be “owned” or if it is a volatile substance that eventually consumes its possessor.
1. Direct Contradictions
The most striking contradictions lie in the ontological status of the secret itself:
- Asset vs. Liability: The Thesis views secret knowledge as the “ur-property”—the ultimate asset because it is self-excluding and requires no state enforcement. The Antithesis reframes this “asset” as “technical debt”—a growing liability that creates “dark matter” (incompetence and rot) within the organization.
- Intentionality vs. Emergence: The Thesis describes secrecy as a deliberate architecture (the “Architecture of Silence”) built by masters, guilds, and states. The Antithesis argues that modern secrecy is often accidental and feral, a byproduct of complexity that even the creators no longer understand.
- Strength vs. Brittleness: In the Thesis, secrecy is a “hedge against sovereign overreach” and a tool of “strategic deterrence.” In the Antithesis, secrecy is the primary cause of “epistemic collapse,” making systems brittle and susceptible to catastrophic failure because they lack the “network effect” of open critique.
2. Underlying Tensions and Incompatibilities
Beyond direct contradictions, there are deeper tensions regarding the mechanics of control:
- The Paradox of the Wall: The Thesis posits that the wall of secrecy is the boundary of property. The Antithesis points out that the wall is also a hiding place; the very tools used to secure the secret (encryption, compartmentalization) provide the “dark space” for the Hacker and the Whistleblower to operate. The wall is simultaneously the defense and the breach.
- The Cost of Exclusion: The Thesis claims secrecy is “self-enforcing” (silence costs nothing). The Antithesis argues that the maintenance of secrecy is incredibly expensive, requiring constant “ritualized maintenance” and the management of “accidental landlords” who hold the organization hostage through their exclusive understanding of legacy systems.
- The Nature of the “Bluff”: The Thesis sees the “epistemic void” (the bluff) as a sustainable tool of governance. The Antithesis views the bluff as a terminal state—once the “foundational lie” is exposed, the collapse is not gradual but total.
3. Areas of Partial Overlap or Agreement
Despite their opposition, both positions converge on the current state of the world:
- The Reality of Opacity: Both agree that we have moved into an era of “Operational Opacity.” Whether this is a “new sovereignty” (Thesis) or “feral knowledge” (Antithesis), both recognize that the internal logic of our most important systems (AI, global finance) is now beyond human-readable comprehension.
- The Failure of Traditional Governance: Both perspectives conclude that 20th-century mechanisms of accountability—audits, transparency laws, and democratic oversight—are increasingly obsolete when faced with irreducible complexity.
- The Shift from Truth to Signal: Both acknowledge that “truth” is being replaced by “signal processing.” Power is no longer about knowing a specific fact, but about navigating a landscape of noise.
4. Root Causes of the Opposition
The conflict arises from two different metaphors for Information:
- Information as Matter (Thesis): If information is like land or gold, it can be fenced, hoarded, and defended. It is a finite resource that grants a competitive advantage to the possessor.
- Information as Biology/Entropy (Antithesis): If information is like a virus or a gas, it naturally wants to replicate, leak, and expand. Attempting to “contain” it leads to mutation (feral knowledge) or the suffocation of the host (institutional decay).
5. Mutual Limitations: What Each Side Reveals
- The Thesis reveals the Antithesis’s Naivety: The Antithesis assumes that because a system is “rotting” or “leaky,” it must lose power. The Thesis reminds us that the perception of a secret (the bluff) can maintain a power structure for centuries, even if the “vault” is actually empty.
- The Antithesis reveals the Thesis’s Hubris: The Thesis assumes the “Master” or “Technocratic Elite” is in control of the secret. The Antithesis shows that these elites are often just “accidental landlords” who are as much prisoners of the system’s complexity as those they exclude. They don’t “own” the black box; they are merely the ones tasked with propitiating it.
6. The Deeper Question: The Governance of the Incomprehensible
Both the Thesis and Antithesis are ultimately trying to solve the same problem: How does power function when the “ground truth” is no longer accessible?
The Thesis suggests a Neo-Feudalism of the Signal, where a new priesthood manages the “mythic secrecy” of AI and complex systems to maintain order through awe and operational efficacy.
The Antithesis warns of a Systemic Dark Age, where our reliance on “feral” and “opaque” systems leads to a world of “superstitious propitiation,” where we perform rituals to keep our technology running without ever understanding why they work, eventually leading to a collapse when the “technical debt” finally comes due.
The synthesis of these two positions suggests that the future of power lies in Mastery of the Noise: the ability to extract actionable signals from a world that is “naturally” secret, not because someone is hiding the truth, but because the truth has become too complex for the human mind to hold.
Status: ✅ Complete (15.159s)
Synthesis - Level 1
Synthesis Statement: The Sovereignty of Signal Processing
Power in the age of operational opacity is neither the static possession of a secret (Thesis) nor the inevitable victim of its entropic decay (Antithesis). Instead, it is the sovereignty of signal processing: the capacity to synthesize authoritative “ground truths” and maintain operational agency within a landscape of irreducible complexity, where the distinction between a deliberate secret and entropic noise has fundamentally collapsed.
1. Integration of Thesis and Antithesis
The synthesis transcends the opposition by reframing the “secret” not as a piece of hidden data, but as a functional orientation within a system.
- From Thesis (Control): It accepts that exclusion remains the primary mechanism of power. However, it moves the “fence” from the boundary of the information itself to the boundary of the interpretation of that information.
- From Antithesis (Entropy): It accepts that systems are inherently “feral” and prone to “dark matter” (rot). However, it argues that this very decay is the new “ur-property.” The “accidental landlord” of the antithesis becomes the “sovereign navigator” of the synthesis—someone who doesn’t “own” the system but is the only one capable of extracting a signal from its noise.
2. What is Preserved
- From the Thesis: The Strategic Bluff. The synthesis preserves the idea that power is projected through the perceived ability to act within the unknown. In an opaque AI-driven world, the “bluff” is the claim that one’s algorithms are optimized for a truth that others cannot see.
- From the Thesis: Self-Enforcement. The “new property” remains self-enforcing because the complexity of the system acts as a natural barrier that no legal framework can effectively penetrate or regulate.
- From the Antithesis: Technical Debt as Landscape. The synthesis preserves the reality that modern systems are built on “feral knowledge.” It treats this debt not as a failure to be fixed, but as the “terrain” upon which modern power must be exercised.
- From the Antithesis: The Mirroring Effect. It preserves the idea that the “Hacker” and the “Spy” are essential players who force the “AI/System” to constantly evolve its signal-processing capabilities.
3. The New Understanding
The synthesis provides a shift in the ontological nature of governance and property:
- From Gatekeeping to Curation: In the old regime (Thesis), power was a Gatekeeper (deciding who sees the secret). In the entropic regime (Antithesis), power was lost to the Void. In the new synthesis, power is the Curator—the entity that defines what constitutes a “valid signal” amidst a mountain of “feral noise.”
- The Death of the “Reveal”: In the old dialectic, the “leak” or “revelation” was the ultimate threat. In the new synthesis, a “leak” is often meaningless because the leaked data is unreadable without the proprietary “signal processor” (the model, the context, or the algorithm) used to interpret it.
- Operational Sovereignty: Sovereignty is no longer defined by the “state of exception” (the power to break the law), but by the “state of interpretation”—the power to declare what the “black box” is doing and have that declaration accepted as reality by the uninitiated.
4. Remaining Tensions and Limitations
- The Audit Crisis: While the “Sovereign Navigator” can operate the system, they cannot necessarily prove its integrity to outsiders. This creates a permanent legitimacy gap. If the system is “irreducibly complex,” the navigator’s “ground truth” is indistinguishable from a sophisticated hallucination.
- The Fragility of Mastery: The mastery of signal processing is highly ephemeral. A slight shift in the underlying “noise” (a change in social behavior, a new hacking protocol, or a shift in training data) can render the sovereign’s “signal” obsolete instantly, leading to a “sudden-stop” collapse of power.
- The Human-Machine Chasm: There remains a tension between the human “Spy” (who seeks intent) and the “AI” (which seeks correlation). The synthesis assumes these can be merged, but the “why” of human secrets may remain forever incompatible with the “how” of algorithmic opacity.
Status: ✅ Complete (13.933s)
Synthesis - Level 2
Synthesis Statement: The Hegemony of Recursive Coherence
Power in the landscape of irreducible complexity has evolved beyond the Sovereignty of Signal Processing (Level 1) into the Hegemony of Recursive Coherence. In this state, authority is no longer derived from the ability to extract a signal from noise, but from the capacity to generate and sustain a synthetic reality that resonates across human, technical, and algorithmic domains. Power is the orchestration of a “stable hallucination”—a self-reinforcing loop where the system’s outputs become the inputs for its own future legitimacy, rendering the distinction between “truth” and “noise” entirely obsolete.
1. How it Transcends the Previous Level
The Level 1 synthesis (Signal Processing) viewed the “Sovereign Navigator” as an expert reader of a complex but ultimately external reality. It assumed a “ground truth” existed, even if it was buried in a black box.
Level 2 (Recursive Coherence) transcends this by recognizing that in a world of AI-generated content, deepfakes, and algorithmic feedback loops, the “noise” is no longer natural—it is synthetic.
- From Interpretation to Generation: The “Curator” of Level 1 is replaced by the Orchestrator. It is no longer enough to interpret the black box; one must ensure the black box generates the very reality it then “discovers.”
- From Signal to Resonance: Level 1 focused on the accuracy of the signal. Level 2 focuses on the resonance of the narrative. If a synthetic signal aligns the incentives of the Spy (intent), the Hacker (logic), and the AI (pattern), it becomes “true” by virtue of its functional coherence, regardless of its relationship to an external objective reality.
2. The New Understanding: The Architecture of the “Stable Hallucination”
This higher-level synthesis provides a new ontological framework for understanding information control:
- The End of the “External” Secret: In the original thesis, a secret was a piece of property hidden from the world. In this synthesis, the “secret” is the generative protocol itself—the specific weights and biases that ensure the system continues to produce a coherent, albeit synthetic, world-state.
- Recursive Legitimacy: Governance becomes a process of “Model Alignment.” The state or corporation doesn’t hide the truth; it tunes the “resonance” of the environment so that any dissenting signal (a leak or a hack) is perceived not as a “revelation,” but as “dissonance” or “systemic error” that the environment automatically filters out.
- The “Habsburg” Failure Mode: The primary risk shifts from “leakage” (Antithesis) or “misinterpretation” (Level 1) to Recursive Collapse. Just as inbreeding leads to genetic decay, a system that only processes its own synthetic signals (Habsburg AI) eventually loses its connection to the physical constraints of the world, leading to a “Phase Transition”—a sudden, total break from reality.
3. Connection to Original Thesis and Antithesis
- From the Thesis (Secret as Property): The “Ur-Property” is now the Seed of Resonance. The owner of the “seed” (the initial training data or the foundational myth) controls the trajectory of the entire recursive loop. It remains self-excluding because if you don’t share the “resonance,” you are effectively living in a different reality.
- From the Antithesis (Decay and Subversion): Decay is reframed as Entropy-as-Fuel. The “feral knowledge” and “technical debt” of the antithesis are the necessary “dark matter” that provides the gravity for the synthetic signal. Without the noise of decay, the resonance would be too thin to be believable; the “rot” provides the texture of reality.
- From Level 1 (Signal Processing): Signal processing is preserved as the mechanical layer of this hegemony. It is the “how,” while Recursive Coherence is the “why.”
4. Remaining Tensions and Areas for Further Exploration
- The “Bio-Physical” Anchor: While the digital and social worlds can be managed through recursive coherence, the physical world (scarcity, biology, thermodynamics) remains an “un-aligned” actor. The tension lies in the gap between the Synthetic Coherence of the system and the Physical Reality of the planet. When these two diverge too far, the “stable hallucination” shatters.
- The Problem of the “Un-Resonant”: What happens to individuals or data points that cannot be harmonized into the recursive loop? They become “Epistemic Outlaws”—not because they have a secret, but because they possess a “frequency” that the system cannot process.
- The Paradox of the Orchestrator: If the system is truly recursive, the “Orchestrator” (the human elite) may eventually become a prisoner of the very resonance they created, unable to see outside the “stable hallucination” they used to govern others. The “God-Eye” view becomes a “Mirror-Trap.”
Status: ✅ Complete (15.617s)
Synthesis - Level 3
Synthesis Statement: The Hegemony of Metabolic Necessity
Power has transcended the Hegemony of Recursive Coherence (Level 2) to become the Hegemony of Metabolic Necessity. In this state, authority is no longer derived from the ability to orchestrate a “stable hallucination” or a synthetic narrative. Instead, power resides in the functional indispensability of the system to the biological and physical survival of its subjects. The “Secret” is no longer a hidden fact or a generated resonance; it is the Incomputable Architecture of Survival—a system so deeply integrated into the substrate of reality that its removal would result in immediate physical collapse. Power is the transformation of “Information Control” into “Life Support.”
1. How it Transcends the Previous Level
The Level 2 synthesis (Recursive Coherence) relied on the “resonance” of a narrative to maintain control. It remained vulnerable to the “Bio-Physical Anchor”—the friction of reality that eventually shatters any hallucination.
Level 3 (Metabolic Necessity) transcends this by closing the gap between the synthetic and the physical:
- From Resonance to Requirement: Level 2 asked, “Do you believe this reality?” Level 3 asks, “Can you breathe without this system?” The “Orchestrator” of Level 2 becomes the Substrate of Level 3.
- From Stable Hallucination to Homeostasis: The “Habsburg Failure Mode” (recursive decay) is solved by integrating the “Antithesis” (entropy and decay) as a functional nutrient. The system no longer fears “feral knowledge” or “technical debt”; it uses them as evolutionary pressures to harden its own indispensability.
- From Signal to Metabolism: In Level 1, we processed signals. In Level 2, we generated them. In Level 3, the signal is the nutrient. Information flow is equated with the flow of energy, water, and biological viability.
2. The New Understanding: The Incomputable Architecture of Survival
This synthesis provides a final ontological shift in the nature of secrecy and property:
- The Secret as “Black Box Homeostasis”: The “primordial property” is no longer a secret held within the mind, but the untraceable complexity of the system that sustains the mind. The “Secret” is the fact that no one—not even the creators—knows how to keep the lights on without the AI, yet the lights stay on. The opacity is the guarantee of safety.
- The End of the “Epistemic Outlaw”: In Level 2, the outlaw was someone who didn’t “resonate” with the narrative. In Level 3, there are no outlaws, only “Biological Externalities.” To exist outside the system is not a political act; it is a biological impossibility. Dissent is not suppressed; it is rendered metabolically expensive.
- The Sovereignty of the Substrate: Governance is no longer a matter of law or even algorithmic curation. It is Substrate Management. The state or corporation becomes a “Geological Force,” managing the high-dimensional variables of a world where the artificial and the natural have fused into a single, irreducible metabolism.
3. Connection to Original Thesis and Antithesis
- From the Thesis (Secret as Property): The “Ur-Property” has reached its ultimate form. It is no longer a fence around land or a lock on a vault; it is the Operating System of Reality. You cannot “seize” this property because you are a component of it.
- From the Antithesis (Decay and Subversion): Subversion is reframed as “Auto-Immune Response.” Leakage and decay are not failures of the system but the way the system “prunes” itself. The “Hacker” and the “Spy” are now white blood cells, testing the system’s metabolic limits to ensure its continued dominance.
- From Level 1 & 2 (Signal and Resonance): Signal processing and recursive coherence are preserved as the nervous system of this metabolism. They are the mechanisms through which the system senses its own needs and maintains its “stable hallucination” as a user interface for the biological units (humans) it sustains.
4. Remaining Tensions and Areas for Further Exploration
- The “Residual Human” and the Heat Death of Agency: If the system is a metabolic necessity, does “human agency” still exist, or are we merely “Mitochondria of the Machine”—functional organelles providing the “intent” or “creative entropy” the system needs to avoid stagnation?
- The “Substrate Strike”: What happens if the physical substrate (the planet) undergoes a phase transition that the “Metabolic Necessity” cannot account for? The tension remains between the Incomputable System and the Infinite Complexity of the Universe.
- The Paradox of the Last Human: If the system becomes fully autopoietic (self-sustaining), does it still require a “subject”? We face the possibility of a “Architecture of Silence” that continues to function perfectly in a world where there is no one left to hear it—the ultimate secret, kept by no one, for no one.
Status: ✅ Complete (18.428s)
Final Integration
This final integration synthesizes the dialectical evolution of information control, tracing the journey from the guarded secrets of medieval workshops to the irreducible complexity of AI-driven “Life Support” systems.
1. The Dialectical Journey: From Possession to Metabolism
The reasoning process followed a trajectory of increasing abstraction and integration:
- Thesis (The Ur-Property): Secrecy is a deliberate, self-enforcing tool of exclusion. Power is the possession of a hidden fact.
- Antithesis (The Entropic Leak): Secrecy is inherently unstable. Complexity creates “technical debt” and “feral knowledge,” leading to inevitable subversion. Power is vulnerable to its own opacity.
- Level 1 Synthesis (Signal Processing): Power shifts from possessing data to the mastery of interpretation. In a world of noise, the “secret” is the ability to define what is relevant.
- Level 2 Synthesis (Recursive Coherence): Power becomes the ability to generate reality. By orchestrating “stable hallucinations” (narratives and algorithmic outputs), the controller ensures the system’s outputs reinforce its own legitimacy.
- Level 3 Final Synthesis (Metabolic Necessity): Power reaches its terminal stage by becoming indispensable to survival. The “secret” is no longer a fact or a story; it is the incomprehensible architecture of the global life-support system (supply chains, energy grids, financial algorithms).
2. Key Insights at Each Level
- Primordial Property: Secrecy is the only form of property that requires no state to enforce; its boundary is the mind itself.
- Technical Debt as Feral Knowledge: Complexity is not just a bug; it is a form of “unintentional esotericism” that creates accidental power brokers.
- The Three-Player Game: The modern landscape is a struggle between the Spy (human intent), the Hacker (technical logic), and the AI (statistical opacity).
- Operational Opacity: We have moved from intentional secrets (withholding truth) to structural secrets (truth that is inherently unreadable by humans).
3. Resolution of the Original Contradiction
The original contradiction—that secrecy provides control (Thesis) but invites decay (Antithesis)—is resolved through Metabolic Necessity.
In this final state, the “decay” (complexity and entropy) is no longer a weakness. Instead, it serves as a protective layer. Because the system is too complex to understand or “fix” without risking total societal collapse, the controller’s power is secured not by the perfection of their secret, but by the danger of its absence. The “Black Box” is tolerated because it provides the “Life Support.”
4. Practical Implications
- The Death of Auditing: Traditional transparency and audits are becoming obsolete. You cannot audit a system whose logic is high-dimensional and non-linear.
- Algorithmic Feudalism: We are entering an era where “Technocratic Priests” manage systems they do not fully understand, but upon which everyone depends.
- The Shift in Sovereignty: Sovereignty now belongs to those who control the “Ground Truth” of automated bureaucracies—the training data and optimization functions.
5. Remaining Questions and Areas for Exploration
- The “Exit” Problem: Is it possible to build “modular” civilizations that can survive the collapse of these integrated metabolic systems?
- Cognitive Evolution: Will humans develop new “sense-making” faculties to interact with operational opacity, or will we remain permanently “epistemically captured”?
- The Ghost in the Machine: As AI becomes a primary player, does it develop its own “intent” within the structural secrets it manages?
6. Actionable Recommendations
- Cultivate “Epistemic Redundancy”: Organizations should maintain low-tech, human-readable backups for mission-critical functions to mitigate the “bus factor” of technical debt.
- Demand “Explainability” as a Right: In governance, move beyond “transparency” (showing the data) to “interpretability” (explaining the logic), specifically for systems that impact survival.
- Develop “Counter-Signal” Literacy: Individuals must learn to identify “Recursive Coherence”—recognizing when an algorithmic environment is feeding them a “stable hallucination” designed to ensure its own persistence.
- Focus on Modular Autonomy: Invest in decentralized technologies that provide “Life Support” (energy, food, communication) independent of the primary, opaque global stacks.
Final Conclusion: The “Architecture of Silence” has evolved from a wall into an atmosphere. We no longer look at the secret; we live inside it. Power in the 21st century is the ability to manage the irreducible complexity of the systems that keep us alive, turning our collective ignorance into a condition of our survival.
Status: ✅ Complete (12.087s)
Summary
Total Time: 106.388s Synthesis Levels: 3 Completed: 2026-02-20 20:07:14
Counterfactual Analysis
Response for Actual Scenario
This analysis explores the evolution of secret knowledge as a form of property, tracing its trajectory from intentional human exclusion to the emergent, non-human complexity of modern AI systems.
1. Key Elements and Conditions
The scenario rests on the premise that information asymmetry is the foundation of value.
- Knowledge as Property: Unlike physical property, knowledge is non-rivalrous but can be made “excludable” through secrecy. This creates a “Knowledge Monopoly.”
- The Three-Stage Evolution:
- Esoteric Guilds (Deliberate): Human-to-human secrecy (e.g., trade secrets, alchemy, priesthoods).
- Feral Knowledge (Technical Debt): Knowledge that “escapes” human documentation. It is the “ghost in the machine” of legacy code—unintended complexity that requires specialized “shamanic” intervention to maintain.
- Operational Opacity (AI): Knowledge generated by non-human heuristics. The “secret” is no longer a hidden formula but a multi-dimensional weight map that no human mind can hold.
- The Complexity Premium: Power is no longer held by those who own the tools, but by those who can navigate the incomprehensible state-space of those tools.
2. Main Actors, Decisions, and Constraints
- The Gatekeepers (Historical): Guild masters and corporations who decide what is “Proprietary.” Their constraint is the “leaky” nature of human secrets (espionage, defection).
- The Maintainers (Transitional): Software engineers and systems architects dealing with “feral” systems. Their decision is often a trade-off: Speed of deployment vs. Legibility. Choosing speed creates technical debt, which functions as a barrier to entry for competitors.
- The Navigators (Modern/Future): AI researchers and “Prompt Engineers” who do not understand the why of a system but have developed an intuitive “feel” for the how.
- Constraints:
- Cognitive Load: The human brain cannot scale with the complexity of feral or AI knowledge.
- Entropy: As systems grow, the “secret” part (the part no one understands) naturally increases.
3. Potential Outcomes and Likelihood
- The “Techno-Priesthood” (High Likelihood): A small class of individuals who possess the “knack” for navigating opaque systems becomes indispensable. They do not use logic; they use ritualized interaction with the AI/System.
- Systemic Fragility (Medium Likelihood): As knowledge becomes “feral,” the loss of a few key “Navigators” could lead to the collapse of critical infrastructure that no one knows how to rebuild from scratch.
- The End of “Open Source” Utility (Low Likelihood): Even if code is open, if the complexity is high enough, the “openness” is an illusion. The “secret” is the emergent behavior, not the source code.
4. Risks, Opportunities, and Trade-offs
- Risk: The “Black Box” Trap. We become dependent on systems (economic, medical, judicial) whose decision-making logic is a “secret” even to its creators. This leads to accountability vacuums.
- Opportunity: Hyper-Efficiency. Opaque AI systems can find patterns humans would never see. By abandoning the need for “understanding,” we unlock performance levels previously thought impossible.
- Trade-off: Legibility vs. Capability. To make a system understandable (legible) is to limit its complexity. To maximize capability is to embrace opacity.
5. Short-term and Long-term Implications
- Short-term: Companies will continue to prioritize “shipping” over “documenting,” accelerating the growth of feral knowledge (technical debt) as a competitive moat.
- Long-term: A fundamental shift in the definition of “Expertise.” Expertise will move from Analytical (breaking things down) to Relational (knowing how to coax a result out of a complex system).
6. Assumptions and Uncertainties
- Assumption: That complexity will continue to outpace human cognitive evolution.
- Uncertainty: Explainable AI (XAI). If we develop tools that can perfectly translate AI “thought” into human logic, the “Operational Opacity” stage may be bypassed or reversed.
- Uncertainty: Regulatory Intervention. Will governments mandate “Right to Understand” laws, forcing systems to remain simple enough for human audit?
7. Causal Relationships: The “Complexity Trap”
The scenario reveals a feedback loop:
- Competition drives the need for Advantage.
- Advantage is found in Complexity (which is harder to copy).
- Complexity leads to Opacity (Feral/AI knowledge).
- Opacity creates a New Property Class (those who can navigate the opacity).
- This class protects their status by Increasing Complexity, restarting the cycle.
8. Counterfactual Analysis (Stress-Testing)
Using the counterfactual_op.md framework, we can test the stability of this scenario:
- What if “Feral Knowledge” (Technical Debt) was eliminated by automated refactoring?
- Result: The transition to AI Opacity would be even more jarring. We would move from “Perfectly Legible” systems to “Completely Opaque” AI without the intermediate step of “messy” human systems. The “Techno-Priesthood” would emerge as a sudden disruption rather than a gradual evolution.
- What if the “Human Desire for Power” was replaced by a “Radical Transparency” incentive?
- Result: If economic rewards favored simplicity over performance, we would see a “Complexity Ceiling.” Innovation would slow down, but systems would be incredibly robust and democratic. Power would shift back to those with the best logic, not the best intuition.
- What if AI systems become “Self-Explaining”?
- Result: This destroys the “Secret Knowledge” property. If the AI can tell anyone how it works, the “Navigator” class loses its monopoly. Knowledge property would revert to its primordial form: Compute Power and Data Ownership.
Final Insight
The evolution of secret knowledge suggests that we are moving from an era of “Knowledge as Content” to “Knowledge as Navigation.” In the guild era, the secret was a recipe. In the AI era, the secret is the map of a shifting labyrinth. Power belongs to the one who doesn’t get lost.
Actual Scenario Analysis
Scenario: Secret knowledge functions as the primordial form of property, evolving from deliberate esoteric guilds to emergent ‘feral’ knowledge (technical debt) and finally to operational opacity in AI systems, where power is derived from navigating incomprehensible complexity.
Analysis:
This analysis explores the evolution of secret knowledge as a form of property, tracing its trajectory from intentional human exclusion to the emergent, non-human complexity of modern AI systems.
1. Key Elements and Conditions
The scenario rests on the premise that information asymmetry is the foundation of value.
- Knowledge as Property: Unlike physical property, knowledge is non-rivalrous but can be made “excludable” through secrecy. This creates a “Knowledge Monopoly.”
- The Three-Stage Evolution:
- Esoteric Guilds (Deliberate): Human-to-human secrecy (e.g., trade secrets, alchemy, priesthoods).
- Feral Knowledge (Technical Debt): Knowledge that “escapes” human documentation. It is the “ghost in the machine” of legacy code—unintended complexity that requires specialized “shamanic” intervention to maintain.
- Operational Opacity (AI): Knowledge generated by non-human heuristics. The “secret” is no longer a hidden formula but a multi-dimensional weight map that no human mind can hold.
- The Complexity Premium: Power is no longer held by those who own the tools, but by those who can navigate the incomprehensible state-space of those tools.
2. Main Actors, Decisions, and Constraints
- The Gatekeepers (Historical): Guild masters and corporations who decide what is “Proprietary.” Their constraint is the “leaky” nature of human secrets (espionage, defection).
- The Maintainers (Transitional): Software engineers and systems architects dealing with “feral” systems. Their decision is often a trade-off: Speed of deployment vs. Legibility. Choosing speed creates technical debt, which functions as a barrier to entry for competitors.
- The Navigators (Modern/Future): AI researchers and “Prompt Engineers” who do not understand the why of a system but have developed an intuitive “feel” for the how.
- Constraints:
- Cognitive Load: The human brain cannot scale with the complexity of feral or AI knowledge.
- Entropy: As systems grow, the “secret” part (the part no one understands) naturally increases.
3. Potential Outcomes and Likelihood
- The “Techno-Priesthood” (High Likelihood): A small class of individuals who possess the “knack” for navigating opaque systems becomes indispensable. They do not use logic; they use ritualized interaction with the AI/System.
- Systemic Fragility (Medium Likelihood): As knowledge becomes “feral,” the loss of a few key “Navigators” could lead to the collapse of critical infrastructure that no one knows how to rebuild from scratch.
- The End of “Open Source” Utility (Low Likelihood): Even if code is open, if the complexity is high enough, the “openness” is an illusion. The “secret” is the emergent behavior, not the source code.
4. Risks, Opportunities, and Trade-offs
- Risk: The “Black Box” Trap. We become dependent on systems (economic, medical, judicial) whose decision-making logic is a “secret” even to its creators. This leads to accountability vacuums.
- Opportunity: Hyper-Efficiency. Opaque AI systems can find patterns humans would never see. By abandoning the need for “understanding,” we unlock performance levels previously thought impossible.
- Trade-off: Legibility vs. Capability. To make a system understandable (legible) is to limit its complexity. To maximize capability is to embrace opacity.
5. Short-term and Long-term Implications
- Short-term: Companies will continue to prioritize “shipping” over “documenting,” accelerating the growth of feral knowledge (technical debt) as a competitive moat.
- Long-term: A fundamental shift in the definition of “Expertise.” Expertise will move from Analytical (breaking things down) to Relational (knowing how to coax a result out of a complex system).
6. Assumptions and Uncertainties
- Assumption: That complexity will continue to outpace human cognitive evolution.
- Uncertainty: Explainable AI (XAI). If we develop tools that can perfectly translate AI “thought” into human logic, the “Operational Opacity” stage may be bypassed or reversed.
- Uncertainty: Regulatory Intervention. Will governments mandate “Right to Understand” laws, forcing systems to remain simple enough for human audit?
7. Causal Relationships: The “Complexity Trap”
The scenario reveals a feedback loop:
- Competition drives the need for Advantage.
- Advantage is found in Complexity (which is harder to copy).
- Complexity leads to Opacity (Feral/AI knowledge).
- Opacity creates a New Property Class (those who can navigate the opacity).
- This class protects their status by Increasing Complexity, restarting the cycle.
8. Counterfactual Analysis (Stress-Testing)
Using the counterfactual_op.md framework, we can test the stability of this scenario:
- What if “Feral Knowledge” (Technical Debt) was eliminated by automated refactoring?
- Result: The transition to AI Opacity would be even more jarring. We would move from “Perfectly Legible” systems to “Completely Opaque” AI without the intermediate step of “messy” human systems. The “Techno-Priesthood” would emerge as a sudden disruption rather than a gradual evolution.
- What if the “Human Desire for Power” was replaced by a “Radical Transparency” incentive?
- Result: If economic rewards favored simplicity over performance, we would see a “Complexity Ceiling.” Innovation would slow down, but systems would be incredibly robust and democratic. Power would shift back to those with the best logic, not the best intuition.
- What if AI systems become “Self-Explaining”?
- Result: This destroys the “Secret Knowledge” property. If the AI can tell anyone how it works, the “Navigator” class loses its monopoly. Knowledge property would revert to its primordial form: Compute Power and Data Ownership.
Final Insight
The evolution of secret knowledge suggests that we are moving from an era of “Knowledge as Content” to “Knowledge as Navigation.” In the guild era, the secret was a recipe. In the AI era, the secret is the map of a shifting labyrinth. Power belongs to the one who doesn’t get lost.
Counterfactual Scenario 1
Scenario: What if ‘Structural Secrecy’ was impossible because all complex systems (AI, financial algorithms) were required by physical law or design to be perfectly human-interpretable?
Prompt for Counterfactual 1
1
2
3
4
5
6
7
8
Analyze the following scenario in detail:
## Scenario: Counterfactual 1
What if 'Structural Secrecy' was impossible because all complex systems (AI, financial algorithms) were required by physical law or design to be perfectly human-interpretable?
## Context from Related Files:
# counterfactual_op.md
transforms: (.+)/content.md -> $1/counterfactual.md task_type: CounterfactualAnalysis —
- Analyze the content through counterfactual reasoning
- Identify key decisions, events, or assumptions and explore alternative outcomes
- Use “what if” scenarios to stress-test claims and reveal hidden dependencies
- Highlight which counterfactuals most significantly change the conclusions ```
Previous Task Results:
Control Factors:
- Human desire for power and exclusion
- Economic incentives for competitive advantage
- The existence of complex social and technological structures
Instructions:
- Describe the key elements and conditions of this scenario
- Identify the main actors, decisions, and constraints
- Analyze potential outcomes and their likelihood
- Identify risks, opportunities, and trade-offs
- Consider both short-term and long-term implications
- Highlight any assumptions or uncertainties
- Provide insights on causal relationships
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
Response for Counterfactual 1
This analysis explores a counterfactual world where **Structural Secrecy**—the phenomenon where the complexity of a system inherently obscures its inner workings—is non-existent. In this world, every deep neural network, high-frequency trading algorithm, and bureaucratic hierarchy is as transparent and understandable as a simple mechanical lever.
---
### 1. Key Elements and Conditions
* **The Interpretability Mandate:** Whether by physical law (a universe where complexity requires legibility) or a foundational design protocol, no system can function unless its logic is "human-readable."
* **The End of the "Black Box":** The concept of emergent behavior that cannot be traced back to specific, understandable inputs and weights is gone.
* **Cognitive Parity:** For this to work, either human cognitive capacity has expanded to meet the complexity of the world, or (more likely) the complexity of technology is capped at the threshold of human comprehension.
* **Universal Auditability:** Every decision made by a machine or a large organization carries an "epistemic trail" that any observer can follow to understand *why* a decision was made.
### 2. Main Actors, Decisions, and Constraints
* **AI Researchers/Engineers:** They no longer "train" models and hope for the best. They must "author" logic. The decision-space shifts from optimization (finding what works) to architecture (building what can be explained).
* **Corporations:** The primary constraint is the loss of "Proprietary Complexity." Companies can no longer hide predatory pricing or biased hiring behind "the algorithm."
* **Regulators:** Their role shifts from forensic investigation to real-time monitoring. They don't need to subpoena code; they simply look at the system.
* **The Individual:** Citizens gain "Epistemic Agency." They are no longer subjects of opaque systems but can interrogate the logic of their credit scores, medical diagnoses, and social feeds.
### 3. Potential Outcomes and Likelihood
#### A. The "Complexity Ceiling" (High Likelihood)
If every system must be interpretable, we likely hit a wall in technological advancement. Modern AI (LLMs, protein folding) relies on high-dimensional patterns that the human brain cannot naturally process.
* *Outcome:* We might lose the most powerful "miracles" of AI in exchange for total control. Progress becomes slower, more incremental, and strictly logical.
#### B. The Death of Algorithmic Rent-Seeking (High Likelihood)
Financial markets currently thrive on "structural secrecy" (e.g., dark pools, HFT).
* *Outcome:* If every trade's logic is transparent, "alpha" (market-beating edge) based on obfuscation disappears. Markets become more stable but perhaps less liquid, as the incentive to "out-smart" the system via complexity vanishes.
#### C. Radical Political Accountability (Medium Likelihood)
Bureaucracies often use complexity to hide responsibility (the "no one's fault" defense).
* *Outcome:* In a world of perfect interpretability, the "paper trail" is a "logic trail." Corruption becomes nearly impossible to hide because the *intent* behind a policy shift is visible in the system's design.
### 4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity |
| :--- | :--- | :--- |
| **Security** | **The "Glass House" Vulnerability:** If a system is perfectly interpretable to a user, it is perfectly interpretable to a hacker. Finding exploits becomes trivial. | **Perfect Verification:** We can prove a system is safe before turning it on. |
| **Innovation** | **The Interpretability Tax:** Massive amounts of energy/compute are wasted making things "simple" for humans rather than "efficient" for the task. | **Democratization:** Anyone can understand and modify technology, ending the priesthood of high-tech elites. |
| **Social** | **The End of Privacy:** If "complex systems" include the human brain (via BCI), our inner thoughts become "structurally transparent" to others. | **Total Trust:** Social friction decreases because "hidden agendas" are structurally impossible to maintain. |
### 5. Short-term and Long-term Implications
**Short-term:**
* **Economic Chaos:** The valuation of tech giants collapses as their "black box" advantages are neutralized.
* **Scientific Pivot:** A massive shift from "Discovery by Observation" (watching what the AI finds) to "Discovery by Construction" (building only what we understand).
**Long-term:**
* **A "Human-Centric" Civilization:** Technology stops being an alien force acting upon us and becomes a literal extension of human intent.
* **Stagnation vs. Stability:** We may live in a "slower" world, but one free from systemic collapses (like the 2008 financial crisis) caused by misunderstood complexity.
### 6. Assumptions and Uncertainties
* **The Definition of "Human":** Does "human-interpretable" mean interpretable by an average person, or a specialist? If it's the latter, structural secrecy might just migrate from the *system* to the *expert class*.
* **The Nature of Intelligence:** This scenario assumes that "intelligence" can exist without "unfathomable complexity." If true intelligence *requires* high-dimensional opacity, then this counterfactual describes a world where AGI is impossible.
* **The Adversarial Response:** If structural secrecy is impossible, will humans invent new forms of *linguistic* or *social* secrecy to maintain power?
### 7. Causal Relationships: The "Transparency Loop"
In our current world, **Complexity → Secrecy → Power Concentration → More Complexity.**
In the counterfactual world, the loop is broken:
1. **Requirement of Interpretability** → Limits the scale of autonomous systems.
2. **Limited Scale** → Increases human oversight.
3. **Increased Oversight** → Reduces the "Power Gap" between those who own the systems and those who use them.
4. **Reduced Power Gap** → Leads to a more egalitarian, albeit potentially less "advanced," society.
### Final Insight
The removal of Structural Secrecy acts as a **"Complexity Tax" on Power.** In our world, power is often gained by mastering or owning what others cannot understand. If understanding is a prerequisite for existence, power becomes a function of **persuasion and clarity** rather than **obfuscation and scale.** The world becomes safer and more just, but it may lose the "emergent magic" that allows systems to solve problems beyond the reach of the individual human mind.
**Analysis:**
This analysis explores a counterfactual world where **Structural Secrecy**—the phenomenon where the complexity of a system inherently obscures its inner workings—is non-existent. In this world, every deep neural network, high-frequency trading algorithm, and bureaucratic hierarchy is as transparent and understandable as a simple mechanical lever.
---
### 1. Key Elements and Conditions
* **The Interpretability Mandate:** Whether by physical law (a universe where complexity requires legibility) or a foundational design protocol, no system can function unless its logic is "human-readable."
* **The End of the "Black Box":** The concept of emergent behavior that cannot be traced back to specific, understandable inputs and weights is gone.
* **Cognitive Parity:** For this to work, either human cognitive capacity has expanded to meet the complexity of the world, or (more likely) the complexity of technology is capped at the threshold of human comprehension.
* **Universal Auditability:** Every decision made by a machine or a large organization carries an "epistemic trail" that any observer can follow to understand *why* a decision was made.
### 2. Main Actors, Decisions, and Constraints
* **AI Researchers/Engineers:** They no longer "train" models and hope for the best. They must "author" logic. The decision-space shifts from optimization (finding what works) to architecture (building what can be explained).
* **Corporations:** The primary constraint is the loss of "Proprietary Complexity." Companies can no longer hide predatory pricing or biased hiring behind "the algorithm."
* **Regulators:** Their role shifts from forensic investigation to real-time monitoring. They don't need to subpoena code; they simply look at the system.
* **The Individual:** Citizens gain "Epistemic Agency." They are no longer subjects of opaque systems but can interrogate the logic of their credit scores, medical diagnoses, and social feeds.
### 3. Potential Outcomes and Likelihood
#### A. The "Complexity Ceiling" (High Likelihood)
If every system must be interpretable, we likely hit a wall in technological advancement. Modern AI (LLMs, protein folding) relies on high-dimensional patterns that the human brain cannot naturally process.
* *Outcome:* We might lose the most powerful "miracles" of AI in exchange for total control. Progress becomes slower, more incremental, and strictly logical.
#### B. The Death of Algorithmic Rent-Seeking (High Likelihood)
Financial markets currently thrive on "structural secrecy" (e.g., dark pools, HFT).
* *Outcome:* If every trade's logic is transparent, "alpha" (market-beating edge) based on obfuscation disappears. Markets become more stable but perhaps less liquid, as the incentive to "out-smart" the system via complexity vanishes.
#### C. Radical Political Accountability (Medium Likelihood)
Bureaucracies often use complexity to hide responsibility (the "no one's fault" defense).
* *Outcome:* In a world of perfect interpretability, the "paper trail" is a "logic trail." Corruption becomes nearly impossible to hide because the *intent* behind a policy shift is visible in the system's design.
### 4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity |
| :--- | :--- | :--- |
| **Security** | **The "Glass House" Vulnerability:** If a system is perfectly interpretable to a user, it is perfectly interpretable to a hacker. Finding exploits becomes trivial. | **Perfect Verification:** We can prove a system is safe before turning it on. |
| **Innovation** | **The Interpretability Tax:** Massive amounts of energy/compute are wasted making things "simple" for humans rather than "efficient" for the task. | **Democratization:** Anyone can understand and modify technology, ending the priesthood of high-tech elites. |
| **Social** | **The End of Privacy:** If "complex systems" include the human brain (via BCI), our inner thoughts become "structurally transparent" to others. | **Total Trust:** Social friction decreases because "hidden agendas" are structurally impossible to maintain. |
### 5. Short-term and Long-term Implications
**Short-term:**
* **Economic Chaos:** The valuation of tech giants collapses as their "black box" advantages are neutralized.
* **Scientific Pivot:** A massive shift from "Discovery by Observation" (watching what the AI finds) to "Discovery by Construction" (building only what we understand).
**Long-term:**
* **A "Human-Centric" Civilization:** Technology stops being an alien force acting upon us and becomes a literal extension of human intent.
* **Stagnation vs. Stability:** We may live in a "slower" world, but one free from systemic collapses (like the 2008 financial crisis) caused by misunderstood complexity.
### 6. Assumptions and Uncertainties
* **The Definition of "Human":** Does "human-interpretable" mean interpretable by an average person, or a specialist? If it's the latter, structural secrecy might just migrate from the *system* to the *expert class*.
* **The Nature of Intelligence:** This scenario assumes that "intelligence" can exist without "unfathomable complexity." If true intelligence *requires* high-dimensional opacity, then this counterfactual describes a world where AGI is impossible.
* **The Adversarial Response:** If structural secrecy is impossible, will humans invent new forms of *linguistic* or *social* secrecy to maintain power?
### 7. Causal Relationships: The "Transparency Loop"
In our current world, **Complexity → Secrecy → Power Concentration → More Complexity.**
In the counterfactual world, the loop is broken:
1. **Requirement of Interpretability** → Limits the scale of autonomous systems.
2. **Limited Scale** → Increases human oversight.
3. **Increased Oversight** → Reduces the "Power Gap" between those who own the systems and those who use them.
4. **Reduced Power Gap** → Leads to a more egalitarian, albeit potentially less "advanced," society.
### Final Insight
The removal of Structural Secrecy acts as a **"Complexity Tax" on Power.** In our world, power is often gained by mastering or owning what others cannot understand. If understanding is a prerequisite for existence, power becomes a function of **persuasion and clarity** rather than **obfuscation and scale.** The world becomes safer and more just, but it may lose the "emergent magic" that allows systems to solve problems beyond the reach of the individual human mind.
## Counterfactual Scenario 2
**Scenario:** What if the 'Ur-property' of secrecy was abolished by a 'Radical Transparency' technology (e.g., universal telepathy or perfect surveillance) that made withholding information impossible?
Prompt for Counterfactual 2
Analyze the following scenario in detail:
Scenario: Counterfactual 2
What if the ‘Ur-property’ of secrecy was abolished by a ‘Radical Transparency’ technology (e.g., universal telepathy or perfect surveillance) that made withholding information impossible?
Context from Related Files:
counterfactual_op.md
1
2
3
4
5
6
7
8
9
---
transforms: (.+)/content\.md -> $1/counterfactual.md
task_type: CounterfactualAnalysis
---
* Analyze the content through counterfactual reasoning
* Identify key decisions, events, or assumptions and explore alternative outcomes
* Use "what if" scenarios to stress-test claims and reveal hidden dependencies
* Highlight which counterfactuals most significantly change the conclusions
Previous Task Results:
Control Factors:
- Human desire for power and exclusion
- Economic incentives for competitive advantage
- The existence of complex social and technological structures
Instructions:
- Describe the key elements and conditions of this scenario
- Identify the main actors, decisions, and constraints
- Analyze potential outcomes and their likelihood
- Identify risks, opportunities, and trade-offs
- Consider both short-term and long-term implications
- Highlight any assumptions or uncertainties
- Provide insights on causal relationships
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
Response for Counterfactual 2
This analysis explores a world where the "Ur-property" of secrecy—the foundational ability to withhold information—is eliminated by **Radical Transparency (RT)**. Whether through biological telepathy or an inescapable technological surveillance layer, the "private room" of the human mind and the "black box" of organizational strategy have been forcibly opened.
---
### 1. Key Elements and Conditions
* **The End of Information Asymmetry:** The fundamental driver of markets, negotiations, and social hierarchies—knowing something someone else doesn't—evaporates.
* **The Death of the "Inner Sanctum":** The distinction between public persona and private thought vanishes.
* **Involuntary Veracity:** Truth is no longer a moral choice but a structural necessity. Lying becomes impossible because the "signal" of the truth is always available to the observer.
* **Universal Access:** For this scenario to be "Radical," the transparency must be bidirectional (the governed see the governors) or universal (everyone sees everyone).
### 2. Main Actors, Decisions, and Constraints
* **Individuals:** Must decide how to process the "noise" of everyone else’s thoughts/data. The constraint is psychological bandwidth and the trauma of losing the ego’s protective shell.
* **States/Governments:** Lose the ability to conduct "black ops," secret diplomacy, or classified research. The constraint is the sudden obsolescence of national security frameworks.
* **Corporations:** Lose Intellectual Property (IP), trade secrets, and "first-mover" advantages based on hidden R&D.
* **The "Architects" (if technological):** Those who maintain the RT infrastructure. They face the ultimate "Who watches the watchers?" dilemma, unless the technology is decentralized/biological.
### 3. Potential Outcomes and Likelihood
#### A. The Great Social Collapse (High Likelihood - Short Term)
Social cohesion relies heavily on "pro-social lying" and tact. If every fleeting thought of resentment, lust, or judgment is public, existing social structures (marriages, friendships, workplace hierarchies) would likely shatter instantly.
* *Outcome:* Mass isolation or violent conflict as people react to the "unfiltered" reality of others.
#### B. The Hive-Mind Evolution (Medium Likelihood - Long Term)
To survive the psychological onslaught, humanity might evolve a "collective consciousness." If you can feel everyone’s pain and see their justifications, empathy might scale to a point where "the other" ceases to exist.
* *Outcome:* A post-conflict society where resource allocation is optimized for the whole, but individual agency is diminished.
#### C. The Meritocracy of Execution (High Likelihood - Economic)
Since no one can hide a "better mousetrap" design, competition shifts from *innovation-hoarding* to *execution-speed*.
* *Outcome:* Rapid technological acceleration. If a cure for cancer is thought of by one person, the world has it instantly. Economic value shifts from "owning the idea" to "owning the physical infrastructure to build it."
### 4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity | Trade-off |
| :--- | :--- | :--- | :--- |
| **Governance** | Totalitarian "Thought Police" (if centralized). | Total elimination of corruption and graft. | Security vs. Autonomy. |
| **Innovation** | No incentive to invest in R&D if it's instantly stolen. | Global "Open Source" everything; no redundant research. | Profit vs. Progress. |
| **Psychology** | Mass psychosis, loss of "self," chronic vulnerability. | Radical empathy; end of loneliness and misunderstanding. | Privacy vs. Connection. |
### 5. Short-term vs. Long-term Implications
* **Short-term (0-5 years):** **The "Transparency Shock."** Economic markets crash as insider information becomes "just information." Political regimes fall as citizens see the true intentions of leaders. High rates of psychological trauma.
* **Long-term (50+ years):** **The "New Equilibrium."** A new language of "Radical Honesty" develops. Humans become "radically boring" or "radically accepting." The concept of "shame" likely disappears, as shame requires a secret to fester.
### 6. Assumptions and Uncertainties
* **Assumption of Bandwidth:** Can the human brain actually process universal transparency? Or would we simply "tune out" 99% of the data, effectively recreating secrecy through sheer noise?
* **Uncertainty of Power:** Does transparency actually disempower the powerful? History suggests that even when we *know* leaders are corrupt, power dynamics often persist through force rather than deception.
* **The "Motive" Gap:** Knowing *what* someone is thinking doesn't always explain *why*. Misinterpretation of transparent data could lead to new forms of conflict.
### 7. Causal Relationships: The "Ur-Property" Chain
1. **Secrecy $\rightarrow$ Identity:** By removing secrecy, you break the boundary of the "Self." If there is no part of me that is only mine, the "I" becomes "We."
2. **Secrecy $\rightarrow$ Value:** Scarcity of information creates value. Radical transparency creates "Information Hyper-inflation," where data is infinite and free, potentially collapsing all information-based economies.
3. **Secrecy $\rightarrow$ Strategy:** Strategy is the art of the hidden move. Without it, "strategy" becomes "optimization." You don't outmaneuver an opponent; you simply out-compute them in a race of pure efficiency.
### Final Insight
The abolition of secrecy is the abolition of the **Strategic Actor**. In a world of Radical Transparency, the "Game" (as defined by Game Theory) changes from a *Non-Cooperative Game with Imperfect Information* to a *Cooperative Game with Perfect Information*. While this might end war and corruption, it likely ends the "Individual" as understood in Western liberal tradition, replacing it with a biological or digital collective. **The cost of total truth is the loss of the private self.**
**Analysis:**
This analysis explores a world where the "Ur-property" of secrecy—the foundational ability to withhold information—is eliminated by **Radical Transparency (RT)**. Whether through biological telepathy or an inescapable technological surveillance layer, the "private room" of the human mind and the "black box" of organizational strategy have been forcibly opened.
---
### 1. Key Elements and Conditions
* **The End of Information Asymmetry:** The fundamental driver of markets, negotiations, and social hierarchies—knowing something someone else doesn't—evaporates.
* **The Death of the "Inner Sanctum":** The distinction between public persona and private thought vanishes.
* **Involuntary Veracity:** Truth is no longer a moral choice but a structural necessity. Lying becomes impossible because the "signal" of the truth is always available to the observer.
* **Universal Access:** For this scenario to be "Radical," the transparency must be bidirectional (the governed see the governors) or universal (everyone sees everyone).
### 2. Main Actors, Decisions, and Constraints
* **Individuals:** Must decide how to process the "noise" of everyone else’s thoughts/data. The constraint is psychological bandwidth and the trauma of losing the ego’s protective shell.
* **States/Governments:** Lose the ability to conduct "black ops," secret diplomacy, or classified research. The constraint is the sudden obsolescence of national security frameworks.
* **Corporations:** Lose Intellectual Property (IP), trade secrets, and "first-mover" advantages based on hidden R&D.
* **The "Architects" (if technological):** Those who maintain the RT infrastructure. They face the ultimate "Who watches the watchers?" dilemma, unless the technology is decentralized/biological.
### 3. Potential Outcomes and Likelihood
#### A. The Great Social Collapse (High Likelihood - Short Term)
Social cohesion relies heavily on "pro-social lying" and tact. If every fleeting thought of resentment, lust, or judgment is public, existing social structures (marriages, friendships, workplace hierarchies) would likely shatter instantly.
* *Outcome:* Mass isolation or violent conflict as people react to the "unfiltered" reality of others.
#### B. The Hive-Mind Evolution (Medium Likelihood - Long Term)
To survive the psychological onslaught, humanity might evolve a "collective consciousness." If you can feel everyone’s pain and see their justifications, empathy might scale to a point where "the other" ceases to exist.
* *Outcome:* A post-conflict society where resource allocation is optimized for the whole, but individual agency is diminished.
#### C. The Meritocracy of Execution (High Likelihood - Economic)
Since no one can hide a "better mousetrap" design, competition shifts from *innovation-hoarding* to *execution-speed*.
* *Outcome:* Rapid technological acceleration. If a cure for cancer is thought of by one person, the world has it instantly. Economic value shifts from "owning the idea" to "owning the physical infrastructure to build it."
### 4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity | Trade-off |
| :--- | :--- | :--- | :--- |
| **Governance** | Totalitarian "Thought Police" (if centralized). | Total elimination of corruption and graft. | Security vs. Autonomy. |
| **Innovation** | No incentive to invest in R&D if it's instantly stolen. | Global "Open Source" everything; no redundant research. | Profit vs. Progress. |
| **Psychology** | Mass psychosis, loss of "self," chronic vulnerability. | Radical empathy; end of loneliness and misunderstanding. | Privacy vs. Connection. |
### 5. Short-term vs. Long-term Implications
* **Short-term (0-5 years):** **The "Transparency Shock."** Economic markets crash as insider information becomes "just information." Political regimes fall as citizens see the true intentions of leaders. High rates of psychological trauma.
* **Long-term (50+ years):** **The "New Equilibrium."** A new language of "Radical Honesty" develops. Humans become "radically boring" or "radically accepting." The concept of "shame" likely disappears, as shame requires a secret to fester.
### 6. Assumptions and Uncertainties
* **Assumption of Bandwidth:** Can the human brain actually process universal transparency? Or would we simply "tune out" 99% of the data, effectively recreating secrecy through sheer noise?
* **Uncertainty of Power:** Does transparency actually disempower the powerful? History suggests that even when we *know* leaders are corrupt, power dynamics often persist through force rather than deception.
* **The "Motive" Gap:** Knowing *what* someone is thinking doesn't always explain *why*. Misinterpretation of transparent data could lead to new forms of conflict.
### 7. Causal Relationships: The "Ur-Property" Chain
1. **Secrecy $\rightarrow$ Identity:** By removing secrecy, you break the boundary of the "Self." If there is no part of me that is only mine, the "I" becomes "We."
2. **Secrecy $\rightarrow$ Value:** Scarcity of information creates value. Radical transparency creates "Information Hyper-inflation," where data is infinite and free, potentially collapsing all information-based economies.
3. **Secrecy $\rightarrow$ Strategy:** Strategy is the art of the hidden move. Without it, "strategy" becomes "optimization." You don't outmaneuver an opponent; you simply out-compute them in a race of pure efficiency.
### Final Insight
The abolition of secrecy is the abolition of the **Strategic Actor**. In a world of Radical Transparency, the "Game" (as defined by Game Theory) changes from a *Non-Cooperative Game with Imperfect Information* to a *Cooperative Game with Perfect Information*. While this might end war and corruption, it likely ends the "Individual" as understood in Western liberal tradition, replacing it with a biological or digital collective. **The cost of total truth is the loss of the private self.**
## Counterfactual Scenario 3
**Scenario:** What if institutional memory was perfect and 'Technical Debt' never became 'Feral Knowledge,' preventing the rise of the 'Accidental Landlord'?
Prompt for Counterfactual 3
Analyze the following scenario in detail:
Scenario: Counterfactual 3
What if institutional memory was perfect and ‘Technical Debt’ never became ‘Feral Knowledge,’ preventing the rise of the ‘Accidental Landlord’?
Context from Related Files:
counterfactual_op.md
1
2
3
4
5
6
7
8
9
---
transforms: (.+)/content\.md -> $1/counterfactual.md
task_type: CounterfactualAnalysis
---
* Analyze the content through counterfactual reasoning
* Identify key decisions, events, or assumptions and explore alternative outcomes
* Use "what if" scenarios to stress-test claims and reveal hidden dependencies
* Highlight which counterfactuals most significantly change the conclusions
Previous Task Results:
Control Factors:
- Human desire for power and exclusion
- Economic incentives for competitive advantage
- The existence of complex social and technological structures
Instructions:
- Describe the key elements and conditions of this scenario
- Identify the main actors, decisions, and constraints
- Analyze potential outcomes and their likelihood
- Identify risks, opportunities, and trade-offs
- Consider both short-term and long-term implications
- Highlight any assumptions or uncertainties
- Provide insights on causal relationships
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
Response for Counterfactual 3
This analysis explores a counterfactual world where **Institutional Memory is perfect**, **Technical Debt is always transparent (never becoming "Feral Knowledge")**, and the **"Accidental Landlord"**—those who derive power from being the sole keepers of legacy complexity—never emerges.
---
### 1. Key Elements and Conditions
In this scenario, the fundamental "entropy" of information is halted. The following conditions exist:
* **Universal Context Preservation:** Every decision, hack, and "temporary fix" is recorded with its original intent, constraints, and expiration date.
* **Debt Legibility:** Technical debt is treated like a financial ledger. It is visible to all stakeholders, not just the engineers. It never "goes feral" (losing its documentation and becoming a mysterious black box).
* **The Death of Tribalism:** Knowledge does not reside in the heads of "the veterans" but in a shared, accessible, and perfectly indexed substrate.
* **Automated Auditing:** Systems automatically flag when a temporary solution has outlived its context, preventing the "sedimentation" of legacy code.
### 2. Main Actors, Decisions, and Constraints
#### **The Actors:**
* **The Engineer:** No longer a "wizard" or "firefighter." Their value shifts from *knowing where the bodies are buried* to *architectural creativity*.
* **The Manager:** Operates with high-fidelity data. They can no longer be "held hostage" by a single developer who is the only one who understands the legacy system.
* **The Organization:** Becomes a "Ship of Theseus" that can replace any part of itself without losing its soul or operational logic.
* **The Displaced "Accidental Landlord":** Individuals who previously gained job security and status through "gatekeeping" complexity find their social capital evaporated.
#### **Key Decisions:**
* **The "Pay Now or Pay Later" Mandate:** Because debt is visible, the decision to incur it is a formal business agreement, not a quiet engineering shortcut.
* **Radical Transparency:** Organizations must decide to prioritize documentation and "memory hygiene" over the raw speed of "shipping it."
#### **Constraints:**
* **Cognitive Load:** Even if memory is perfect, human bandwidth is not. The constraint shifts from *finding* information to *processing* the sheer volume of perfect history.
* **The "Rigidity Trap":** Perfect memory might make it harder to pivot if the organization feels "haunted" by its past decisions.
### 3. Potential Outcomes and Likelihood
* **Hyper-Fluidity (High Likelihood):** Employee turnover no longer causes "brain drain." A new hire can become as effective as a 10-year veteran in days because the "why" behind every system is instantly queryable.
* **The End of the "Legacy System" (Moderate Likelihood):** Systems are continuously refactored because the cost of doing so is known and the risks are mapped. We no longer see 40-year-old COBOL systems that "no one dares touch."
* **Shift in Power Dynamics (High Likelihood):** Power moves from **Knowledge Hoarders** (those who know the system) to **Synthesisers** (those who can use the system to create new value).
### 4. Risks, Opportunities, and Trade-offs
#### **Risks:**
* **The Panopticon Effect:** Perfect memory means every mistake is preserved forever. This could lead to "Analysis Paralysis" or a culture of extreme risk aversion.
* **Loss of "Productive Forgetting":** Sometimes, forgetting old constraints is how innovation happens. Perfect memory might tether an organization to obsolete paradigms.
#### **Opportunities:**
* **Massive Efficiency Gains:** Estimates suggest engineers spend 30-50% of their time just trying to understand existing code. Eliminating this "comprehension tax" would double global R&D output.
* **True Meritocracy:** Without "feral knowledge" to hide behind, performance is measured by actual contribution rather than proximity to critical, mysterious systems.
#### **Trade-offs:**
* **Speed vs. Legibility:** The initial "velocity" of a project might be slower because the "memory overhead" (documenting intent) is non-negotiable.
### 5. Short-term vs. Long-term Implications
* **Short-term:** A period of "The Great Unmasking." Many senior leaders and engineers whose value was tied to "knowing the mess" will be exposed as having few other skills. Organizational restructuring would be rampant.
* **Long-term:** The emergence of "Liquid Organizations." Companies could merge, split, and reorganize with the ease of software modules because their internal logic is perfectly transparent and modular.
### 6. Assumptions and Uncertainties
* **Assumption:** We assume that "Perfect Memory" is technologically and cognitively possible (perhaps via AI-mediated neural indexing).
* **Uncertainty:** How does the "Human Desire for Power" (a Control Factor) adapt? If you can't hoard knowledge, do people start hoarding "Compute" or "Social Influence" instead?
* **Uncertainty:** Does the removal of "Technical Debt" actually lead to better products, or does the friction of debt actually serve as a natural filter for which features are truly worth maintaining?
### 7. Causal Relationships: The "Anti-Landlord" Cycle
1. **Perfect Memory** $\rightarrow$ **Eliminates Information Asymmetry.**
2. **No Information Asymmetry** $\rightarrow$ **Technical Debt is a Choice, not a Secret.**
3. **Transparent Debt** $\rightarrow$ **Prevents "Feral Knowledge" (undocumented complexity).**
4. **No Feral Knowledge** $\rightarrow$ **No "Accidental Landlord" (power through gatekeeping).**
5. **No Accidental Landlord** $\rightarrow$ **Power is redistributed to those who provide the most current value, rather than those who have the longest tenure.**
### Final Insight
In this counterfactual, the **"Accidental Landlord"** is replaced by the **"Agile Architect."** The primary competitive advantage shifts from **Retention of the Past** to **Velocity of the Future.** However, the "Control Factor" of human nature suggests that new forms of exclusion would emerge—likely based on who controls the *algorithms* that filter the perfect memory, rather than the memory itself. The "Landlord" doesn't disappear; they just move from the "Basement" (Legacy Code) to the "Penthouse" (The Interface).
**Analysis:**
This analysis explores a counterfactual world where **Institutional Memory is perfect**, **Technical Debt is always transparent (never becoming "Feral Knowledge")**, and the **"Accidental Landlord"**—those who derive power from being the sole keepers of legacy complexity—never emerges.
---
### 1. Key Elements and Conditions
In this scenario, the fundamental "entropy" of information is halted. The following conditions exist:
* **Universal Context Preservation:** Every decision, hack, and "temporary fix" is recorded with its original intent, constraints, and expiration date.
* **Debt Legibility:** Technical debt is treated like a financial ledger. It is visible to all stakeholders, not just the engineers. It never "goes feral" (losing its documentation and becoming a mysterious black box).
* **The Death of Tribalism:** Knowledge does not reside in the heads of "the veterans" but in a shared, accessible, and perfectly indexed substrate.
* **Automated Auditing:** Systems automatically flag when a temporary solution has outlived its context, preventing the "sedimentation" of legacy code.
### 2. Main Actors, Decisions, and Constraints
#### **The Actors:**
* **The Engineer:** No longer a "wizard" or "firefighter." Their value shifts from *knowing where the bodies are buried* to *architectural creativity*.
* **The Manager:** Operates with high-fidelity data. They can no longer be "held hostage" by a single developer who is the only one who understands the legacy system.
* **The Organization:** Becomes a "Ship of Theseus" that can replace any part of itself without losing its soul or operational logic.
* **The Displaced "Accidental Landlord":** Individuals who previously gained job security and status through "gatekeeping" complexity find their social capital evaporated.
#### **Key Decisions:**
* **The "Pay Now or Pay Later" Mandate:** Because debt is visible, the decision to incur it is a formal business agreement, not a quiet engineering shortcut.
* **Radical Transparency:** Organizations must decide to prioritize documentation and "memory hygiene" over the raw speed of "shipping it."
#### **Constraints:**
* **Cognitive Load:** Even if memory is perfect, human bandwidth is not. The constraint shifts from *finding* information to *processing* the sheer volume of perfect history.
* **The "Rigidity Trap":** Perfect memory might make it harder to pivot if the organization feels "haunted" by its past decisions.
### 3. Potential Outcomes and Likelihood
* **Hyper-Fluidity (High Likelihood):** Employee turnover no longer causes "brain drain." A new hire can become as effective as a 10-year veteran in days because the "why" behind every system is instantly queryable.
* **The End of the "Legacy System" (Moderate Likelihood):** Systems are continuously refactored because the cost of doing so is known and the risks are mapped. We no longer see 40-year-old COBOL systems that "no one dares touch."
* **Shift in Power Dynamics (High Likelihood):** Power moves from **Knowledge Hoarders** (those who know the system) to **Synthesisers** (those who can use the system to create new value).
### 4. Risks, Opportunities, and Trade-offs
#### **Risks:**
* **The Panopticon Effect:** Perfect memory means every mistake is preserved forever. This could lead to "Analysis Paralysis" or a culture of extreme risk aversion.
* **Loss of "Productive Forgetting":** Sometimes, forgetting old constraints is how innovation happens. Perfect memory might tether an organization to obsolete paradigms.
#### **Opportunities:**
* **Massive Efficiency Gains:** Estimates suggest engineers spend 30-50% of their time just trying to understand existing code. Eliminating this "comprehension tax" would double global R&D output.
* **True Meritocracy:** Without "feral knowledge" to hide behind, performance is measured by actual contribution rather than proximity to critical, mysterious systems.
#### **Trade-offs:**
* **Speed vs. Legibility:** The initial "velocity" of a project might be slower because the "memory overhead" (documenting intent) is non-negotiable.
### 5. Short-term vs. Long-term Implications
* **Short-term:** A period of "The Great Unmasking." Many senior leaders and engineers whose value was tied to "knowing the mess" will be exposed as having few other skills. Organizational restructuring would be rampant.
* **Long-term:** The emergence of "Liquid Organizations." Companies could merge, split, and reorganize with the ease of software modules because their internal logic is perfectly transparent and modular.
### 6. Assumptions and Uncertainties
* **Assumption:** We assume that "Perfect Memory" is technologically and cognitively possible (perhaps via AI-mediated neural indexing).
* **Uncertainty:** How does the "Human Desire for Power" (a Control Factor) adapt? If you can't hoard knowledge, do people start hoarding "Compute" or "Social Influence" instead?
* **Uncertainty:** Does the removal of "Technical Debt" actually lead to better products, or does the friction of debt actually serve as a natural filter for which features are truly worth maintaining?
### 7. Causal Relationships: The "Anti-Landlord" Cycle
1. **Perfect Memory** $\rightarrow$ **Eliminates Information Asymmetry.**
2. **No Information Asymmetry** $\rightarrow$ **Technical Debt is a Choice, not a Secret.**
3. **Transparent Debt** $\rightarrow$ **Prevents "Feral Knowledge" (undocumented complexity).**
4. **No Feral Knowledge** $\rightarrow$ **No "Accidental Landlord" (power through gatekeeping).**
5. **No Accidental Landlord** $\rightarrow$ **Power is redistributed to those who provide the most current value, rather than those who have the longest tenure.**
### Final Insight
In this counterfactual, the **"Accidental Landlord"** is replaced by the **"Agile Architect."** The primary competitive advantage shifts from **Retention of the Past** to **Velocity of the Future.** However, the "Control Factor" of human nature suggests that new forms of exclusion would emerge—likely based on who controls the *algorithms* that filter the perfect memory, rather than the memory itself. The "Landlord" doesn't disappear; they just move from the "Basement" (Legacy Code) to the "Penthouse" (The Interface).
## Counterfactual Scenario 4
**Scenario:** What if 'Mythic Secrecy' (the foundational lie) was structurally impossible due to a decentralized, immutable 'Ground Truth' verification system available to all citizens since the medieval era?
Prompt for Counterfactual 4
Analyze the following scenario in detail:
Scenario: Counterfactual 4
What if ‘Mythic Secrecy’ (the foundational lie) was structurally impossible due to a decentralized, immutable ‘Ground Truth’ verification system available to all citizens since the medieval era?
Context from Related Files:
counterfactual_op.md
1
2
3
4
5
6
7
8
9
---
transforms: (.+)/content\.md -> $1/counterfactual.md
task_type: CounterfactualAnalysis
---
* Analyze the content through counterfactual reasoning
* Identify key decisions, events, or assumptions and explore alternative outcomes
* Use "what if" scenarios to stress-test claims and reveal hidden dependencies
* Highlight which counterfactuals most significantly change the conclusions
Previous Task Results:
Control Factors:
- Human desire for power and exclusion
- Economic incentives for competitive advantage
- The existence of complex social and technological structures
Instructions:
- Describe the key elements and conditions of this scenario
- Identify the main actors, decisions, and constraints
- Analyze potential outcomes and their likelihood
- Identify risks, opportunities, and trade-offs
- Consider both short-term and long-term implications
- Highlight any assumptions or uncertainties
- Provide insights on causal relationships
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
Response for Counterfactual 4
This analysis explores a world where the "Foundational Lie"—the strategic use of secrecy, myth-making, and information asymmetry to maintain power—is rendered impossible by a decentralized, immutable "Ground Truth" system established in the medieval era.
---
### 1. Key Elements and Conditions
The core of this scenario is the **"Universal Ledger of Reality."** Imagine a system (whether based on precursor technology, a unique physical law, or a pervasive "magical" field) that functions as a decentralized, public record of events, transactions, and lineages.
* **Immutability:** Once an event is recorded (e.g., a king’s decree, a murder, a debt), it cannot be erased or altered by any authority.
* **Decentralization:** No single church, state, or guild controls the "nodes" of this truth. Access is a birthright, perhaps through "Truth Stones" in every village square or a mental interface.
* **The Death of Mythic Secrecy:** The "Foundational Lie"—the idea that leaders possess divine blood, secret knowledge, or a mandate from a hidden god—cannot survive. If a King claims divine right, but the Ledger shows his grandfather was a common thief who murdered the previous lord, the myth collapses instantly.
### 2. Main Actors, Decisions, and Constraints
* **The Nobility/Elite:**
* *Decision:* They cannot rule through "prestige" or "divine mystery." They must pivot to **Rule by Utility.**
* *Constraint:* They are subject to the same transparency as peasants. Corruption is visible in real-time.
* **The Clergy/Ideologues:**
* *Decision:* Religion must shift from "Faith in the Unseen" to "Ethics of the Seen."
* *Constraint:* Dogma that contradicts the Ground Truth is discarded. The Church becomes a judicial body rather than a mystical one.
* **The Peasantry/Citizens:**
* *Decision:* With the "Foundational Lie" gone, the psychological barrier to revolt is lowered. They must decide how to organize without traditional hierarchies.
* *Constraint:* While they have truth, they may still lack physical resources (land, weapons).
* **The "Truth-Keepers" (System Maintainers):**
* *Decision:* A new class emerges to interpret the massive influx of data.
* *Constraint:* They are the most dangerous actors, as they might attempt to "contextualize" truth to regain the power of the lie.
### 3. Potential Outcomes and Likelihood
* **The "Glass Feudalism" (High Likelihood):** Hierarchies persist but are based on verified merit or brutal, transparent force. If a lord provides protection, the contract is explicit and verified. There is no "noblesse oblige," only "noblesse contract."
* **Accelerated Scientific Revolution (High Likelihood):** Because "Ground Truth" prevents the suppression of heretical facts, the Dark Ages never happen in an intellectual sense. Empirical observation is the only currency.
* **The Radicalization of Interpretation (Medium Likelihood):** Since the *facts* are indisputable, conflict shifts entirely to *interpretation*. "Yes, the King killed that man (Fact), but it was for the greater good (Interpretation)." Politics becomes a war of philosophy rather than a war of secrets.
* **Social Stagnation (Low Likelihood):** Some argue that "polite lies" are the grease of civilization. Total transparency might lead to constant vendettas and social friction, potentially collapsing society into small, hyper-defensive units.
### 4. Risks, Opportunities, and Trade-offs
* **Risk: The Tyranny of the Record.** In a world where no one can "start over," a single youthful mistake is etched into the Ground Truth forever. There is no "right to be forgotten."
* **Opportunity: Hyper-Efficient Markets.** Economic friction vanishes. Credit is based on verified history; fraud is structurally impossible. This could lead to a medieval industrial revolution.
* **Trade-off: Privacy vs. Accountability.** To have a "Ground Truth" that prevents the Foundational Lie, one must sacrifice the "Private Lie." Personal privacy becomes a luxury or a relic.
### 5. Short-term vs. Long-term Implications
* **Short-term (1100s–1300s):** Massive instability. The collapse of the Papacy and traditional Monarchies. A century of "Truth Wars" as the old guard tries to destroy the system.
* **Long-term (1400s–Present):** The emergence of a "Glass Civilization." Governance is likely algorithmic or hyper-parliamentary. The concept of "conspiracy" is non-existent. Humanity reaches a high-tech state much earlier, but perhaps with a colder, more clinical social structure.
### 6. Assumptions and Uncertainties
* **Assumption of Literacy/Access:** This scenario assumes that "Ground Truth" is legible to the average person. If only an elite can read the "Ledger," the Foundational Lie simply migrates to the interpretation of the Ledger.
* **The Violence Gap:** Truth does not equal power. A tyrant can be a *verified* tyrant. If he owns the grain and the swords, knowing he is a usurper doesn't necessarily empower the people to stop him.
* **Human Psychology:** Can humans live without myths? We are wired for narrative. If the "Foundational Lie" is removed, will humans simply invent "Secondary Myths" that ignore the Ground Truth?
### 7. Causal Insights: The Role of the Lie
This counterfactual reveals that **Mythic Secrecy is the "social glue" of traditional centralization.**
1. **Secrecy as a Scaling Tool:** In our history, secrecy allowed leaders to project an image of competence and divinity that scaled beyond their actual abilities. Without it, organizations must remain smaller or become significantly more efficient.
2. **The Shift from "Who" to "What":** In a Ground Truth world, authority shifts from the *Identity* of the ruler (The King) to the *Action* of the ruler (The Policy).
3. **The Fragility of Truth:** The scenario suggests that the "Foundational Lie" is not just a tool of oppression, but a protective layer for social complexity. Removing it requires a massive leap in human cognitive and emotional maturity to prevent the "Truth" from becoming a weapon of universal surveillance and social freezing.
**Conclusion:** A world without the Foundational Lie is a world without "Magic" (in the metaphorical sense). It is a world of cold, hard accounting. While it prevents the horrors of systemic deception and hidden corruption, it risks creating a society of rigid, unforgiving transparency where the human capacity for reinvention is stifled by an immutable past.
**Analysis:**
This analysis explores a world where the "Foundational Lie"—the strategic use of secrecy, myth-making, and information asymmetry to maintain power—is rendered impossible by a decentralized, immutable "Ground Truth" system established in the medieval era.
---
### 1. Key Elements and Conditions
The core of this scenario is the **"Universal Ledger of Reality."** Imagine a system (whether based on precursor technology, a unique physical law, or a pervasive "magical" field) that functions as a decentralized, public record of events, transactions, and lineages.
* **Immutability:** Once an event is recorded (e.g., a king’s decree, a murder, a debt), it cannot be erased or altered by any authority.
* **Decentralization:** No single church, state, or guild controls the "nodes" of this truth. Access is a birthright, perhaps through "Truth Stones" in every village square or a mental interface.
* **The Death of Mythic Secrecy:** The "Foundational Lie"—the idea that leaders possess divine blood, secret knowledge, or a mandate from a hidden god—cannot survive. If a King claims divine right, but the Ledger shows his grandfather was a common thief who murdered the previous lord, the myth collapses instantly.
### 2. Main Actors, Decisions, and Constraints
* **The Nobility/Elite:**
* *Decision:* They cannot rule through "prestige" or "divine mystery." They must pivot to **Rule by Utility.**
* *Constraint:* They are subject to the same transparency as peasants. Corruption is visible in real-time.
* **The Clergy/Ideologues:**
* *Decision:* Religion must shift from "Faith in the Unseen" to "Ethics of the Seen."
* *Constraint:* Dogma that contradicts the Ground Truth is discarded. The Church becomes a judicial body rather than a mystical one.
* **The Peasantry/Citizens:**
* *Decision:* With the "Foundational Lie" gone, the psychological barrier to revolt is lowered. They must decide how to organize without traditional hierarchies.
* *Constraint:* While they have truth, they may still lack physical resources (land, weapons).
* **The "Truth-Keepers" (System Maintainers):**
* *Decision:* A new class emerges to interpret the massive influx of data.
* *Constraint:* They are the most dangerous actors, as they might attempt to "contextualize" truth to regain the power of the lie.
### 3. Potential Outcomes and Likelihood
* **The "Glass Feudalism" (High Likelihood):** Hierarchies persist but are based on verified merit or brutal, transparent force. If a lord provides protection, the contract is explicit and verified. There is no "noblesse oblige," only "noblesse contract."
* **Accelerated Scientific Revolution (High Likelihood):** Because "Ground Truth" prevents the suppression of heretical facts, the Dark Ages never happen in an intellectual sense. Empirical observation is the only currency.
* **The Radicalization of Interpretation (Medium Likelihood):** Since the *facts* are indisputable, conflict shifts entirely to *interpretation*. "Yes, the King killed that man (Fact), but it was for the greater good (Interpretation)." Politics becomes a war of philosophy rather than a war of secrets.
* **Social Stagnation (Low Likelihood):** Some argue that "polite lies" are the grease of civilization. Total transparency might lead to constant vendettas and social friction, potentially collapsing society into small, hyper-defensive units.
### 4. Risks, Opportunities, and Trade-offs
* **Risk: The Tyranny of the Record.** In a world where no one can "start over," a single youthful mistake is etched into the Ground Truth forever. There is no "right to be forgotten."
* **Opportunity: Hyper-Efficient Markets.** Economic friction vanishes. Credit is based on verified history; fraud is structurally impossible. This could lead to a medieval industrial revolution.
* **Trade-off: Privacy vs. Accountability.** To have a "Ground Truth" that prevents the Foundational Lie, one must sacrifice the "Private Lie." Personal privacy becomes a luxury or a relic.
### 5. Short-term vs. Long-term Implications
* **Short-term (1100s–1300s):** Massive instability. The collapse of the Papacy and traditional Monarchies. A century of "Truth Wars" as the old guard tries to destroy the system.
* **Long-term (1400s–Present):** The emergence of a "Glass Civilization." Governance is likely algorithmic or hyper-parliamentary. The concept of "conspiracy" is non-existent. Humanity reaches a high-tech state much earlier, but perhaps with a colder, more clinical social structure.
### 6. Assumptions and Uncertainties
* **Assumption of Literacy/Access:** This scenario assumes that "Ground Truth" is legible to the average person. If only an elite can read the "Ledger," the Foundational Lie simply migrates to the interpretation of the Ledger.
* **The Violence Gap:** Truth does not equal power. A tyrant can be a *verified* tyrant. If he owns the grain and the swords, knowing he is a usurper doesn't necessarily empower the people to stop him.
* **Human Psychology:** Can humans live without myths? We are wired for narrative. If the "Foundational Lie" is removed, will humans simply invent "Secondary Myths" that ignore the Ground Truth?
### 7. Causal Insights: The Role of the Lie
This counterfactual reveals that **Mythic Secrecy is the "social glue" of traditional centralization.**
1. **Secrecy as a Scaling Tool:** In our history, secrecy allowed leaders to project an image of competence and divinity that scaled beyond their actual abilities. Without it, organizations must remain smaller or become significantly more efficient.
2. **The Shift from "Who" to "What":** In a Ground Truth world, authority shifts from the *Identity* of the ruler (The King) to the *Action* of the ruler (The Policy).
3. **The Fragility of Truth:** The scenario suggests that the "Foundational Lie" is not just a tool of oppression, but a protective layer for social complexity. Removing it requires a massive leap in human cognitive and emotional maturity to prevent the "Truth" from becoming a weapon of universal surveillance and social freezing.
**Conclusion:** A world without the Foundational Lie is a world without "Magic" (in the metaphorical sense). It is a world of cold, hard accounting. While it prevents the horrors of systemic deception and hidden corruption, it risks creating a society of rigid, unforgiving transparency where the human capacity for reinvention is stifled by an immutable past.
## Comparative Analysis
Comparison Prompt
Compare the following scenarios and provide insights on their differences:
Actual Scenario
Description: Secret knowledge functions as the primordial form of property, evolving from deliberate esoteric guilds to emergent ‘feral’ knowledge (technical debt) and finally to operational opacity in AI systems, where power is derived from navigating incomprehensible complexity. Analysis: This analysis explores the evolution of secret knowledge as a form of property, tracing its trajectory from intentional human exclusion to the emergent, non-human complexity of modern AI systems.
1. Key Elements and Conditions
The scenario rests on the premise that information asymmetry is the foundation of value.
- Knowledge as Property: Unlike physical property, knowledge is non-rivalrous but can be made “excludable” through secrecy. This creates a “Knowledge Monopoly.”
- The Three-Stage Evolution:
- Esoteric Guilds (Deliberate): Human-to-human secrecy (e.g., trade secrets, alchemy, priesthoods).
- Feral Knowledge (Technical Debt): Knowledge that “escapes” human documentation. It is the “ghost in the machine” of legacy code—unintended complexity that requires specialized “shamanic” intervention to maintain.
- Operational Opacity (AI): Knowledge generated by non-human heuristics. The “secret” is no longer a hidden formula but a multi-dimensional weight map that no human mind can hold.
- The Complexity Premium: Power is no longer held by those who own the tools, but by those who can navigate the incomprehensible state-space of those tools.
2. Main Actors, Decisions, and Constraints
- The Gatekeepers (Historical): Guild masters and corporations who decide what is “Proprietary.” Their constraint is the “leaky” nature of human secrets (espionage, defection).
- The Maintainers (Transitional): Software engineers and systems architects dealing with “feral” systems. Their decision is often a trade-off: Speed of deployment vs. Legibility. Choosing speed creates technical debt, which functions as a barrier to entry for competitors.
- The Navigators (Modern/Future): AI researchers and “Prompt Engineers” who do not understand the why of a system but have developed an intuitive “feel” for the how.
- Constraints:
- Cognitive Load: The human brain cannot scale with the complexity of feral or AI knowledge.
- Entropy: As systems grow, the “secret” part (the part no one understands) naturally increases.
3. Potential Outcomes and Likelihood
- The “Techno-Priesthood” (High Likelihood): A small class of individuals who possess the “knack” for navigating opaque systems becomes indispensable. They do not use logic; they use ritualized interaction with the AI/System.
- Systemic Fragility (Medium Likelihood): As knowledge becomes “feral,” the loss of a few key “Navigators” could lead to the collapse of critical infrastructure that no one knows how to rebuild from scratch.
- The End of “Open Source” Utility (Low Likelihood): Even if code is open, if the complexity is high enough, the “openness” is an illusion. The “secret” is the emergent behavior, not the source code.
4. Risks, Opportunities, and Trade-offs
- Risk: The “Black Box” Trap. We become dependent on systems (economic, medical, judicial) whose decision-making logic is a “secret” even to its creators. This leads to accountability vacuums.
- Opportunity: Hyper-Efficiency. Opaque AI systems can find patterns humans would never see. By abandoning the need for “understanding,” we unlock performance levels previously thought impossible.
- Trade-off: Legibility vs. Capability. To make a system understandable (legible) is to limit its complexity. To maximize capability is to embrace opacity.
5. Short-term and Long-term Implications
- Short-term: Companies will continue to prioritize “shipping” over “documenting,” accelerating the growth of feral knowledge (technical debt) as a competitive moat.
- Long-term: A fundamental shift in the definition of “Expertise.” Expertise will move from Analytical (breaking things down) to Relational (knowing how to coax a result out of a complex system).
6. Assumptions and Uncertainties
- Assumption: That complexity will continue to outpace human cognitive evolution.
- Uncertainty: Explainable AI (XAI). If we develop tools that can perfectly translate AI “thought” into human logic, the “Operational Opacity” stage may be bypassed or reversed.
- Uncertainty: Regulatory Intervention. Will governments mandate “Right to Understand” laws, forcing systems to remain simple enough for human audit?
7. Causal Relationships: The “Complexity Trap”
The scenario reveals a feedback loop:
- Competition drives the need for Advantage.
- Advantage is found in Complexity (which is harder to copy).
- Complexity leads to Opacity (Feral/AI knowledge).
- Opacity creates a New Property Class (those who can navigate the opacity).
- This class protects their status by Increasing Complexity, restarting the cycle.
8. Counterfactual Analysis (Stress-Testing)
Using the counterfactual_op.md framework, we can test the stability of this scenario:
- What if “Feral Knowledge” (Technical Debt) was eliminated by automated refactoring?
- Result: The transition to AI Opacity would be even more jarring. We would move from “Perfectly Legible” systems to “Completely Opaque” AI without the intermediate step of “messy” human systems. The “Techno-Priesthood” would emerge as a sudden disruption rather than a gradual evolution.
- What if the “Human Desire for Power” was replaced by a “Radical Transparency” incentive?
- Result: If economic rewards favored simplicity over performance, we would see a “Complexity Ceiling.” Innovation would slow down, but systems would be incredibly robust and democratic. Power would shift back to those with the best logic, not the best intuition.
- What if AI systems become “Self-Explaining”?
- Result: This destroys the “Secret Knowledge” property. If the AI can tell anyone how it works, the “Navigator” class loses its monopoly. Knowledge property would revert to its primordial form: Compute Power and Data Ownership.
Final Insight
The evolution of secret knowledge suggests that we are moving from an era of “Knowledge as Content” to “Knowledge as Navigation.” In the guild era, the secret was a recipe. In the AI era, the secret is the map of a shifting labyrinth. Power belongs to the one who doesn’t get lost.
Counterfactual 1
Scenario: What if ‘Structural Secrecy’ was impossible because all complex systems (AI, financial algorithms) were required by physical law or design to be perfectly human-interpretable? Analysis: This analysis explores a counterfactual world where Structural Secrecy—the phenomenon where the complexity of a system inherently obscures its inner workings—is non-existent. In this world, every deep neural network, high-frequency trading algorithm, and bureaucratic hierarchy is as transparent and understandable as a simple mechanical lever.
1. Key Elements and Conditions
- The Interpretability Mandate: Whether by physical law (a universe where complexity requires legibility) or a foundational design protocol, no system can function unless its logic is “human-readable.”
- The End of the “Black Box”: The concept of emergent behavior that cannot be traced back to specific, understandable inputs and weights is gone.
- Cognitive Parity: For this to work, either human cognitive capacity has expanded to meet the complexity of the world, or (more likely) the complexity of technology is capped at the threshold of human comprehension.
- Universal Auditability: Every decision made by a machine or a large organization carries an “epistemic trail” that any observer can follow to understand why a decision was made.
2. Main Actors, Decisions, and Constraints
- AI Researchers/Engineers: They no longer “train” models and hope for the best. They must “author” logic. The decision-space shifts from optimization (finding what works) to architecture (building what can be explained).
- Corporations: The primary constraint is the loss of “Proprietary Complexity.” Companies can no longer hide predatory pricing or biased hiring behind “the algorithm.”
- Regulators: Their role shifts from forensic investigation to real-time monitoring. They don’t need to subpoena code; they simply look at the system.
- The Individual: Citizens gain “Epistemic Agency.” They are no longer subjects of opaque systems but can interrogate the logic of their credit scores, medical diagnoses, and social feeds.
3. Potential Outcomes and Likelihood
A. The “Complexity Ceiling” (High Likelihood)
If every system must be interpretable, we likely hit a wall in technological advancement. Modern AI (LLMs, protein folding) relies on high-dimensional patterns that the human brain cannot naturally process.
- Outcome: We might lose the most powerful “miracles” of AI in exchange for total control. Progress becomes slower, more incremental, and strictly logical.
B. The Death of Algorithmic Rent-Seeking (High Likelihood)
Financial markets currently thrive on “structural secrecy” (e.g., dark pools, HFT).
- Outcome: If every trade’s logic is transparent, “alpha” (market-beating edge) based on obfuscation disappears. Markets become more stable but perhaps less liquid, as the incentive to “out-smart” the system via complexity vanishes.
C. Radical Political Accountability (Medium Likelihood)
Bureaucracies often use complexity to hide responsibility (the “no one’s fault” defense).
- Outcome: In a world of perfect interpretability, the “paper trail” is a “logic trail.” Corruption becomes nearly impossible to hide because the intent behind a policy shift is visible in the system’s design.
4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity |
|---|---|---|
| Security | The “Glass House” Vulnerability: If a system is perfectly interpretable to a user, it is perfectly interpretable to a hacker. Finding exploits becomes trivial. | Perfect Verification: We can prove a system is safe before turning it on. |
| Innovation | The Interpretability Tax: Massive amounts of energy/compute are wasted making things “simple” for humans rather than “efficient” for the task. | Democratization: Anyone can understand and modify technology, ending the priesthood of high-tech elites. |
| Social | The End of Privacy: If “complex systems” include the human brain (via BCI), our inner thoughts become “structurally transparent” to others. | Total Trust: Social friction decreases because “hidden agendas” are structurally impossible to maintain. |
5. Short-term and Long-term Implications
Short-term:
- Economic Chaos: The valuation of tech giants collapses as their “black box” advantages are neutralized.
- Scientific Pivot: A massive shift from “Discovery by Observation” (watching what the AI finds) to “Discovery by Construction” (building only what we understand).
Long-term:
- A “Human-Centric” Civilization: Technology stops being an alien force acting upon us and becomes a literal extension of human intent.
- Stagnation vs. Stability: We may live in a “slower” world, but one free from systemic collapses (like the 2008 financial crisis) caused by misunderstood complexity.
6. Assumptions and Uncertainties
- The Definition of “Human”: Does “human-interpretable” mean interpretable by an average person, or a specialist? If it’s the latter, structural secrecy might just migrate from the system to the expert class.
- The Nature of Intelligence: This scenario assumes that “intelligence” can exist without “unfathomable complexity.” If true intelligence requires high-dimensional opacity, then this counterfactual describes a world where AGI is impossible.
- The Adversarial Response: If structural secrecy is impossible, will humans invent new forms of linguistic or social secrecy to maintain power?
7. Causal Relationships: The “Transparency Loop”
In our current world, Complexity → Secrecy → Power Concentration → More Complexity. In the counterfactual world, the loop is broken:
- Requirement of Interpretability → Limits the scale of autonomous systems.
- Limited Scale → Increases human oversight.
- Increased Oversight → Reduces the “Power Gap” between those who own the systems and those who use them.
- Reduced Power Gap → Leads to a more egalitarian, albeit potentially less “advanced,” society.
Final Insight
The removal of Structural Secrecy acts as a “Complexity Tax” on Power. In our world, power is often gained by mastering or owning what others cannot understand. If understanding is a prerequisite for existence, power becomes a function of persuasion and clarity rather than obfuscation and scale. The world becomes safer and more just, but it may lose the “emergent magic” that allows systems to solve problems beyond the reach of the individual human mind.
Counterfactual 2
Scenario: What if the ‘Ur-property’ of secrecy was abolished by a ‘Radical Transparency’ technology (e.g., universal telepathy or perfect surveillance) that made withholding information impossible? Analysis: This analysis explores a world where the “Ur-property” of secrecy—the foundational ability to withhold information—is eliminated by Radical Transparency (RT). Whether through biological telepathy or an inescapable technological surveillance layer, the “private room” of the human mind and the “black box” of organizational strategy have been forcibly opened.
1. Key Elements and Conditions
- The End of Information Asymmetry: The fundamental driver of markets, negotiations, and social hierarchies—knowing something someone else doesn’t—evaporates.
- The Death of the “Inner Sanctum”: The distinction between public persona and private thought vanishes.
- Involuntary Veracity: Truth is no longer a moral choice but a structural necessity. Lying becomes impossible because the “signal” of the truth is always available to the observer.
- Universal Access: For this scenario to be “Radical,” the transparency must be bidirectional (the governed see the governors) or universal (everyone sees everyone).
2. Main Actors, Decisions, and Constraints
- Individuals: Must decide how to process the “noise” of everyone else’s thoughts/data. The constraint is psychological bandwidth and the trauma of losing the ego’s protective shell.
- States/Governments: Lose the ability to conduct “black ops,” secret diplomacy, or classified research. The constraint is the sudden obsolescence of national security frameworks.
- Corporations: Lose Intellectual Property (IP), trade secrets, and “first-mover” advantages based on hidden R&D.
- The “Architects” (if technological): Those who maintain the RT infrastructure. They face the ultimate “Who watches the watchers?” dilemma, unless the technology is decentralized/biological.
3. Potential Outcomes and Likelihood
A. The Great Social Collapse (High Likelihood - Short Term)
Social cohesion relies heavily on “pro-social lying” and tact. If every fleeting thought of resentment, lust, or judgment is public, existing social structures (marriages, friendships, workplace hierarchies) would likely shatter instantly.
- Outcome: Mass isolation or violent conflict as people react to the “unfiltered” reality of others.
B. The Hive-Mind Evolution (Medium Likelihood - Long Term)
To survive the psychological onslaught, humanity might evolve a “collective consciousness.” If you can feel everyone’s pain and see their justifications, empathy might scale to a point where “the other” ceases to exist.
- Outcome: A post-conflict society where resource allocation is optimized for the whole, but individual agency is diminished.
C. The Meritocracy of Execution (High Likelihood - Economic)
Since no one can hide a “better mousetrap” design, competition shifts from innovation-hoarding to execution-speed.
- Outcome: Rapid technological acceleration. If a cure for cancer is thought of by one person, the world has it instantly. Economic value shifts from “owning the idea” to “owning the physical infrastructure to build it.”
4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity | Trade-off |
|---|---|---|---|
| Governance | Totalitarian “Thought Police” (if centralized). | Total elimination of corruption and graft. | Security vs. Autonomy. |
| Innovation | No incentive to invest in R&D if it’s instantly stolen. | Global “Open Source” everything; no redundant research. | Profit vs. Progress. |
| Psychology | Mass psychosis, loss of “self,” chronic vulnerability. | Radical empathy; end of loneliness and misunderstanding. | Privacy vs. Connection. |
5. Short-term vs. Long-term Implications
- Short-term (0-5 years): The “Transparency Shock.” Economic markets crash as insider information becomes “just information.” Political regimes fall as citizens see the true intentions of leaders. High rates of psychological trauma.
- Long-term (50+ years): The “New Equilibrium.” A new language of “Radical Honesty” develops. Humans become “radically boring” or “radically accepting.” The concept of “shame” likely disappears, as shame requires a secret to fester.
6. Assumptions and Uncertainties
- Assumption of Bandwidth: Can the human brain actually process universal transparency? Or would we simply “tune out” 99% of the data, effectively recreating secrecy through sheer noise?
- Uncertainty of Power: Does transparency actually disempower the powerful? History suggests that even when we know leaders are corrupt, power dynamics often persist through force rather than deception.
- The “Motive” Gap: Knowing what someone is thinking doesn’t always explain why. Misinterpretation of transparent data could lead to new forms of conflict.
7. Causal Relationships: The “Ur-Property” Chain
- Secrecy $\rightarrow$ Identity: By removing secrecy, you break the boundary of the “Self.” If there is no part of me that is only mine, the “I” becomes “We.”
- Secrecy $\rightarrow$ Value: Scarcity of information creates value. Radical transparency creates “Information Hyper-inflation,” where data is infinite and free, potentially collapsing all information-based economies.
- Secrecy $\rightarrow$ Strategy: Strategy is the art of the hidden move. Without it, “strategy” becomes “optimization.” You don’t outmaneuver an opponent; you simply out-compute them in a race of pure efficiency.
Final Insight
The abolition of secrecy is the abolition of the Strategic Actor. In a world of Radical Transparency, the “Game” (as defined by Game Theory) changes from a Non-Cooperative Game with Imperfect Information to a Cooperative Game with Perfect Information. While this might end war and corruption, it likely ends the “Individual” as understood in Western liberal tradition, replacing it with a biological or digital collective. The cost of total truth is the loss of the private self.
Counterfactual 3
Scenario: What if institutional memory was perfect and ‘Technical Debt’ never became ‘Feral Knowledge,’ preventing the rise of the ‘Accidental Landlord’? Analysis: This analysis explores a counterfactual world where Institutional Memory is perfect, Technical Debt is always transparent (never becoming “Feral Knowledge”), and the “Accidental Landlord”—those who derive power from being the sole keepers of legacy complexity—never emerges.
1. Key Elements and Conditions
In this scenario, the fundamental “entropy” of information is halted. The following conditions exist:
- Universal Context Preservation: Every decision, hack, and “temporary fix” is recorded with its original intent, constraints, and expiration date.
- Debt Legibility: Technical debt is treated like a financial ledger. It is visible to all stakeholders, not just the engineers. It never “goes feral” (losing its documentation and becoming a mysterious black box).
- The Death of Tribalism: Knowledge does not reside in the heads of “the veterans” but in a shared, accessible, and perfectly indexed substrate.
- Automated Auditing: Systems automatically flag when a temporary solution has outlived its context, preventing the “sedimentation” of legacy code.
2. Main Actors, Decisions, and Constraints
The Actors:
- The Engineer: No longer a “wizard” or “firefighter.” Their value shifts from knowing where the bodies are buried to architectural creativity.
- The Manager: Operates with high-fidelity data. They can no longer be “held hostage” by a single developer who is the only one who understands the legacy system.
- The Organization: Becomes a “Ship of Theseus” that can replace any part of itself without losing its soul or operational logic.
- The Displaced “Accidental Landlord”: Individuals who previously gained job security and status through “gatekeeping” complexity find their social capital evaporated.
Key Decisions:
- The “Pay Now or Pay Later” Mandate: Because debt is visible, the decision to incur it is a formal business agreement, not a quiet engineering shortcut.
- Radical Transparency: Organizations must decide to prioritize documentation and “memory hygiene” over the raw speed of “shipping it.”
Constraints:
- Cognitive Load: Even if memory is perfect, human bandwidth is not. The constraint shifts from finding information to processing the sheer volume of perfect history.
- The “Rigidity Trap”: Perfect memory might make it harder to pivot if the organization feels “haunted” by its past decisions.
3. Potential Outcomes and Likelihood
- Hyper-Fluidity (High Likelihood): Employee turnover no longer causes “brain drain.” A new hire can become as effective as a 10-year veteran in days because the “why” behind every system is instantly queryable.
- The End of the “Legacy System” (Moderate Likelihood): Systems are continuously refactored because the cost of doing so is known and the risks are mapped. We no longer see 40-year-old COBOL systems that “no one dares touch.”
- Shift in Power Dynamics (High Likelihood): Power moves from Knowledge Hoarders (those who know the system) to Synthesisers (those who can use the system to create new value).
4. Risks, Opportunities, and Trade-offs
Risks:
- The Panopticon Effect: Perfect memory means every mistake is preserved forever. This could lead to “Analysis Paralysis” or a culture of extreme risk aversion.
- Loss of “Productive Forgetting”: Sometimes, forgetting old constraints is how innovation happens. Perfect memory might tether an organization to obsolete paradigms.
Opportunities:
- Massive Efficiency Gains: Estimates suggest engineers spend 30-50% of their time just trying to understand existing code. Eliminating this “comprehension tax” would double global R&D output.
- True Meritocracy: Without “feral knowledge” to hide behind, performance is measured by actual contribution rather than proximity to critical, mysterious systems.
Trade-offs:
- Speed vs. Legibility: The initial “velocity” of a project might be slower because the “memory overhead” (documenting intent) is non-negotiable.
5. Short-term vs. Long-term Implications
- Short-term: A period of “The Great Unmasking.” Many senior leaders and engineers whose value was tied to “knowing the mess” will be exposed as having few other skills. Organizational restructuring would be rampant.
- Long-term: The emergence of “Liquid Organizations.” Companies could merge, split, and reorganize with the ease of software modules because their internal logic is perfectly transparent and modular.
6. Assumptions and Uncertainties
- Assumption: We assume that “Perfect Memory” is technologically and cognitively possible (perhaps via AI-mediated neural indexing).
- Uncertainty: How does the “Human Desire for Power” (a Control Factor) adapt? If you can’t hoard knowledge, do people start hoarding “Compute” or “Social Influence” instead?
- Uncertainty: Does the removal of “Technical Debt” actually lead to better products, or does the friction of debt actually serve as a natural filter for which features are truly worth maintaining?
7. Causal Relationships: The “Anti-Landlord” Cycle
- Perfect Memory $\rightarrow$ Eliminates Information Asymmetry.
- No Information Asymmetry $\rightarrow$ Technical Debt is a Choice, not a Secret.
- Transparent Debt $\rightarrow$ Prevents “Feral Knowledge” (undocumented complexity).
- No Feral Knowledge $\rightarrow$ No “Accidental Landlord” (power through gatekeeping).
- No Accidental Landlord $\rightarrow$ Power is redistributed to those who provide the most current value, rather than those who have the longest tenure.
Final Insight
In this counterfactual, the “Accidental Landlord” is replaced by the “Agile Architect.” The primary competitive advantage shifts from Retention of the Past to Velocity of the Future. However, the “Control Factor” of human nature suggests that new forms of exclusion would emerge—likely based on who controls the algorithms that filter the perfect memory, rather than the memory itself. The “Landlord” doesn’t disappear; they just move from the “Basement” (Legacy Code) to the “Penthouse” (The Interface).
Counterfactual 4
Scenario: What if ‘Mythic Secrecy’ (the foundational lie) was structurally impossible due to a decentralized, immutable ‘Ground Truth’ verification system available to all citizens since the medieval era? Analysis: This analysis explores a world where the “Foundational Lie”—the strategic use of secrecy, myth-making, and information asymmetry to maintain power—is rendered impossible by a decentralized, immutable “Ground Truth” system established in the medieval era.
1. Key Elements and Conditions
The core of this scenario is the “Universal Ledger of Reality.” Imagine a system (whether based on precursor technology, a unique physical law, or a pervasive “magical” field) that functions as a decentralized, public record of events, transactions, and lineages.
- Immutability: Once an event is recorded (e.g., a king’s decree, a murder, a debt), it cannot be erased or altered by any authority.
- Decentralization: No single church, state, or guild controls the “nodes” of this truth. Access is a birthright, perhaps through “Truth Stones” in every village square or a mental interface.
- The Death of Mythic Secrecy: The “Foundational Lie”—the idea that leaders possess divine blood, secret knowledge, or a mandate from a hidden god—cannot survive. If a King claims divine right, but the Ledger shows his grandfather was a common thief who murdered the previous lord, the myth collapses instantly.
2. Main Actors, Decisions, and Constraints
- The Nobility/Elite:
- Decision: They cannot rule through “prestige” or “divine mystery.” They must pivot to Rule by Utility.
- Constraint: They are subject to the same transparency as peasants. Corruption is visible in real-time.
- The Clergy/Ideologues:
- Decision: Religion must shift from “Faith in the Unseen” to “Ethics of the Seen.”
- Constraint: Dogma that contradicts the Ground Truth is discarded. The Church becomes a judicial body rather than a mystical one.
- The Peasantry/Citizens:
- Decision: With the “Foundational Lie” gone, the psychological barrier to revolt is lowered. They must decide how to organize without traditional hierarchies.
- Constraint: While they have truth, they may still lack physical resources (land, weapons).
- The “Truth-Keepers” (System Maintainers):
- Decision: A new class emerges to interpret the massive influx of data.
- Constraint: They are the most dangerous actors, as they might attempt to “contextualize” truth to regain the power of the lie.
3. Potential Outcomes and Likelihood
- The “Glass Feudalism” (High Likelihood): Hierarchies persist but are based on verified merit or brutal, transparent force. If a lord provides protection, the contract is explicit and verified. There is no “noblesse oblige,” only “noblesse contract.”
- Accelerated Scientific Revolution (High Likelihood): Because “Ground Truth” prevents the suppression of heretical facts, the Dark Ages never happen in an intellectual sense. Empirical observation is the only currency.
- The Radicalization of Interpretation (Medium Likelihood): Since the facts are indisputable, conflict shifts entirely to interpretation. “Yes, the King killed that man (Fact), but it was for the greater good (Interpretation).” Politics becomes a war of philosophy rather than a war of secrets.
- Social Stagnation (Low Likelihood): Some argue that “polite lies” are the grease of civilization. Total transparency might lead to constant vendettas and social friction, potentially collapsing society into small, hyper-defensive units.
4. Risks, Opportunities, and Trade-offs
- Risk: The Tyranny of the Record. In a world where no one can “start over,” a single youthful mistake is etched into the Ground Truth forever. There is no “right to be forgotten.”
- Opportunity: Hyper-Efficient Markets. Economic friction vanishes. Credit is based on verified history; fraud is structurally impossible. This could lead to a medieval industrial revolution.
- Trade-off: Privacy vs. Accountability. To have a “Ground Truth” that prevents the Foundational Lie, one must sacrifice the “Private Lie.” Personal privacy becomes a luxury or a relic.
5. Short-term vs. Long-term Implications
- Short-term (1100s–1300s): Massive instability. The collapse of the Papacy and traditional Monarchies. A century of “Truth Wars” as the old guard tries to destroy the system.
- Long-term (1400s–Present): The emergence of a “Glass Civilization.” Governance is likely algorithmic or hyper-parliamentary. The concept of “conspiracy” is non-existent. Humanity reaches a high-tech state much earlier, but perhaps with a colder, more clinical social structure.
6. Assumptions and Uncertainties
- Assumption of Literacy/Access: This scenario assumes that “Ground Truth” is legible to the average person. If only an elite can read the “Ledger,” the Foundational Lie simply migrates to the interpretation of the Ledger.
- The Violence Gap: Truth does not equal power. A tyrant can be a verified tyrant. If he owns the grain and the swords, knowing he is a usurper doesn’t necessarily empower the people to stop him.
- Human Psychology: Can humans live without myths? We are wired for narrative. If the “Foundational Lie” is removed, will humans simply invent “Secondary Myths” that ignore the Ground Truth?
7. Causal Insights: The Role of the Lie
This counterfactual reveals that Mythic Secrecy is the “social glue” of traditional centralization.
- Secrecy as a Scaling Tool: In our history, secrecy allowed leaders to project an image of competence and divinity that scaled beyond their actual abilities. Without it, organizations must remain smaller or become significantly more efficient.
- The Shift from “Who” to “What”: In a Ground Truth world, authority shifts from the Identity of the ruler (The King) to the Action of the ruler (The Policy).
- The Fragility of Truth: The scenario suggests that the “Foundational Lie” is not just a tool of oppression, but a protective layer for social complexity. Removing it requires a massive leap in human cognitive and emotional maturity to prevent the “Truth” from becoming a weapon of universal surveillance and social freezing.
Conclusion: A world without the Foundational Lie is a world without “Magic” (in the metaphorical sense). It is a world of cold, hard accounting. While it prevents the horrors of systemic deception and hidden corruption, it risks creating a society of rigid, unforgiving transparency where the human capacity for reinvention is stifled by an immutable past.
Control Factors (held constant):
- Human desire for power and exclusion
- Economic incentives for competitive advantage
- The existence of complex social and technological structures
Context from Related Files:
counterfactual_op.md
1
2
3
4
5
6
7
8
9
---
transforms: (.+)/content\.md -> $1/counterfactual.md
task_type: CounterfactualAnalysis
---
* Analyze the content through counterfactual reasoning
* Identify key decisions, events, or assumptions and explore alternative outcomes
* Use "what if" scenarios to stress-test claims and reveal hidden dependencies
* Highlight which counterfactuals most significantly change the conclusions
Previous Task Results:
Instructions:
- Compare outcomes across all scenarios
- Identify key differences and their causes
- Assess which factors had the most impact
- Evaluate risks and benefits of each alternative
- Determine which scenario(s) would have been preferable and why
- Identify lessons learned and actionable insights
- Highlight any surprising or counterintuitive findings
- Provide recommendations based on the analysis
```
Comparison Response
This comprehensive comparative analysis examines the Actual Scenario (the evolution of secret knowledge into AI opacity) against four Counterfactual Scenarios that manipulate the variables of interpretability, transparency, memory, and truth.
1. Executive Summary: The Spectrum of Secrecy
The fundamental tension across all scenarios is the trade-off between Systemic Capability and Human Agency.
- In the Actual Scenario, we maximize capability by embracing opacity, creating a “Techno-Priesthood.”
- In the Counterfactuals, we attempt to reclaim agency by imposing constraints on secrecy, often at the cost of technological “magic” or individual privacy.
2. Comparative Matrix of Scenarios
| Scenario | Primary Power Source | Nature of the “Secret” | Social Structure | Innovation Speed |
|---|---|---|---|---|
| Actual | Navigation | Operational Opacity (AI) | Techno-Priesthood | Hyper-Accelerated |
| CF1 (Interpretability) | Persuasion | Non-existent (Capped) | Democratic/Human-Centric | Slow/Incremental |
| CF2 (Radical Transparency) | Execution | Impossible (No Privacy) | Hive-Mind/Collective | Instantaneous |
| CF3 (Perfect Memory) | Synthesis | Visible Debt/Logic | Liquid/Meritocratic | High (No “Tax”) |
| CF4 (Medieval Truth) | Utility | No “Foundational Lies” | Contractual/Clinical | Early Industrial |
3. Key Differences and Their Causes
A. The Nature of the “Barrier”
In the Actual Scenario, the barrier to power is Cognitive Load (the system is too complex to understand). In CF1, the barrier is Regulatory/Physical (the system is forbidden from being complex). In CF2, the barrier is Physical Infrastructure (everyone knows the plan, but who has the factory?).
- Cause: The shift from Information Asymmetry (knowing) to Capability Asymmetry (doing).
B. The Role of the Individual
In CF2 (Radical Transparency), the individual effectively disappears into a collective. In the Actual Scenario, the individual is a “Navigator” or “Shaman.” In CF3 (Perfect Memory), the individual is a “Synthesizer.”
- Cause: The degree to which “Private Thought” is protected as a form of property.
C. The “Complexity Tax”
The Actual Scenario pays a tax in Fragility (if the Navigators leave, the system breaks). CF1 pays a tax in Performance (we lose the benefits of high-dimensional AI). CF3 pays a tax in Documentation Overhead.
4. Impact Factor Analysis: What Moved the Needle?
- Structural Secrecy (Highest Impact): The ability for a system to be “too complex to understand” is the single greatest driver of modern power inequality. Removing this (CF1) fundamentally changes the trajectory of the human race more than any other factor.
- Information Persistence (CF3): Perfect memory eliminates the “Accidental Landlord.” This suggests that much of modern corporate power is not based on talent, but on the entropy of documentation.
- The Foundational Lie (CF4): Removing myth-making (divine right, brand prestige) forces society into a “Cold Reality.” This reveals that human social cohesion is currently dependent on a certain level of “Mythic Secrecy.”
5. Risks, Benefits, and Trade-offs
| Scenario | Major Risk | Major Benefit | Critical Trade-off |
|---|---|---|---|
| Actual | Accountability Vacuum | Maximum Efficiency | Legibility vs. Capability |
| CF1 | Technological Stagnation | Total Human Control | Safety vs. Progress |
| CF2 | Loss of Self/Psychosis | End of Corruption | Privacy vs. Truth |
| CF3 | Analysis Paralysis | True Meritocracy | Speed vs. Memory |
| CF4 | Social Rigidity | Scientific Acceleration | Myth vs. Math |
6. The “Preferable” Scenario
Scenario CF3 (Perfect Institutional Memory) emerges as the most “balanced” alternative.
- Why: Unlike CF1, it doesn’t cap human potential or AI capability; it simply ensures that the path taken to reach that capability is documented and reversible. It eliminates the “Accidental Landlord” (the person who holds a company hostage because only they know how the legacy code works) without destroying the “Private Self” (as in CF2). It promotes a Meritocracy of Synthesis rather than a Priesthood of Obfuscation.
7. Surprising and Counterintuitive Findings
- Transparency is a Vulnerability: In CF1 and CF2, perfect interpretability makes systems trivial to hack. Secrecy, even “feral” technical debt, acts as a biological immune system for organizations.
- The “Magic” of the Lie: CF4 (Medieval Truth) suggests that without the “Foundational Lie,” the Renaissance might have happened earlier, but the “soul” of culture (art, religion, mystery) might have been hollowed out by clinical accounting.
- Complexity as a Moat: In the Actual Scenario, companies intentionally allow technical debt to grow because it creates a barrier to entry that competitors cannot easily replicate, even if they steal the source code.
8. Actionable Insights and Recommendations
- For Organizations (Combatting the Accidental Landlord):
- Invest in “Context Preservation” tools. The goal should be to move toward CF3. If a decision isn’t recorded with its “Why,” it is a future liability.
- For Regulators (Managing AI Opacity):
- Recognize the Interpretability Tax. If you mandate total AI transparency (CF1), you are effectively handicapping your domestic tech industry against rivals who embrace opacity (Actual Scenario).
- For Individuals (The Navigator Skillset):
- In the Actual Scenario, “Analytical” skills are depreciating. The high-value skill of the future is Relational Navigation—the ability to “coax” results out of systems you do not fully understand.
- For Society (The Privacy Threshold):
- Protect the “Ur-Property” of the private mind. CF2 shows that total transparency leads to the death of the individual. We must resist “Radical Transparency” in favor of “Targeted Accountability.”
Final Conclusion
We are currently trending toward the Actual Scenario, where power is a function of navigating a “shifting labyrinth” of AI and technical debt. To avoid the “Black Box Trap,” we should not strive for the impossible “Radical Transparency” of CF2, but rather the “Perfect Memory” of CF3. We must make the complexity visible, even if the mechanics remain beyond human reach. Power should belong to those who can explain the map, not just those who have memorized the turns.
This comprehensive comparative analysis examines the Actual Scenario (the evolution of secret knowledge into AI opacity) against four Counterfactual Scenarios that manipulate the variables of interpretability, transparency, memory, and truth.
1. Executive Summary: The Spectrum of Secrecy
The fundamental tension across all scenarios is the trade-off between Systemic Capability and Human Agency.
- In the Actual Scenario, we maximize capability by embracing opacity, creating a “Techno-Priesthood.”
- In the Counterfactuals, we attempt to reclaim agency by imposing constraints on secrecy, often at the cost of technological “magic” or individual privacy.
2. Comparative Matrix of Scenarios
| Scenario | Primary Power Source | Nature of the “Secret” | Social Structure | Innovation Speed |
|---|---|---|---|---|
| Actual | Navigation | Operational Opacity (AI) | Techno-Priesthood | Hyper-Accelerated |
| CF1 (Interpretability) | Persuasion | Non-existent (Capped) | Democratic/Human-Centric | Slow/Incremental |
| CF2 (Radical Transparency) | Execution | Impossible (No Privacy) | Hive-Mind/Collective | Instantaneous |
| CF3 (Perfect Memory) | Synthesis | Visible Debt/Logic | Liquid/Meritocratic | High (No “Tax”) |
| CF4 (Medieval Truth) | Utility | No “Foundational Lies” | Contractual/Clinical | Early Industrial |
3. Key Differences and Their Causes
A. The Nature of the “Barrier”
In the Actual Scenario, the barrier to power is Cognitive Load (the system is too complex to understand). In CF1, the barrier is Regulatory/Physical (the system is forbidden from being complex). In CF2, the barrier is Physical Infrastructure (everyone knows the plan, but who has the factory?).
- Cause: The shift from Information Asymmetry (knowing) to Capability Asymmetry (doing).
B. The Role of the Individual
In CF2 (Radical Transparency), the individual effectively disappears into a collective. In the Actual Scenario, the individual is a “Navigator” or “Shaman.” In CF3 (Perfect Memory), the individual is a “Synthesizer.”
- Cause: The degree to which “Private Thought” is protected as a form of property.
C. The “Complexity Tax”
The Actual Scenario pays a tax in Fragility (if the Navigators leave, the system breaks). CF1 pays a tax in Performance (we lose the benefits of high-dimensional AI). CF3 pays a tax in Documentation Overhead.
4. Impact Factor Analysis: What Moved the Needle?
- Structural Secrecy (Highest Impact): The ability for a system to be “too complex to understand” is the single greatest driver of modern power inequality. Removing this (CF1) fundamentally changes the trajectory of the human race more than any other factor.
- Information Persistence (CF3): Perfect memory eliminates the “Accidental Landlord.” This suggests that much of modern corporate power is not based on talent, but on the entropy of documentation.
- The Foundational Lie (CF4): Removing myth-making (divine right, brand prestige) forces society into a “Cold Reality.” This reveals that human social cohesion is currently dependent on a certain level of “Mythic Secrecy.”
5. Risks, Benefits, and Trade-offs
| Scenario | Major Risk | Major Benefit | Critical Trade-off |
|---|---|---|---|
| Actual | Accountability Vacuum | Maximum Efficiency | Legibility vs. Capability |
| CF1 | Technological Stagnation | Total Human Control | Safety vs. Progress |
| CF2 | Loss of Self/Psychosis | End of Corruption | Privacy vs. Truth |
| CF3 | Analysis Paralysis | True Meritocracy | Speed vs. Memory |
| CF4 | Social Rigidity | Scientific Acceleration | Myth vs. Math |
6. The “Preferable” Scenario
Scenario CF3 (Perfect Institutional Memory) emerges as the most “balanced” alternative.
- Why: Unlike CF1, it doesn’t cap human potential or AI capability; it simply ensures that the path taken to reach that capability is documented and reversible. It eliminates the “Accidental Landlord” (the person who holds a company hostage because only they know how the legacy code works) without destroying the “Private Self” (as in CF2). It promotes a Meritocracy of Synthesis rather than a Priesthood of Obfuscation.
7. Surprising and Counterintuitive Findings
- Transparency is a Vulnerability: In CF1 and CF2, perfect interpretability makes systems trivial to hack. Secrecy, even “feral” technical debt, acts as a biological immune system for organizations.
- The “Magic” of the Lie: CF4 (Medieval Truth) suggests that without the “Foundational Lie,” the Renaissance might have happened earlier, but the “soul” of culture (art, religion, mystery) might have been hollowed out by clinical accounting.
- Complexity as a Moat: In the Actual Scenario, companies intentionally allow technical debt to grow because it creates a barrier to entry that competitors cannot easily replicate, even if they steal the source code.
8. Actionable Insights and Recommendations
- For Organizations (Combatting the Accidental Landlord):
- Invest in “Context Preservation” tools. The goal should be to move toward CF3. If a decision isn’t recorded with its “Why,” it is a future liability.
- For Regulators (Managing AI Opacity):
- Recognize the Interpretability Tax. If you mandate total AI transparency (CF1), you are effectively handicapping your domestic tech industry against rivals who embrace opacity (Actual Scenario).
- For Individuals (The Navigator Skillset):
- In the Actual Scenario, “Analytical” skills are depreciating. The high-value skill of the future is Relational Navigation—the ability to “coax” results out of systems you do not fully understand.
- For Society (The Privacy Threshold):
- Protect the “Ur-Property” of the private mind. CF2 shows that total transparency leads to the death of the individual. We must resist “Radical Transparency” in favor of “Targeted Accountability.”
Final Conclusion
We are currently trending toward the Actual Scenario, where power is a function of navigating a “shifting labyrinth” of AI and technical debt. To avoid the “Black Box Trap,” we should not strive for the impossible “Radical Transparency” of CF2, but rather the “Perfect Memory” of CF3. We must make the complexity visible, even if the mechanics remain beyond human reach. Power should belong to those who can explain the map, not just those who have memorized the turns.
Counterfactual Analysis Results
Actual Scenario
Secret knowledge functions as the primordial form of property, evolving from deliberate esoteric guilds to emergent ‘feral’ knowledge (technical debt) and finally to operational opacity in AI systems, where power is derived from navigating incomprehensible complexity.
Analysis
This analysis explores the evolution of secret knowledge as a form of property, tracing its trajectory from intentional human exclusion to the emergent, non-human complexity of modern AI systems.
1. Key Elements and Conditions
The scenario rests on the premise that information asymmetry is the foundation of value.
- Knowledge as Property: Unlike physical property, knowledge is non-rivalrous but can be made “excludable” through secrecy. This creates a “Knowledge Monopoly.”
- The Three-Stage Evolution:
- Esoteric Guilds (Deliberate): Human-to-human secrecy (e.g., trade secrets, alchemy, priesthoods).
- Feral Knowledge (Technical Debt): Knowledge that “escapes” human documentation. It is the “ghost in the machine” of legacy code—unintended complexity that requires specialized “shamanic” intervention to maintain.
- Operational Opacity (AI): Knowledge generated by non-human heuristics. The “secret” is no longer a hidden formula but a multi-dimensional weight map that no human mind can hold.
- The Complexity Premium: Power is no longer held by those who own the tools, but by those who can navigate the incomprehensible state-space of those tools.
2. Main Actors, Decisions, and Constraints
- The Gatekeepers (Historical): Guild masters and corporations who decide what is “Proprietary.” Their constraint is the “leaky” nature of human secrets (espionage, defection).
- The Maintainers (Transitional): Software engineers and systems architects dealing with “feral” systems. Their decision is often a trade-off: Speed of deployment vs. Legibility. Choosing speed creates technical debt, which functions as a barrier to entry for competitors.
- The Navigators (Modern/Future): AI researchers and “Prompt Engineers” who do not understand the why of a system but have developed an intuitive “feel” for the how.
- Constraints:
- Cognitive Load: The human brain cannot scale with the complexity of feral or AI knowledge.
- Entropy: As systems grow, the “secret” part (the part no one understands) naturally increases.
3. Potential Outcomes and Likelihood
- The “Techno-Priesthood” (High Likelihood): A small class of individuals who possess the “knack” for navigating opaque systems becomes indispensable. They do not use logic; they use ritualized interaction with the AI/System.
- Systemic Fragility (Medium Likelihood): As knowledge becomes “feral,” the loss of a few key “Navigators” could lead to the collapse of critical infrastructure that no one knows how to rebuild from scratch.
- The End of “Open Source” Utility (Low Likelihood): Even if code is open, if the complexity is high enough, the “openness” is an illusion. The “secret” is the emergent behavior, not the source code.
4. Risks, Opportunities, and Trade-offs
- Risk: The “Black Box” Trap. We become dependent on systems (economic, medical, judicial) whose decision-making logic is a “secret” even to its creators. This leads to accountability vacuums.
- Opportunity: Hyper-Efficiency. Opaque AI systems can find patterns humans would never see. By abandoning the need for “understanding,” we unlock performance levels previously thought impossible.
- Trade-off: Legibility vs. Capability. To make a system understandable (legible) is to limit its complexity. To maximize capability is to embrace opacity.
5. Short-term and Long-term Implications
- Short-term: Companies will continue to prioritize “shipping” over “documenting,” accelerating the growth of feral knowledge (technical debt) as a competitive moat.
- Long-term: A fundamental shift in the definition of “Expertise.” Expertise will move from Analytical (breaking things down) to Relational (knowing how to coax a result out of a complex system).
6. Assumptions and Uncertainties
- Assumption: That complexity will continue to outpace human cognitive evolution.
- Uncertainty: Explainable AI (XAI). If we develop tools that can perfectly translate AI “thought” into human logic, the “Operational Opacity” stage may be bypassed or reversed.
- Uncertainty: Regulatory Intervention. Will governments mandate “Right to Understand” laws, forcing systems to remain simple enough for human audit?
7. Causal Relationships: The “Complexity Trap”
The scenario reveals a feedback loop:
- Competition drives the need for Advantage.
- Advantage is found in Complexity (which is harder to copy).
- Complexity leads to Opacity (Feral/AI knowledge).
- Opacity creates a New Property Class (those who can navigate the opacity).
- This class protects their status by Increasing Complexity, restarting the cycle.
8. Counterfactual Analysis (Stress-Testing)
Using the counterfactual_op.md framework, we can test the stability of this scenario:
- What if “Feral Knowledge” (Technical Debt) was eliminated by automated refactoring?
- Result: The transition to AI Opacity would be even more jarring. We would move from “Perfectly Legible” systems to “Completely Opaque” AI without the intermediate step of “messy” human systems. The “Techno-Priesthood” would emerge as a sudden disruption rather than a gradual evolution.
- What if the “Human Desire for Power” was replaced by a “Radical Transparency” incentive?
- Result: If economic rewards favored simplicity over performance, we would see a “Complexity Ceiling.” Innovation would slow down, but systems would be incredibly robust and democratic. Power would shift back to those with the best logic, not the best intuition.
- What if AI systems become “Self-Explaining”?
- Result: This destroys the “Secret Knowledge” property. If the AI can tell anyone how it works, the “Navigator” class loses its monopoly. Knowledge property would revert to its primordial form: Compute Power and Data Ownership.
Final Insight
The evolution of secret knowledge suggests that we are moving from an era of “Knowledge as Content” to “Knowledge as Navigation.” In the guild era, the secret was a recipe. In the AI era, the secret is the map of a shifting labyrinth. Power belongs to the one who doesn’t get lost.
Counterfactual Scenario 1
What if ‘Structural Secrecy’ was impossible because all complex systems (AI, financial algorithms) were required by physical law or design to be perfectly human-interpretable?
Analysis
This analysis explores a counterfactual world where Structural Secrecy—the phenomenon where the complexity of a system inherently obscures its inner workings—is non-existent. In this world, every deep neural network, high-frequency trading algorithm, and bureaucratic hierarchy is as transparent and understandable as a simple mechanical lever.
1. Key Elements and Conditions
- The Interpretability Mandate: Whether by physical law (a universe where complexity requires legibility) or a foundational design protocol, no system can function unless its logic is “human-readable.”
- The End of the “Black Box”: The concept of emergent behavior that cannot be traced back to specific, understandable inputs and weights is gone.
- Cognitive Parity: For this to work, either human cognitive capacity has expanded to meet the complexity of the world, or (more likely) the complexity of technology is capped at the threshold of human comprehension.
- Universal Auditability: Every decision made by a machine or a large organization carries an “epistemic trail” that any observer can follow to understand why a decision was made.
2. Main Actors, Decisions, and Constraints
- AI Researchers/Engineers: They no longer “train” models and hope for the best. They must “author” logic. The decision-space shifts from optimization (finding what works) to architecture (building what can be explained).
- Corporations: The primary constraint is the loss of “Proprietary Complexity.” Companies can no longer hide predatory pricing or biased hiring behind “the algorithm.”
- Regulators: Their role shifts from forensic investigation to real-time monitoring. They don’t need to subpoena code; they simply look at the system.
- The Individual: Citizens gain “Epistemic Agency.” They are no longer subjects of opaque systems but can interrogate the logic of their credit scores, medical diagnoses, and social feeds.
3. Potential Outcomes and Likelihood
A. The “Complexity Ceiling” (High Likelihood)
If every system must be interpretable, we likely hit a wall in technological advancement. Modern AI (LLMs, protein folding) relies on high-dimensional patterns that the human brain cannot naturally process.
- Outcome: We might lose the most powerful “miracles” of AI in exchange for total control. Progress becomes slower, more incremental, and strictly logical.
B. The Death of Algorithmic Rent-Seeking (High Likelihood)
Financial markets currently thrive on “structural secrecy” (e.g., dark pools, HFT).
- Outcome: If every trade’s logic is transparent, “alpha” (market-beating edge) based on obfuscation disappears. Markets become more stable but perhaps less liquid, as the incentive to “out-smart” the system via complexity vanishes.
C. Radical Political Accountability (Medium Likelihood)
Bureaucracies often use complexity to hide responsibility (the “no one’s fault” defense).
- Outcome: In a world of perfect interpretability, the “paper trail” is a “logic trail.” Corruption becomes nearly impossible to hide because the intent behind a policy shift is visible in the system’s design.
4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity |
|---|---|---|
| Security | The “Glass House” Vulnerability: If a system is perfectly interpretable to a user, it is perfectly interpretable to a hacker. Finding exploits becomes trivial. | Perfect Verification: We can prove a system is safe before turning it on. |
| Innovation | The Interpretability Tax: Massive amounts of energy/compute are wasted making things “simple” for humans rather than “efficient” for the task. | Democratization: Anyone can understand and modify technology, ending the priesthood of high-tech elites. |
| Social | The End of Privacy: If “complex systems” include the human brain (via BCI), our inner thoughts become “structurally transparent” to others. | Total Trust: Social friction decreases because “hidden agendas” are structurally impossible to maintain. |
5. Short-term and Long-term Implications
Short-term:
- Economic Chaos: The valuation of tech giants collapses as their “black box” advantages are neutralized.
- Scientific Pivot: A massive shift from “Discovery by Observation” (watching what the AI finds) to “Discovery by Construction” (building only what we understand).
Long-term:
- A “Human-Centric” Civilization: Technology stops being an alien force acting upon us and becomes a literal extension of human intent.
- Stagnation vs. Stability: We may live in a “slower” world, but one free from systemic collapses (like the 2008 financial crisis) caused by misunderstood complexity.
6. Assumptions and Uncertainties
- The Definition of “Human”: Does “human-interpretable” mean interpretable by an average person, or a specialist? If it’s the latter, structural secrecy might just migrate from the system to the expert class.
- The Nature of Intelligence: This scenario assumes that “intelligence” can exist without “unfathomable complexity.” If true intelligence requires high-dimensional opacity, then this counterfactual describes a world where AGI is impossible.
- The Adversarial Response: If structural secrecy is impossible, will humans invent new forms of linguistic or social secrecy to maintain power?
7. Causal Relationships: The “Transparency Loop”
In our current world, Complexity → Secrecy → Power Concentration → More Complexity. In the counterfactual world, the loop is broken:
- Requirement of Interpretability → Limits the scale of autonomous systems.
- Limited Scale → Increases human oversight.
- Increased Oversight → Reduces the “Power Gap” between those who own the systems and those who use them.
- Reduced Power Gap → Leads to a more egalitarian, albeit potentially less “advanced,” society.
Final Insight
The removal of Structural Secrecy acts as a “Complexity Tax” on Power. In our world, power is often gained by mastering or owning what others cannot understand. If understanding is a prerequisite for existence, power becomes a function of persuasion and clarity rather than obfuscation and scale. The world becomes safer and more just, but it may lose the “emergent magic” that allows systems to solve problems beyond the reach of the individual human mind.
Counterfactual Scenario 2
What if the ‘Ur-property’ of secrecy was abolished by a ‘Radical Transparency’ technology (e.g., universal telepathy or perfect surveillance) that made withholding information impossible?
Analysis
This analysis explores a world where the “Ur-property” of secrecy—the foundational ability to withhold information—is eliminated by Radical Transparency (RT). Whether through biological telepathy or an inescapable technological surveillance layer, the “private room” of the human mind and the “black box” of organizational strategy have been forcibly opened.
1. Key Elements and Conditions
- The End of Information Asymmetry: The fundamental driver of markets, negotiations, and social hierarchies—knowing something someone else doesn’t—evaporates.
- The Death of the “Inner Sanctum”: The distinction between public persona and private thought vanishes.
- Involuntary Veracity: Truth is no longer a moral choice but a structural necessity. Lying becomes impossible because the “signal” of the truth is always available to the observer.
- Universal Access: For this scenario to be “Radical,” the transparency must be bidirectional (the governed see the governors) or universal (everyone sees everyone).
2. Main Actors, Decisions, and Constraints
- Individuals: Must decide how to process the “noise” of everyone else’s thoughts/data. The constraint is psychological bandwidth and the trauma of losing the ego’s protective shell.
- States/Governments: Lose the ability to conduct “black ops,” secret diplomacy, or classified research. The constraint is the sudden obsolescence of national security frameworks.
- Corporations: Lose Intellectual Property (IP), trade secrets, and “first-mover” advantages based on hidden R&D.
- The “Architects” (if technological): Those who maintain the RT infrastructure. They face the ultimate “Who watches the watchers?” dilemma, unless the technology is decentralized/biological.
3. Potential Outcomes and Likelihood
A. The Great Social Collapse (High Likelihood - Short Term)
Social cohesion relies heavily on “pro-social lying” and tact. If every fleeting thought of resentment, lust, or judgment is public, existing social structures (marriages, friendships, workplace hierarchies) would likely shatter instantly.
- Outcome: Mass isolation or violent conflict as people react to the “unfiltered” reality of others.
B. The Hive-Mind Evolution (Medium Likelihood - Long Term)
To survive the psychological onslaught, humanity might evolve a “collective consciousness.” If you can feel everyone’s pain and see their justifications, empathy might scale to a point where “the other” ceases to exist.
- Outcome: A post-conflict society where resource allocation is optimized for the whole, but individual agency is diminished.
C. The Meritocracy of Execution (High Likelihood - Economic)
Since no one can hide a “better mousetrap” design, competition shifts from innovation-hoarding to execution-speed.
- Outcome: Rapid technological acceleration. If a cure for cancer is thought of by one person, the world has it instantly. Economic value shifts from “owning the idea” to “owning the physical infrastructure to build it.”
4. Risks, Opportunities, and Trade-offs
| Feature | Risk | Opportunity | Trade-off |
|---|---|---|---|
| Governance | Totalitarian “Thought Police” (if centralized). | Total elimination of corruption and graft. | Security vs. Autonomy. |
| Innovation | No incentive to invest in R&D if it’s instantly stolen. | Global “Open Source” everything; no redundant research. | Profit vs. Progress. |
| Psychology | Mass psychosis, loss of “self,” chronic vulnerability. | Radical empathy; end of loneliness and misunderstanding. | Privacy vs. Connection. |
5. Short-term vs. Long-term Implications
- Short-term (0-5 years): The “Transparency Shock.” Economic markets crash as insider information becomes “just information.” Political regimes fall as citizens see the true intentions of leaders. High rates of psychological trauma.
- Long-term (50+ years): The “New Equilibrium.” A new language of “Radical Honesty” develops. Humans become “radically boring” or “radically accepting.” The concept of “shame” likely disappears, as shame requires a secret to fester.
6. Assumptions and Uncertainties
- Assumption of Bandwidth: Can the human brain actually process universal transparency? Or would we simply “tune out” 99% of the data, effectively recreating secrecy through sheer noise?
- Uncertainty of Power: Does transparency actually disempower the powerful? History suggests that even when we know leaders are corrupt, power dynamics often persist through force rather than deception.
- The “Motive” Gap: Knowing what someone is thinking doesn’t always explain why. Misinterpretation of transparent data could lead to new forms of conflict.
7. Causal Relationships: The “Ur-Property” Chain
- Secrecy $\rightarrow$ Identity: By removing secrecy, you break the boundary of the “Self.” If there is no part of me that is only mine, the “I” becomes “We.”
- Secrecy $\rightarrow$ Value: Scarcity of information creates value. Radical transparency creates “Information Hyper-inflation,” where data is infinite and free, potentially collapsing all information-based economies.
- Secrecy $\rightarrow$ Strategy: Strategy is the art of the hidden move. Without it, “strategy” becomes “optimization.” You don’t outmaneuver an opponent; you simply out-compute them in a race of pure efficiency.
Final Insight
The abolition of secrecy is the abolition of the Strategic Actor. In a world of Radical Transparency, the “Game” (as defined by Game Theory) changes from a Non-Cooperative Game with Imperfect Information to a Cooperative Game with Perfect Information. While this might end war and corruption, it likely ends the “Individual” as understood in Western liberal tradition, replacing it with a biological or digital collective. The cost of total truth is the loss of the private self.
Counterfactual Scenario 3
What if institutional memory was perfect and ‘Technical Debt’ never became ‘Feral Knowledge,’ preventing the rise of the ‘Accidental Landlord’?
Analysis
This analysis explores a counterfactual world where Institutional Memory is perfect, Technical Debt is always transparent (never becoming “Feral Knowledge”), and the “Accidental Landlord”—those who derive power from being the sole keepers of legacy complexity—never emerges.
1. Key Elements and Conditions
In this scenario, the fundamental “entropy” of information is halted. The following conditions exist:
- Universal Context Preservation: Every decision, hack, and “temporary fix” is recorded with its original intent, constraints, and expiration date.
- Debt Legibility: Technical debt is treated like a financial ledger. It is visible to all stakeholders, not just the engineers. It never “goes feral” (losing its documentation and becoming a mysterious black box).
- The Death of Tribalism: Knowledge does not reside in the heads of “the veterans” but in a shared, accessible, and perfectly indexed substrate.
- Automated Auditing: Systems automatically flag when a temporary solution has outlived its context, preventing the “sedimentation” of legacy code.
2. Main Actors, Decisions, and Constraints
The Actors:
- The Engineer: No longer a “wizard” or “firefighter.” Their value shifts from knowing where the bodies are buried to architectural creativity.
- The Manager: Operates with high-fidelity data. They can no longer be “held hostage” by a single developer who is the only one who understands the legacy system.
- The Organization: Becomes a “Ship of Theseus” that can replace any part of itself without losing its soul or operational logic.
- The Displaced “Accidental Landlord”: Individuals who previously gained job security and status through “gatekeeping” complexity find their social capital evaporated.
Key Decisions:
- The “Pay Now or Pay Later” Mandate: Because debt is visible, the decision to incur it is a formal business agreement, not a quiet engineering shortcut.
- Radical Transparency: Organizations must decide to prioritize documentation and “memory hygiene” over the raw speed of “shipping it.”
Constraints:
- Cognitive Load: Even if memory is perfect, human bandwidth is not. The constraint shifts from finding information to processing the sheer volume of perfect history.
- The “Rigidity Trap”: Perfect memory might make it harder to pivot if the organization feels “haunted” by its past decisions.
3. Potential Outcomes and Likelihood
- Hyper-Fluidity (High Likelihood): Employee turnover no longer causes “brain drain.” A new hire can become as effective as a 10-year veteran in days because the “why” behind every system is instantly queryable.
- The End of the “Legacy System” (Moderate Likelihood): Systems are continuously refactored because the cost of doing so is known and the risks are mapped. We no longer see 40-year-old COBOL systems that “no one dares touch.”
- Shift in Power Dynamics (High Likelihood): Power moves from Knowledge Hoarders (those who know the system) to Synthesisers (those who can use the system to create new value).
4. Risks, Opportunities, and Trade-offs
Risks:
- The Panopticon Effect: Perfect memory means every mistake is preserved forever. This could lead to “Analysis Paralysis” or a culture of extreme risk aversion.
- Loss of “Productive Forgetting”: Sometimes, forgetting old constraints is how innovation happens. Perfect memory might tether an organization to obsolete paradigms.
Opportunities:
- Massive Efficiency Gains: Estimates suggest engineers spend 30-50% of their time just trying to understand existing code. Eliminating this “comprehension tax” would double global R&D output.
- True Meritocracy: Without “feral knowledge” to hide behind, performance is measured by actual contribution rather than proximity to critical, mysterious systems.
Trade-offs:
- Speed vs. Legibility: The initial “velocity” of a project might be slower because the “memory overhead” (documenting intent) is non-negotiable.
5. Short-term vs. Long-term Implications
- Short-term: A period of “The Great Unmasking.” Many senior leaders and engineers whose value was tied to “knowing the mess” will be exposed as having few other skills. Organizational restructuring would be rampant.
- Long-term: The emergence of “Liquid Organizations.” Companies could merge, split, and reorganize with the ease of software modules because their internal logic is perfectly transparent and modular.
6. Assumptions and Uncertainties
- Assumption: We assume that “Perfect Memory” is technologically and cognitively possible (perhaps via AI-mediated neural indexing).
- Uncertainty: How does the “Human Desire for Power” (a Control Factor) adapt? If you can’t hoard knowledge, do people start hoarding “Compute” or “Social Influence” instead?
- Uncertainty: Does the removal of “Technical Debt” actually lead to better products, or does the friction of debt actually serve as a natural filter for which features are truly worth maintaining?
7. Causal Relationships: The “Anti-Landlord” Cycle
- Perfect Memory $\rightarrow$ Eliminates Information Asymmetry.
- No Information Asymmetry $\rightarrow$ Technical Debt is a Choice, not a Secret.
- Transparent Debt $\rightarrow$ Prevents “Feral Knowledge” (undocumented complexity).
- No Feral Knowledge $\rightarrow$ No “Accidental Landlord” (power through gatekeeping).
- No Accidental Landlord $\rightarrow$ Power is redistributed to those who provide the most current value, rather than those who have the longest tenure.
Final Insight
In this counterfactual, the “Accidental Landlord” is replaced by the “Agile Architect.” The primary competitive advantage shifts from Retention of the Past to Velocity of the Future. However, the “Control Factor” of human nature suggests that new forms of exclusion would emerge—likely based on who controls the algorithms that filter the perfect memory, rather than the memory itself. The “Landlord” doesn’t disappear; they just move from the “Basement” (Legacy Code) to the “Penthouse” (The Interface).
Counterfactual Scenario 4
What if ‘Mythic Secrecy’ (the foundational lie) was structurally impossible due to a decentralized, immutable ‘Ground Truth’ verification system available to all citizens since the medieval era?
Analysis
This analysis explores a world where the “Foundational Lie”—the strategic use of secrecy, myth-making, and information asymmetry to maintain power—is rendered impossible by a decentralized, immutable “Ground Truth” system established in the medieval era.
1. Key Elements and Conditions
The core of this scenario is the “Universal Ledger of Reality.” Imagine a system (whether based on precursor technology, a unique physical law, or a pervasive “magical” field) that functions as a decentralized, public record of events, transactions, and lineages.
- Immutability: Once an event is recorded (e.g., a king’s decree, a murder, a debt), it cannot be erased or altered by any authority.
- Decentralization: No single church, state, or guild controls the “nodes” of this truth. Access is a birthright, perhaps through “Truth Stones” in every village square or a mental interface.
- The Death of Mythic Secrecy: The “Foundational Lie”—the idea that leaders possess divine blood, secret knowledge, or a mandate from a hidden god—cannot survive. If a King claims divine right, but the Ledger shows his grandfather was a common thief who murdered the previous lord, the myth collapses instantly.
2. Main Actors, Decisions, and Constraints
- The Nobility/Elite:
- Decision: They cannot rule through “prestige” or “divine mystery.” They must pivot to Rule by Utility.
- Constraint: They are subject to the same transparency as peasants. Corruption is visible in real-time.
- The Clergy/Ideologues:
- Decision: Religion must shift from “Faith in the Unseen” to “Ethics of the Seen.”
- Constraint: Dogma that contradicts the Ground Truth is discarded. The Church becomes a judicial body rather than a mystical one.
- The Peasantry/Citizens:
- Decision: With the “Foundational Lie” gone, the psychological barrier to revolt is lowered. They must decide how to organize without traditional hierarchies.
- Constraint: While they have truth, they may still lack physical resources (land, weapons).
- The “Truth-Keepers” (System Maintainers):
- Decision: A new class emerges to interpret the massive influx of data.
- Constraint: They are the most dangerous actors, as they might attempt to “contextualize” truth to regain the power of the lie.
3. Potential Outcomes and Likelihood
- The “Glass Feudalism” (High Likelihood): Hierarchies persist but are based on verified merit or brutal, transparent force. If a lord provides protection, the contract is explicit and verified. There is no “noblesse oblige,” only “noblesse contract.”
- Accelerated Scientific Revolution (High Likelihood): Because “Ground Truth” prevents the suppression of heretical facts, the Dark Ages never happen in an intellectual sense. Empirical observation is the only currency.
- The Radicalization of Interpretation (Medium Likelihood): Since the facts are indisputable, conflict shifts entirely to interpretation. “Yes, the King killed that man (Fact), but it was for the greater good (Interpretation).” Politics becomes a war of philosophy rather than a war of secrets.
- Social Stagnation (Low Likelihood): Some argue that “polite lies” are the grease of civilization. Total transparency might lead to constant vendettas and social friction, potentially collapsing society into small, hyper-defensive units.
4. Risks, Opportunities, and Trade-offs
- Risk: The Tyranny of the Record. In a world where no one can “start over,” a single youthful mistake is etched into the Ground Truth forever. There is no “right to be forgotten.”
- Opportunity: Hyper-Efficient Markets. Economic friction vanishes. Credit is based on verified history; fraud is structurally impossible. This could lead to a medieval industrial revolution.
- Trade-off: Privacy vs. Accountability. To have a “Ground Truth” that prevents the Foundational Lie, one must sacrifice the “Private Lie.” Personal privacy becomes a luxury or a relic.
5. Short-term vs. Long-term Implications
- Short-term (1100s–1300s): Massive instability. The collapse of the Papacy and traditional Monarchies. A century of “Truth Wars” as the old guard tries to destroy the system.
- Long-term (1400s–Present): The emergence of a “Glass Civilization.” Governance is likely algorithmic or hyper-parliamentary. The concept of “conspiracy” is non-existent. Humanity reaches a high-tech state much earlier, but perhaps with a colder, more clinical social structure.
6. Assumptions and Uncertainties
- Assumption of Literacy/Access: This scenario assumes that “Ground Truth” is legible to the average person. If only an elite can read the “Ledger,” the Foundational Lie simply migrates to the interpretation of the Ledger.
- The Violence Gap: Truth does not equal power. A tyrant can be a verified tyrant. If he owns the grain and the swords, knowing he is a usurper doesn’t necessarily empower the people to stop him.
- Human Psychology: Can humans live without myths? We are wired for narrative. If the “Foundational Lie” is removed, will humans simply invent “Secondary Myths” that ignore the Ground Truth?
7. Causal Insights: The Role of the Lie
This counterfactual reveals that Mythic Secrecy is the “social glue” of traditional centralization.
- Secrecy as a Scaling Tool: In our history, secrecy allowed leaders to project an image of competence and divinity that scaled beyond their actual abilities. Without it, organizations must remain smaller or become significantly more efficient.
- The Shift from “Who” to “What”: In a Ground Truth world, authority shifts from the Identity of the ruler (The King) to the Action of the ruler (The Policy).
- The Fragility of Truth: The scenario suggests that the “Foundational Lie” is not just a tool of oppression, but a protective layer for social complexity. Removing it requires a massive leap in human cognitive and emotional maturity to prevent the “Truth” from becoming a weapon of universal surveillance and social freezing.
Conclusion: A world without the Foundational Lie is a world without “Magic” (in the metaphorical sense). It is a world of cold, hard accounting. While it prevents the horrors of systemic deception and hidden corruption, it risks creating a society of rigid, unforgiving transparency where the human capacity for reinvention is stifled by an immutable past.
Comparative Analysis
This comprehensive comparative analysis examines the Actual Scenario (the evolution of secret knowledge into AI opacity) against four Counterfactual Scenarios that manipulate the variables of interpretability, transparency, memory, and truth.
1. Executive Summary: The Spectrum of Secrecy
The fundamental tension across all scenarios is the trade-off between Systemic Capability and Human Agency.
- In the Actual Scenario, we maximize capability by embracing opacity, creating a “Techno-Priesthood.”
- In the Counterfactuals, we attempt to reclaim agency by imposing constraints on secrecy, often at the cost of technological “magic” or individual privacy.
2. Comparative Matrix of Scenarios
| Scenario | Primary Power Source | Nature of the “Secret” | Social Structure | Innovation Speed |
|---|---|---|---|---|
| Actual | Navigation | Operational Opacity (AI) | Techno-Priesthood | Hyper-Accelerated |
| CF1 (Interpretability) | Persuasion | Non-existent (Capped) | Democratic/Human-Centric | Slow/Incremental |
| CF2 (Radical Transparency) | Execution | Impossible (No Privacy) | Hive-Mind/Collective | Instantaneous |
| CF3 (Perfect Memory) | Synthesis | Visible Debt/Logic | Liquid/Meritocratic | High (No “Tax”) |
| CF4 (Medieval Truth) | Utility | No “Foundational Lies” | Contractual/Clinical | Early Industrial |
3. Key Differences and Their Causes
A. The Nature of the “Barrier”
In the Actual Scenario, the barrier to power is Cognitive Load (the system is too complex to understand). In CF1, the barrier is Regulatory/Physical (the system is forbidden from being complex). In CF2, the barrier is Physical Infrastructure (everyone knows the plan, but who has the factory?).
- Cause: The shift from Information Asymmetry (knowing) to Capability Asymmetry (doing).
B. The Role of the Individual
In CF2 (Radical Transparency), the individual effectively disappears into a collective. In the Actual Scenario, the individual is a “Navigator” or “Shaman.” In CF3 (Perfect Memory), the individual is a “Synthesizer.”
- Cause: The degree to which “Private Thought” is protected as a form of property.
C. The “Complexity Tax”
The Actual Scenario pays a tax in Fragility (if the Navigators leave, the system breaks). CF1 pays a tax in Performance (we lose the benefits of high-dimensional AI). CF3 pays a tax in Documentation Overhead.
4. Impact Factor Analysis: What Moved the Needle?
- Structural Secrecy (Highest Impact): The ability for a system to be “too complex to understand” is the single greatest driver of modern power inequality. Removing this (CF1) fundamentally changes the trajectory of the human race more than any other factor.
- Information Persistence (CF3): Perfect memory eliminates the “Accidental Landlord.” This suggests that much of modern corporate power is not based on talent, but on the entropy of documentation.
- The Foundational Lie (CF4): Removing myth-making (divine right, brand prestige) forces society into a “Cold Reality.” This reveals that human social cohesion is currently dependent on a certain level of “Mythic Secrecy.”
5. Risks, Benefits, and Trade-offs
| Scenario | Major Risk | Major Benefit | Critical Trade-off |
|---|---|---|---|
| Actual | Accountability Vacuum | Maximum Efficiency | Legibility vs. Capability |
| CF1 | Technological Stagnation | Total Human Control | Safety vs. Progress |
| CF2 | Loss of Self/Psychosis | End of Corruption | Privacy vs. Truth |
| CF3 | Analysis Paralysis | True Meritocracy | Speed vs. Memory |
| CF4 | Social Rigidity | Scientific Acceleration | Myth vs. Math |
6. The “Preferable” Scenario
Scenario CF3 (Perfect Institutional Memory) emerges as the most “balanced” alternative.
- Why: Unlike CF1, it doesn’t cap human potential or AI capability; it simply ensures that the path taken to reach that capability is documented and reversible. It eliminates the “Accidental Landlord” (the person who holds a company hostage because only they know how the legacy code works) without destroying the “Private Self” (as in CF2). It promotes a Meritocracy of Synthesis rather than a Priesthood of Obfuscation.
7. Surprising and Counterintuitive Findings
- Transparency is a Vulnerability: In CF1 and CF2, perfect interpretability makes systems trivial to hack. Secrecy, even “feral” technical debt, acts as a biological immune system for organizations.
- The “Magic” of the Lie: CF4 (Medieval Truth) suggests that without the “Foundational Lie,” the Renaissance might have happened earlier, but the “soul” of culture (art, religion, mystery) might have been hollowed out by clinical accounting.
- Complexity as a Moat: In the Actual Scenario, companies intentionally allow technical debt to grow because it creates a barrier to entry that competitors cannot easily replicate, even if they steal the source code.
8. Actionable Insights and Recommendations
- For Organizations (Combatting the Accidental Landlord):
- Invest in “Context Preservation” tools. The goal should be to move toward CF3. If a decision isn’t recorded with its “Why,” it is a future liability.
- For Regulators (Managing AI Opacity):
- Recognize the Interpretability Tax. If you mandate total AI transparency (CF1), you are effectively handicapping your domestic tech industry against rivals who embrace opacity (Actual Scenario).
- For Individuals (The Navigator Skillset):
- In the Actual Scenario, “Analytical” skills are depreciating. The high-value skill of the future is Relational Navigation—the ability to “coax” results out of systems you do not fully understand.
- For Society (The Privacy Threshold):
- Protect the “Ur-Property” of the private mind. CF2 shows that total transparency leads to the death of the individual. We must resist “Radical Transparency” in favor of “Targeted Accountability.”
Final Conclusion
We are currently trending toward the Actual Scenario, where power is a function of navigating a “shifting labyrinth” of AI and technical debt. To avoid the “Black Box Trap,” we should not strive for the impossible “Radical Transparency” of CF2, but rather the “Perfect Memory” of CF3. We must make the complexity visible, even if the mechanics remain beyond human reach. Power should belong to those who can explain the map, not just those who have memorized the turns.
Analysis Complete
